Mobility Conscious Medium Access Control Scheme for Wireless Sensor Networks: A Conceptual Approach ()
1. Introduction
Recent technological advancements have made the deployment of small, inexpensive, low-power devices a reality. Wireless Sensor Networks (WSN) has emerged as one of the first real applications of ubiquitous computing. It plays a key role in bridging the gap between the physical and the computational world by providing reliable, scalable, fault tolerant, and accurate monitoring of physical and environmental conditions [1] . The development of WSN was originally motivated by military applications such as battlefield surveillance. In recent times, they are used in many applications ranging from health such as tracking and monitoring doctors and patients to environmental such as precision agriculture, home application such as smart environment, commercial application such as detecting and monitoring car thefts [2] . Furthermore, WSN is a wireless network consisting of spatially distributed sensor nodes to cooperatively monitor a region to obtain data about the environment, physical or environmental conditions such as temperature, sound, vibration, pressure, motion or pollutants at different locations.
Figure 1 shows a typical deployment of sensor nodes in data gathering applications. Sensors are typically scattered in a field. The scattered sensor nodes are deployed randomly in a sensor field. Sensor nodes collect and route data, which is aggregated back to the Sink by multi-hops. In this figure, node A communicates with Sink to deliver messages, it will route data from A to E or from E to A by multi-hops. The Sink communicates with the task manager node through Internet or satellite link to deliver data that is aggregated. The task manager node also uses the collected data to make relevant analysis and applications. A user makes use of any display interface (i.e. PDA, computers) to retrieve or analyze these information locally or remotely.
In WSN, to extend the battery lifetime, protocols at the data link layer usually put sensors in a sleep mode most of the time, and only let nodes wake up periodically for data communication. This mode of operation, which trades network metrics for energy saving, proves to be very effective in stationary network, where connection formations and break-ups are rare events. However, these protocols, which are customized for stationary networks, do not work well in mobile scenarios such as a patient assistance system which monitors patients’ health conditions via wearable bio-sensors, workers equipped with sensor device in disaster recovery situation, soldiers in battle field, and to provide these with appropriate care when needed [3] .
In most of the existing works, efforts have been made to develop MAC protocols that primarily conserve energy assuming static nodes. They failed to consider real life situations where some nodes are mobile hence this renders the existing schemes inefficient when it comes to mobility. However, for the purpose of this work Gauss Markov mobility model is adopted. This work will also use Clear Channel Assessment (CCA) and packets back-off for channel negotiation and Low Power Listening (LPL) for low power communication and also mobility patterns for node awareness. This is with a view to check the status of the channel and report back if there is activity. The rest of this paper is organized as follows. In Section 2, we presented reviews of related works. We described the overview of a Mobility Conscious Medium Access Control (MAC) Scheme in Section 3. In Section 4, the model formulation is presented while Section 5 offers concluding thoughts and future work.
2. Related Works
A MAC protocol is required in sensor networks to coordinate the sensor nodes’ access to the shared medium [4] . Many works have been and are being done on medium access control (MAC) protocols for wireless sensor networks.
The work done by [5] on Sensor Medium Access Control (S-MAC), a Medium Access Control (MAC) protocol was specifically designed for WSN. The main objective of S-MAC is to conserve energy in sensor networks. It takes into consideration that fairness and latency are less critical issues compared to energy savings. The basic idea of S-MAC is that time is divided into frames. It uses a listen/sleep cycle to reduce energy consumption. It forces sensor nodes to operate at low duty cycle by putting nodes into periodic sleep instead of idle listening. Although, SMAC saves more power than 802.11, it does not adapt to network traffic very well since it uses a fixed duty cycle for all the sensor nodes.
Timeout MAC (T-MAC) proposed by [6] is a contention based MAC protocol. T-MAC improves on S-MAC

Figure 1. Typical WSN deployment in data gathering applications, [2] .
by using an adaptive duty cycle. This means that if there is no activity in the vicinity of a node for a threshold time, the node goes to sleep. Such an adaptation frees the application from the burden of selecting an appropriate duty cycle. TMAC has the same performance as SMAC under constant traffic loads, but saves more energy under variable traffic. The downside of TMAC’s aggressive power conserving policy is that nodes can go to sleep rather early, resulting in increased latency and lower throughput. Another drawback in both SMAC and TMAC is they group the communication during small periods of activity. As a result, the protocols collapse under high traffic loads.
Traffic Adaptive MAC (TRAMAC) was developed by [7] for energy efficient and collision free channel access in wireless sensor networks. It uses the Time Division Multiple Access (TDMA) scheme by dividing time into slots. It assumes that time is slotted and uses a distributed election scheme based on information about the traffic at each node to determine which node can transmit at a particular time slot. It uses traffic-based information to decide on schedules for individual nodes and thus is adaptive to network traffic.
WiseMAC was proposed by [8] and uses a preamble sampling technique called Low Power Listening (LPL), where a node regularly samples or polls the medium for a very brief time to check whether a packet needs to be received. When the node wakes up and senses no traffic, it again goes to sleep mode. If the source has to send some data, it transmits a wakeup preamble. If a node polls the medium and senses the wakeup preamble, it receives the data and acknowledges and again goes to sleep mode. The decentralized sleep-listen scheduling in WiseMAC results in different sleep and wakeup times for each neighbour of a node. This is especially an important problem for broadcast type of communication, since broadcasted packet will be buffered for neighbours in sleep mode and delivered many times as each neighbour wakes up. However, this redundant transmission will result in higher latency and power consumption.
Berkely MAC (B-MAC) was introduced by [9] . B-MAC is a carrier sense media access protocol that uses an adaptive preamble sampling scheme to reduce duty cycle and minimize idle listening. B-MAC uses a technique call Low Listening Power (LLP) to reduce energy consumption. Nodes are awakening at fixed interval (check interval) to check the wireless channel for valid preamble bytes that indicate a pending data transmission from another node.
The limitation is during connection setup time, the mobile node is disconnected from the rest of the network, and thus these mobile nodes may not create a new connection fast enough and will degrade network performance. Thus limited energy resource of sensor nodes will not be efficiently manage, because B-MAC does not take into consideration, mobility of some of the sensor nodes.
The work of [10] was on Lightweight MAC (LMAC). Lightweight medium access protocol uses a TDMA scheme, which provides collision-free communication. It is less energy efficient because each node has to listen for control messages during the whole frame. Besides simplicity, an important design goal was to minimize the number of transitions between receive and transmit mode, because they take time during which the radio cannot be used. Only one time slot is assigned to each node and the node is given control over the time slot. This increases the latency because each node has to wait for its time slot. If there is a new node joining the network it will listen to the whole frame before sending the data. It uses the control packet to inform the other nodes about the route, current time slot etc.
Traffic Aware Energy Efficiency MAC (TEEM) which was also inspired from S-MAC was developed by [11] . In order to reduce the energy consumption, in this work, nodes are not active during the complete sleep period. It goes to sleep directly when no data packets are buffered to be transmitted. TEEM also has more packet collision than S-MAC and TMAC, this is the reason for end to end delay realized which increases exponentially when the node density increases.
Pattern MAC (PMAC) was proposed by [12] . According to the design concept of PMAC the sensor generate an appropriate sleeping schedule based on its own data transfer condition. The objective of these works is mainly to efficiently conserve energy while trading off parameters like latency, fairness and throughput. Meanwhile it obtains the sleep/wake schedule of the neighbouring sensors by the Pattern Exchange process with the neighbouring sensors. PMAC when compared to S-MAC produces higher data throughput and saves more energy.
Mobile Lightweight MAC (MLMAC) proposed by [13] is a modification of the work done by [10] LMAC. It is a TDMA based MAC protocol for mobile wireless sensor networks where all sensor nodes are mobile. The main difference between LMAC and MLMAC is their intended scenario. While LMAC assumes a static sensor network where communication takes place between nodes and the gateway, MLMAC scenario display that all nodes are mobile and communicate among each other. MLMAC does not depend on a gateway to start the synchronization; instead, it is fully dynamic.
3. Overview of a Mobility Conscious Medium Access Control (MAC) Scheme
Based on the work of [9] , there are limitations when the sensor nodes are mobile. BMAC allows each node to wake up occasionally to check for channel activity. The wake-up period is referred to as the check interval. The check interval used by B-MAC assumes nodes are static. During connection setup time, the mobile node is disconnected from the rest of the network, thus these mobile nodes may not create a new connection fast enough. Thus limited energy resource of sensor nodes will not be efficiently manage, because B-MAC does not take into consideration, mobility of some of the sensor nodes. This paper is proposing a mobility conscious scheme to enhance the work done by [9] .
In wireless communication networks, medium access control schemes are used to manage the access of active nodes in a shared channel. Energy and throughput of MAC protocols may significantly affect the overall performance of a wireless sensor network.
3.1. Mobility in Wireless Sensor Networks
Mobility in sensor networks brings the following issues in the design of protocols in different layers:
1) In a mobile network, the position of sensor nodes changes over time. A mobility conscious protocol needs to estimate the position of each node in the network at any point in time.
2) The movement of nodes can cause frame errors in the network. A mobile protocol needs to handle these frame errors and retransmit frames where necessary.
3) In the case of routing protocols, node mobility can result in route changes, which will lead to delivery failures if not propagated in time. To lessen the problem, mobility information needs to be used in route calculation. To this end, neighbours table and route maintenance should adapt to the mobility in networks.
4) In the case of schedule based MAC protocols, a neighbourhood inconsistency of two-hop neighbours information can occur when mobile nodes enter or leave the neighbourhood. This leads to schedule inconsistencies [14] . A mobility conscious MAC protocol needs to utilize the mobility information of nodes and determines which nodes enter or leave the neighbourhood to eliminate these inconsistencies.
3.2. Mobility Patterns
Mobility pattern is the actual set of movements that result from applying the mobility model to one, or more nodes. It plays a significant role in determining protocol performance therefore, it is necessary for mobility models to emulate the movement pattern of targeted real life applications in a reasonable way. Similarly, a mobility pattern is the movement pattern of real life objects such as people or vehicles. According to [15] , a mobility pattern is described by properties like dimension, limitation, group behaviour and predictability.
4. Description of the Proposed Model
The proposed work uses Clear Channel Assessment (CCA) and packets back-off for channel negotiation, and Low Power Listening (LPL) for Low Power Communication (LPC) and also Mobility patterns for node awareness. In order for nodes to be aware of mobile nodes, there is need for a mobility model. The model used in this research work represents a wide range of user mobility patterns including linear motion, random motion and totally random motion. For the purpose of this work Gauss Markov mobility model is used. The proposed model considers both static and mobile nodes and generates mobility patterns for mobile nodes to be integrated as part of the network. It then uses a threshold distance to change the check interval of the channel so as to provide ease of communication. This is an improvement over B-MAC. It will minimize the energy consumed when communicating with other nodes.
Proposed Mobility Model
The Gauss-Markov Mobility Model was first introduced by [16] for the simulation of a Personal Communication Service (PCS) network and was subsequently used for the simulation of an ad hoc network protocol by [17] . The model has since been widely utilized. Gauss-Markov mobility model was used for the work because the model is capable of duplicating different kinds of mobility behaviour in various scenarios and models. It does this using a tuning parameter to vary the degree of randomness. The proposed model considers both static and mobile nodes and generates mobility patterns for mobile nodes to be integrated as part of the network. It then uses a threshold distance to change the check interval of the channel so as to provide ease of communication. Also the next movement of the mobile nodes is dependent on its previous movement. That is the movement of the mobile nodes is correlated in time. The model was designed with a tuning parameter . The tuning parameter affects the randomness of the behaviour of a mobile node. In this model, a sensor node’s velocity is assumed to be correlated in time and modeled by a Gauss-Markov random process. In continuous time, a stationary Gaussian process
. The tuning parameter affects the randomness of the behaviour of a mobile node. In this model, a sensor node’s velocity is assumed to be correlated in time and modeled by a Gauss-Markov random process. In continuous time, a stationary Gaussian process  is a Gauss-Markov process if it has the autocorrelation function. This is as shown below:
is a Gauss-Markov process if it has the autocorrelation function. This is as shown below:
 (1)
(1)
where  is the variance of
is the variance of 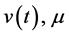 is its mean and
is its mean and  determines the degree of memory.
determines the degree of memory.
The discrete version of the mobile velocity is defined with , and the memory level
, and the memory level , where
, where  is normalized to unity. The discrete Gauss-Markov process in equation (i) can be represented by the following recursive realization:
is normalized to unity. The discrete Gauss-Markov process in equation (i) can be represented by the following recursive realization:
 (2)
(2)
where 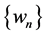 is an uncorrelated Gaussian process with zero mean and unit variance and is independent of
is an uncorrelated Gaussian process with zero mean and unit variance and is independent of . Initially each mobile node is assigned an initial speed and direction. At fixed intervals of time,
. Initially each mobile node is assigned an initial speed and direction. At fixed intervals of time, , movement occurs by updating the speed and direction of each mobile node. Specifically, the value of speed and direction at the
, movement occurs by updating the speed and direction of each mobile node. Specifically, the value of speed and direction at the  instance is calculated based on the value of speed and direction at the
instance is calculated based on the value of speed and direction at the 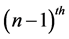 instance i.e. the previous instance and a random variable using the following equations according to [18] :
instance i.e. the previous instance and a random variable using the following equations according to [18] :
 (3)
(3)
 (4)
(4)
where 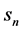 and
and  are the new speed and direction of the mobile node at time interval
are the new speed and direction of the mobile node at time interval ;
; , where
, where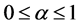 , is the tuning parameter used to vary the randomness;
, is the tuning parameter used to vary the randomness;  and
and  are constants representing the mean value of speed and direction as
are constants representing the mean value of speed and direction as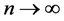 ; and
; and  and
and  are random variables from a Gaussian distribution with mean equal to zero and standard deviation equal to one.
are random variables from a Gaussian distribution with mean equal to zero and standard deviation equal to one.
At each time interval the next location is calculated based on the current location, speed and direction of movement. Specifically, at time interval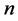 , a mobile node’s position is given by the equations:
, a mobile node’s position is given by the equations:
 (5)
(5)
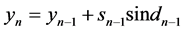 (6)
(6)
where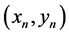 and
and  are the
are the  and
and 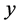 coordinates of the mobile node’s position at the
coordinates of the mobile node’s position at the  and
and 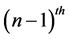 time intervals, respectively, and
time intervals, respectively, and 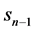 and
and  are the speed and direction of the mobile node respectively at the
are the speed and direction of the mobile node respectively at the 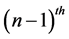 time interval [19] .
time interval [19] .
In this work, the nodes position in  and
and  dimension will be calculated as well as the distance dist, between each nodes. This is given by:
dimension will be calculated as well as the distance dist, between each nodes. This is given by:
 (7)
(7)
The distance above the maximum distance between each node; a threshold distance 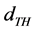 will be set to 5m. Based on the threshold distance
will be set to 5m. Based on the threshold distance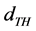 , the check interval of the channel is changed depending on the if
, the check interval of the channel is changed depending on the if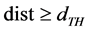 . This will enable the nodes to know the node that is moving and the node that is static so as to decide which nodes to communicate with. The pseudocode of the proposed model is illustrated thus:
. This will enable the nodes to know the node that is moving and the node that is static so as to decide which nodes to communicate with. The pseudocode of the proposed model is illustrated thus:
Pseudocode of the Mobility Conscious Scheme Step 0: Let the nodes position be represented by 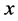 and
and . Let distance between nodes be represented by dist. Let the threshold distance be represented by
. Let distance between nodes be represented by dist. Let the threshold distance be represented by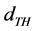 . Let the floor estimation be represented by
. Let the floor estimation be represented by .
.
Step 1: Generate mobility patterns using 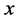 and
and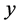 .
.
Step 2: Get nodes distance from each other using dist.
Step 3: Set 
Step 4: change check interval if 
Step 5: Add the information to the neighbourhood list of nodes.
Step 6: Set initial back off Step 7: Check the channel to determine if it is clear using noise floor estimation.
Step 8: If channel is busy receive data or transmit data else sleep Step 9: Stop
5. Conclusion
In this paper, attempt to model mobility pattern using Gauss Markov Mobility Model was achieved. The mathematical model was formulated with a view to determine the position and distance of the sensor nodes and how they are correlated in time. This model used the information of the distance between sensor nodes to check interval of the channel in order to provide ease of communication. This has a substantial effect on reducing the energy consumption and improving the throughput between sensor nodes. Differently from all other relevant heuristics approaches, our approach enhances faster connection and more time for sensor nodes to sleep.
Further Works
Future works will be to evaluate the mobility scenario for the sensor nodes. This will be done using an appropriate simulation tool and the performance metrics of interest. The results of the simulation will be benchmarked with the existing schemes in order to determine its efficiency.