1. Introduction
Performance of transmission control protocol (TCP) for wireless ad hoc networks (WANETs) is an active area of research and it has received a lot of attention for its applicability in military operations, disaster rescue missions and other civilian applications. TCP performs well in wired environment where packet losses are mainly due to congestion in the network, but in case of WANETs, a marked degradation in the performance of TCP has been shown, where packet losses are due to channel errors or link failures between mobile nodes [1] . The main reason is the inability of TCP to distinguish the various causes of packet losses. The newer versions of TCP, such as Tahoe, Reno and New Reno [2] also exhibit similar properties [3] .
A number of transport layer protocols have been proposed in the literature [1] [4] -[9] to enhance TCP’s performance in mobile ad hoc environments. However, it may be noted that when a packet drop occurs, most of the protocols are unable to detect the actual reason of packet loss (congestion, link failure, lossy channels or high bit error rates). In WANET, due to dynamic nature of the network and variable number hops between source and destination, the fairness and efficiency get degraded. It is also seen that the existing protocols are not good enough in setting its parameters like congestion window, congestion window limit, round trip time and the retransmission timeout timers.
The existing transport layer protocols lack certain protection from dynamic internal and external malicious activities and hence relies on separate security mechanisms. Existing secure routing protocols though ensure the correctness of the route discovery, may not provide secure end-to-end data delivery at transport layer. The major security threats [10] associated with transport layer protocols in WANET are such as SYN flooding, session hijacking and ACK storm. Therefore, following are some important goals required to be met while designing a transport layer protocol for wireless ad hoc networks: a) Maximizing the throughput per connection; b) Providing both reliable and unreliable connections as per the requirements of application layer; c) Providing adaptability to the dynamics of the network such as rapid change in topology and changes in the nature of wireless links; d) Utilizing available bandwidth efficiently; e) Handling resources such as battery power and buffer sizes efficiently in resource-constraint environment; f) Proper utilization of information from the lower layers of the protocol stack to improve network throughput; g) Maintaining end-to-end semantics; and h) Considering the security aspects as regards WANETs to make itself complete and self-sufficient.
In this paper, we have modified New Reno protocol for wireless ad hoc networks so that it can take care of the above issues. We call this modified protocol as Secure and Adaptive TCP (SA-TCP) and present the proposed protocol in Section 4. The proposed protocol while in operation utilizes the feedback from the network layer so that it can detect different types of packet losses and act accordingly. It also dynamically adapts the parameters (e.g., congestion window, congestion window limit) according to the conditions of the dynamic network, which in turn reduces the chances of congestion and MAC layer collisions in the network. This increases the network throughput and the performance is enhanced significantly. Further, SA-TCP uses an identity based public key cryptography that does not require a trusted third party, which is absent in wireless ad hoc networks. It generates a session secret key on-fly between source-destination nodes to make the three-way handshaking process secure. This proposed security mechanism incurs less overhead as it does not need a certificate for the purpose of authentication.
Paper Overview: The rest of the paper is organized as follows: the related work in enhancing and securing the transport layer protocols is presented in Section 2. In Section 3 we present the system model that is followed in this paper, which is followed by Section 4, wherein the proposed secure and adaptive transmission control protocol is presented. Section 5 shows the simulation results, and finally, conclusions of the paper are given in Section 6.
2. Related Work
A number of protocols have been proposed in the literature [1] [4] -[9] [11] to enhance the performance of transport layer in wireless ad hoc networks. These existing transport layer protocols can be classified into layered and cross layer approaches [12] . Under layered approach, a protocol works independently at a particular layer of OSI model. Under cross layer approach, the protocol works by interacting between two layers. The proposed SA-TCP presented in this paper utilizes transport layer and network layer, and therefore it falls under cross layer approach. TCP DOOR [13] and fixed RTO [14] are under layered approach, whereas, ELFN [1] , TCP-F [4] , TCP-BuS [9] , ATCP [8] and P-TCP [11] are under cross layer approach. In the following paragraphs, we present the cross layer approaches used to design/enhance transport layer for wireless ad hoc networks.
Explicit Link Failure Notification (ELFN) [1] sends a route error message of DSR protocol to notify link failure to the source node. On receiving the route error message, the source node stops the congestion control mechanism and goes into a standby mode. Once the route is re-established, the source node restarts the data transmission with the same congestion window size and RTO timer as was at the time of link failure. This may either lead to more congestion in the new route giving low throughput or inefficient utilization of bandwidth. TCB-Bus [9] is another protocol that works similar way as ELFN. Additionally, it buffers of packets at the intermediate node, named Pivoting Node (PN), which detects the link failure on an active route. The downside of this protocol is that PN has to drop all buffered packets whenever the PN fails to find a new partial route to the destination.
Chandran et al. proposed TCP-F [4] that utilizes network layer feedback from intermediate nodes for de- tecting link failures in wireless ad hoc networks. On detecting a link failure by an intermediate node, a route failure notification (RFN) message is sent back to the source node. On receiving the RFN, the source node puts the TCP connection into a snooze state, resets all the timers and stops further transmission. If an intermediate node finds a new route to the destination, it sends a route re-establishment notification (RRN) message to the source node. On receiving the RRN, the source node again activates the TCP connection. The main drawback of TCP-F is that upon reactivation of TCP connection the size of the congestion window remains same as before which may lead to either congestion or inefficient bandwidth utilization.
Liu and Singh proposed Ad hoc TCP (ATCP) [8] that provides a robust solution as it considers most of the issues related to TCP in wireless ad hoc networks. However, ATCP performs poorly due to inefficient conges- tion window adaptation whenever a link failure occurs [15] . Upon detection of a link failure, it enters into slow start phase and increments the congestion window in a slow pace. P-TCP [11] takes feedback from network layer to detect different types of packet losses and adjusts its parameters according to the varying wireless ad hoc network environment.
All of the above transport protocols, except P-TCP, do not consider the security aspects. In a multi-hop wireless ad hoc network, an intelligent attacker may place itself in an active route and later it can spoof an address of a node in order to start its malicious activities by dropping, forging, misrouting or injecting data packets. Therefore, it is necessary to design a secure transport layer protocol for secure data transmission between source and destination nodes. In the following paragraphs, we present some exiting work on securing TCP for wireless ad hoc networks.
The scheme proposed in [16] establishes different routes through different intermediate nodes and sends multiple shares of a message through them at different time slots. However, this scheme is suitable for delay tolerant static networks. Papadimitratos and Haas proposed SMT [17] that transmits all the shares of a message simultaneously through the multiple independent routes rather than in different time slots. However, both of the schemes assume that multiple routes exist in a dynamic wireless ad hoc network which may not be realistic in some cases.
In [18] , an ID based secure TCP scheme is proposed. This scheme can securely transmit data using a Diffie- Hellman [19] session key. It assumes that the public-private key pairs along with IDs of nodes are distributed before the network deployment. In this protocol, a node may not be able to change its ID throughout the lifetime of the network and therefore the protocol is secured. However, the protocol has considerably high overhead due to key generation in each session. P-TCP [11] , uses an identity-based public key cryptography to generate a session key for secure data transmission between source and destination nodes. However, this protocol may fail when a malicious node exists on the path.
IPSEC [20] is a popular security mechanism mainly used in wired networks to mitigate most of the attacks discussed in Section 1. However, it does not provide an intermediate node to directly access an IP header of a transmitted packet. The transport layer protocols proposed for WANETs have to rely on information fed back from the intermediate nodes (e.g., Explicit Congestion Notification (ECN) [21] ), and hence IPSEC cannot be incorporated with these protocols [22] . Similar is the case with PCT, SSL and TLS [23] proposed for the wired networks.
3. System Model and Key Distribution
Here, we assume SDRP [24] as the ad hoc routing protocol used in the network layer. We also assume that Explicit Congestion Notification (ECN) [21] is enabled and the public/private key pairs are distributed to each node prior to the network starting its operation. The public 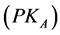 /private
/private 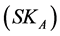 key pair of a node
key pair of a node 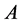 are distributed using the following technique [25] [26] : Let us assume that
are distributed using the following technique [25] [26] : Let us assume that 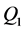 and
and 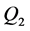 be the two groups of a prime order
be the two groups of a prime order 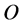 and
and 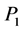 and
and 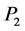 be the generators of
be the generators of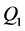 . A bilinear pairing is a map
. A bilinear pairing is a map 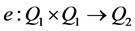 which has the following properties:
which has the following properties:
• Bilinear: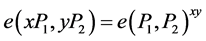 ,
,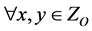 ;
;
• Non-degenerate: There exist 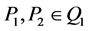 such that
such that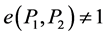 ;
;
• Computable: There exist an efficient algorithm to compute 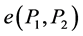
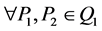 .
.
The security parameters![]() ,
, ![]() ,
, ![]() ,
, ![]() ,
, ![]() ,
, ![]() ,
, ![]() are publicly known by all the nodes in the network. Here, the network master key
are publicly known by all the nodes in the network. Here, the network master key ![]() is shared by a set of
is shared by a set of ![]() nodes. Threshold cryptography technique is used where
nodes. Threshold cryptography technique is used where ![]() nodes in a network is required to construct the master key
nodes in a network is required to construct the master key![]() .
. ![]() and
and ![]() are the two cryptographic hash functions such that
are the two cryptographic hash functions such that ![]() and
and![]() . Node
. Node ![]() with identifier
with identifier ![]() (i.e., hardware address of
(i.e., hardware address of![]() ), will have a public key
), will have a public key ![]() and a private key
and a private key![]() . In addition, shared key
. In addition, shared key ![]() between nodes
between nodes ![]() and
and ![]() is generated in a non-interactive fashion [27] :
is generated in a non-interactive fashion [27] :![]() . The above key distribution is necessary for authentication of nodes in the ad hoc network to nullify the attacks.
. The above key distribution is necessary for authentication of nodes in the ad hoc network to nullify the attacks.
4. SA-TCP: Secure and Adaptive Transmission Control Protocol
In this section, we present the proposed modification to TCP New Reno, named SA-TCP, for wireless ad hoc networks. This work is an extension of our earlier work [28] . SA-TCP handles network congestion in three phases: slow start, congestion avoidance and congestion detection. In slow start and congestion avoidance phases, SA-TCP enhances the performance of TCP New Reno by adjusting the values of congestion window (CWND) and congestion window limit (CWL) according to dynamic network conditions. Therefore, SA-TCP minimizes the chance of congestion and MAC layer collisions in the network.
In congestion avoidance phase of SA-TCP, whenever there is a change in size of CWND, it is taken as a sample and this sample value of ![]() -th congestion window size has been denoted here as
-th congestion window size has been denoted here as![]() . SA-TCP operates in normal mode (i.e., similar to original TCP New Reno) for collecting samples of earlier CWND sizes
. SA-TCP operates in normal mode (i.e., similar to original TCP New Reno) for collecting samples of earlier CWND sizes ![]() (where
(where![]() ). It calculates the value of current congestion window
). It calculates the value of current congestion window ![]() from these
from these ![]() samples using the following Equation (1):
samples using the following Equation (1):
![]() (1)
(1)
SA-TCP also sets the sizes of future CWND sizes in case the network condition remains unchanged. The proposed algorithm collects such ![]() samples while working in the normal mode and creates the future congestion window sizes. Here, the value of
samples while working in the normal mode and creates the future congestion window sizes. Here, the value of ![]() is an important factor to predict the current congestion window size. Using a smaller value of
is an important factor to predict the current congestion window size. Using a smaller value of ![]() may give inaccurate prediction of the network condition, whereas a larger value of
may give inaccurate prediction of the network condition, whereas a larger value of ![]() may make SA-TCP behave like TCP New Reno. We use a least-square method [11] [29] to compute the value of
may make SA-TCP behave like TCP New Reno. We use a least-square method [11] [29] to compute the value of ![]() as follows:
as follows:
![]() (2)
(2)
Here![]() , and
, and ![]() is the
is the ![]() -th sample of the congestion window that is predicted. We select the value of
-th sample of the congestion window that is predicted. We select the value of ![]() corresponding to the minimum sum of residuals
corresponding to the minimum sum of residuals![]() . These ensure that the value of congestion window CWND will not exceed the value of congestion window limit CWL [11] .
. These ensure that the value of congestion window CWND will not exceed the value of congestion window limit CWL [11] .
SA-TCP also reduces the chance of MAC layer collisions by restricting the value of the congestion window according to the equation [30] ![]() , wherein
, wherein ![]() is the upper/lower bound of bandwidth delay product,
is the upper/lower bound of bandwidth delay product, ![]() and RH is the number of round-trip hop-count from source to destination nodes on the path. SA-TCP source node obtains the value of RH through RREP message of SDRP [24] routing protocol.
and RH is the number of round-trip hop-count from source to destination nodes on the path. SA-TCP source node obtains the value of RH through RREP message of SDRP [24] routing protocol.
In congestion detection phase, SA-TCP detects the congestion in the network using the explicit congestion notification (ECN) [21] bit. When a node on an active route detects the congestion, it sends an ACK segment to the source node with ECN bit enabled. On receiving the ACK segment, the source node reduces both sizes of present CWL and CWND to half its size and sets this reduced CWND size as the slow start threshold (ssthreshold) value. Thereafter it sets the value of CWND size to 1 and enters into the slow start phase [11] . SA-TCP handles congestion using the pseudo code presented in Algorithm 1.
Apart from segment loss due to congestion, segment may be lost due to either lossy channel or a link failure between the source and destination nodes. In order to detect a link failure on an active route, SA-TCP uses the route error (RERR) message of SDRP [24] routing protocol. Here, it uses the concept of P-TCP [11] while setting up its parameters after the route is re-established. The source node stops transmitting segments to the destination once it detects a link failure and waits till the route is re-established. When the route is re-established, the source node obtains the value of round-trip hop-count (RH) from route reply (RREP) message of [24] routing protocol and calculates the value of congestion window limit CWL for the new route. Further, if the size of congestion window CWND is higher than the size of CWL, SA-TCP source node reduces the size of CWND to half. Otherwise the source node keeps the value of CWND same as was at the time of link failure. At this point, SA-TCP enters back to its original phase of congestion avoidance or slow start as it was at the time of link failure. The above condition is necessary to ensure that the size of CWND never exceeds the size of CWL even when the route is re-established. Hence SA-TCP minimizes the chance of congestion and collisions in the network. Algorithm 2 presents the pseudo code for SA-TCP link failure handler.
![]()
![]()
Security
This section describes a mechanism to secure the three-way handshaking connection establishment and connection termination processes of SA-TCP. Here, source ![]() and destination
and destination ![]() nodes of the end-to-end connection to be established first exchange their
nodes of the end-to-end connection to be established first exchange their ![]() (
(![]() and
and![]() ) and random numbers (
) and random numbers (![]() by source node and
by source node and ![]() by destination node) to each other in signed
by destination node) to each other in signed ![]()
![]() and signed
and signed ![]()
![]() messages respectively. Each intermediate node
messages respectively. Each intermediate node ![]() on the path also generates a random number
on the path also generates a random number ![]() and sends it to source and destination nodes in signed
and sends it to source and destination nodes in signed ![]()
![]() and
and ![]() messages respectively. The signature scheme proposed in [25] is used here for the purpose of authentication. Thereafter node
messages respectively. The signature scheme proposed in [25] is used here for the purpose of authentication. Thereafter node ![]() generates a session secret key
generates a session secret key![]() , wherein
, wherein ![]() is the private key of node
is the private key of node![]() ,
, ![]() is the public key of
is the public key of
node ![]() and
and ![]() (here
(here ![]() is the number of intermediate nodes between source and destination
is the number of intermediate nodes between source and destination
nodes). Subsequently ![]() starts three-way handshaking connection establishment process with
starts three-way handshaking connection establishment process with ![]() similar way to the scheme given in [18] . It first generates an initial sequence number
similar way to the scheme given in [18] . It first generates an initial sequence number ![]() from a monotonically increased random number
from a monotonically increased random number ![]() and a hash value of source port address
and a hash value of source port address![]() , destination port address
, destination port address![]() ,
, ![]() ,
, ![]() and
and![]() .
. ![]() also computes an authentication tag
also computes an authentication tag ![]() on
on ![]() segment using a HMAC function and a session secret key
segment using a HMAC function and a session secret key![]() . This
. This ![]() segment is sent along with the tag
segment is sent along with the tag ![]() by
by ![]() to
to![]() .
.
On receiving the ![]() from
from![]() ,
, ![]() computes the session secret key
computes the session secret key
![]() , wherein
, wherein ![]() is the private key of
is the private key of![]() ,
, ![]() is the public key of
is the public key of ![]() and
and
![]() . It also generates the authentication tag
. It also generates the authentication tag ![]() on received
on received ![]() segment using the hash
segment using the hash
function and![]() . If the generated tag
. If the generated tag ![]() and the received tag
and the received tag ![]() are same, then
are same, then ![]() concludes that
concludes that ![]() is authenticated. On successful authentication,
is authenticated. On successful authentication, ![]() generates
generates ![]() and an authentication tag
and an authentication tag ![]() on
on ![]() segment in the similar way to
segment in the similar way to![]() . This
. This ![]() segment is sent along with
segment is sent along with ![]() by
by ![]() to
to![]() . On receiving
. On receiving![]() ,
, ![]() com- putes the authentication tag
com- putes the authentication tag ![]() on received
on received ![]() segment using the session secret key
segment using the session secret key![]() . If both of the tags (generated
. If both of the tags (generated ![]() and received tag
and received tag![]() ) are same then
) are same then ![]() concludes that
concludes that ![]() is authenticated.
is authenticated. ![]() also sends
also sends ![]() segment to
segment to![]() .
. ![]() generates the tag
generates the tag ![]() on received
on received ![]() segment and verifies it with the received tag
segment and verifies it with the received tag![]() . If both tags are same,
. If both tags are same, ![]() finishes the three-way handshaking connection establishment process and also allocates resource for
finishes the three-way handshaking connection establishment process and also allocates resource for ![]() and starts sending of data messages along with authentication tags. The pseudo code of three-way handshake connection estab- lishment processes for source
and starts sending of data messages along with authentication tags. The pseudo code of three-way handshake connection estab- lishment processes for source ![]() and destination
and destination ![]() are given in Algorithm 3 and Algorithm 4 respec- tively. SA-TCP secures the three-way handshake connection termination process in the same way as connection establishment process. It may be noted here that an intermediate node sends ECN in the ACK segments and authentication tags whenever the node detects congestion.
are given in Algorithm 3 and Algorithm 4 respec- tively. SA-TCP secures the three-way handshake connection termination process in the same way as connection establishment process. It may be noted here that an intermediate node sends ECN in the ACK segments and authentication tags whenever the node detects congestion.
Analysis: The proposed SA-TCP sends all the segments along with authentication tag and ID of the sender. Here, an ID of a network node can be spoofed by an attacker but it may not be able to generate the valid authentication tags. This is due to the fact that it is difficult for the attacker to know the private keys and the master key of a network. The master key is shared between ![]() nodes in the network where it may only get disclosed if
nodes in the network where it may only get disclosed if ![]() nodes gets compromised. Hence the chances of SYN flooding and segment forging attacks are very low in SA-TCP. The proposed protocol generates the initial sequence number
nodes gets compromised. Hence the chances of SYN flooding and segment forging attacks are very low in SA-TCP. The proposed protocol generates the initial sequence number ![]() from a monotonically increasing random number
from a monotonically increasing random number ![]() and a hash value of source port
and a hash value of source port![]() , destination port
, destination port![]() , source ID
, source ID![]() , destination ID
, destination ID ![]() and a session secret key. Therefore, it is also difficult for the attacker to guess the ISN and hijack a session or creating ACK storm in the network.
and a session secret key. Therefore, it is also difficult for the attacker to guess the ISN and hijack a session or creating ACK storm in the network.
It can also be seen that SA-TCP does not require any certificate or large sized public key for authentication. It uses identity-based cryptography where the public key of a node is generated from its ID (i.e., 48-bit hardware address). Therefore, SA-TCP only requires to send the ID with the segments thereby eliminating the need of sending the public key. Thus, we find that the proposed protocol has low overhead. However, the session secret key has to generate for each session, which increases the protocol overhead slightly. The following equation
![]()
![]()
shows that both source-destination pairs generate the same session secret key:
![]()
where![]() .
.
5. Simulation
In order to compare the performances, we have simulated the proposed SA-TCP along with TCP New Reno [2] and Ad hoc TCP (ATCP) [8] using NS-2 (version-2.34) simulator on a computer running Linux Cent OS 5. Throughput is chosen as the performance comparison metric. We have considered three different simulation scenarios as follows:
Scenario 1—Dynamic Random Topology: In this scenario, we adopt random way-point mobility model where we vary the speed of the nodes between 0 m/s to 25 m/s. The pause time is set to 0s for acquiring continuous motion of the nodes in the simulations. This scenario is simulated for 50 number of mobile nodes in a network area of size![]() .
.
Scenario 2—String Topology: We vary the hop distance between source and destination to show the effect in a string topology for the protocols under consideration. This scenario is simulated for 11 number of nodes in a static network of area size![]()
![]() . Figure 1 shows an example of a string topology with 11 number of nodes.
. Figure 1 shows an example of a string topology with 11 number of nodes.
Scenario 3—Grid Topology: Figure 2 shows an example of a grid topology of size![]() . Under this scenario, the network load is varied by increasing the number of TCP connections from 1 to 5. This simulation is done for
. Under this scenario, the network load is varied by increasing the number of TCP connections from 1 to 5. This simulation is done for
a grid of size ![]() in a static network.
in a static network.
The following simulation parameters are kept common for the above mentioned scenarios. The radio transm-
ission range of each node is set to 250 m. Two-ray ground propagation model is used and IEEE 802.11 standard has been used as the Medium Access Control layer protocol. Constant bit rate (CBR) traffic generator is used of packet size 512 bytes with 4 packets/second traffic generation rate. We have set ![]() as the total simulation time for each set of simulations.
as the total simulation time for each set of simulations.
Simulation Results
Scenario 1—Dynamic Random Topology: The impact of node mobility on throughput is shown in Figure 3(a). From the figure we see that the throughput decreases with increased node mobility for all the protocols under consideration. This is due to the increase number of link failures with increased mobility of nodes resulting in segment losses. It can also be seen that the proposed SA-TCP gives better throughput compared to New Reno and ATCP. This is due to the fact that New Reno cannot detect link failures and thereby retransmits duplicate segments unnecessarily. It also mistakes these link failures as congestions in the network and enters into slow start phase. Even though ATCP detects the link failure, the protocol sets CWND to 1 and gradually increments it to the normal size. On the other hand, on detecting a link failure, SA-TCP enters back into the original phase (either congestion avoidance or slow start) as it was at the time of link failure and computes CWND according to the new route condition.
Scenario 2—String Topology: Figure 3(b) shows the effect of the number of hop distances from source to destination nodes on the network throughput. It can be seen that the throughput decreases with the increased number of hop distances for New Reno, ATCP and the proposed SA-TCP. This is due to the number of MAC layer collisions keeps on increasing with the number of hops. SA-TCP performs better because it sets the mean value of CWND periodically. Further, it tries to reduce the collisions by adjusting the value of CWND according to the network condition and limits the congestion window below a certain value. On the other hand, as no precaution is taken to limit the congestion window by New Reno and ATCP, unnecessary collisions takes place in the network, which in turn triggers retransmissions leading to a domino effect [30] .
Scenario 3—Grid Topology: Figure 4 shows throughput of the protocols under consideration in a grid topology. Here, throughput decreases with increased network loads (in terms of number of connections) for all the protocols. As the number of connection increases in the network, the intermediate nodes are also overloaded with number of packets. Therefore, each node on the route has burdens of packet enqueue/dequeue delays
![]() (a) (b)
(a) (b)
Figure 3. (a) Throughput vrs. node mobility in dynamic random topology; (b) Throughput vrs. hop distance between source- destination in string topology.
![]()
Figure 4. Throughput vrs. network loads in a grid topology.
leading to an overall congestion in the network. SA-TCP adjusts the congestion window efficiently and subsequently it tries to reduce the chance of congestion and MAC layer collisions in the network. The effect is clearly shown in Figure 4.
6. Conclusion
This paper proposed a secure and adaptive TCP, called SA-TCP, for wireless ad hoc networks that utilizes network layer information to differentiate different types of packet losses. In order to minimize the chances of congestion and collisions in the network, SA-TCP adjusts the values of congestion window (CWND) and congestion window limit (CWL) from their previous state values. The proposed protocol uses a low complex identity-based public key cryptography where the public key of a node is evaluated from its ID. Further, all SA-TCP segments are sent along with MAC tags for the purpose of authentication. Simulation results are given to show that SA-TCP outperforms New Reno and ATCP in standard wireless ad hoc network scenarios.