1. Introduction
This paper is located in the area of group based cryptography. A cryptographic protocol consists of the collection of rules, formulas and methods to handle a cryptographic task. In cryptology it is common to call the parties who want to communicate privately with each other Alice and Bob.
The traditional cryptographic protocols, both symmetric key and public key, such as the RSA algorithm, Diffie-Hellman and elliptic curve methods, are number theory based. Hence, from a theoretical point of view, they depend on the structure of abelian groups. Although there have been no successful attacks on the standard protocols, there is a feeling that the strength of computing machinery has made the techniques less secure. As a result of this, there has been an active line of research to develop and analyse new cryptographic protocols, as for example cryptosystems and key exchange protocols, based on non-commutative cryptographic platforms. Up to this point the main sources for non-commutative platforms have been nonabelian groups. For an overwiev about mathematical cryptography see [1] and especially for a book about non-commutative group based cryptography see [2] .
Important along the line of cryptographic protocols are secret sharing protocols. These consist of methods to distribute a secret among a group of users by giving a share of the secret to each. The secret can be recovered only if a sufficient number of users (but perhaps not all) combine their pieces. There are many different motivations for the secret sharing problem. One of the most important is the problem of maintaining sensitive information. There are two crucial issues here: availability and secrecy. If only one person keeps the entire secret, then there is a risk that the person might lose the secret or the person might not be available when the secret is needed. Hence it is often useful to utilize several people in order to access a secret. On the other hand, the more people who can access the secret, the higher the chance the secret will be leaked. By sharing a secret in a threshold scheme the availability and reliability issues can be addressed. The paper by C. Chum, B. Fine and X. Zhang [3] contains a wealth of information on secret sharing schemes in general and managing an access control group.
This paper is organized as follows. We first describe secret sharing protocols and a combinatorial distributions of shares, which are given by D. Panagopoulos in [4] . After introductory definitions we start with a secret sharing scheme using directly the combinatorial distribution of shares. Based on this we present two schemes in which we apply regular Nielsen transformations in connections with faithful representations of free groups and the Nielsen reduction theory. We also modify the secret sharing schemes to a private key cryptosystem and finally Nielsen transformations are used for a public key cryptosystem which is inspired by the ElGamal cryptosystem. The new cryptographic protocols are in the dissertation of A. Moldenhauer [5] under her supervisor G. Rosenb-erger at the University of Hamburg. Thus, parts of this paper are from [5] .
2. Preliminaries for the Newly Developed Cryptographic Protocols
A  -secret sharing protocol, with
-secret sharing protocol, with 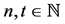 and
and , is a method to distribute a secret among a group of n participants in such a way that it can be recovered only if at least t of them combine their shares. Hence any group of
, is a method to distribute a secret among a group of n participants in such a way that it can be recovered only if at least t of them combine their shares. Hence any group of 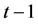 or fewer participants cannot calculate the secret. The number t is called threshold. The person who distrib- utes the shares is called dealer.
or fewer participants cannot calculate the secret. The number t is called threshold. The person who distrib- utes the shares is called dealer.
One of the first  -secret sharing schemes is introduced by A. Shamir in [6] . It has become the standard method for solving the
-secret sharing schemes is introduced by A. Shamir in [6] . It has become the standard method for solving the  -secret sharing problem.
-secret sharing problem.
A. Shamir uses polynomial interpolation for his 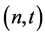 -secret sharing scheme. Let
-secret sharing scheme. Let 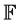 be any field and let
be any field and let 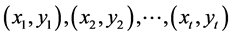 be t points in
be t points in 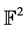 with pairwise distinct
with pairwise distinct ,
,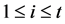 . We say a polynomial
. We say a polynomial 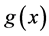 over
over  interpolates these points if
interpolates these points if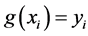 ,
, . A. Shamir’s secret sharing scheme is based on the following theorem.
. A. Shamir’s secret sharing scheme is based on the following theorem.
Theorem 1. [7]
Let ![]() be any field and let
be any field and let ![]() be t pairwise distinct elements of
be t pairwise distinct elements of ![]() and let
and let ![]() be any elements of
be any elements of![]() . Then there exists a unique polynomial of degree less than or equal to
. Then there exists a unique polynomial of degree less than or equal to ![]() that interpolates the t points
that interpolates the t points![]() ,
,![]() .
.
A. Shamir’s ![]() -secret sharing scheme is roughly this: The dealer chooses a field
-secret sharing scheme is roughly this: The dealer chooses a field![]() . The secret S is an element in
. The secret S is an element in![]() . The dealer picks a polynomial
. The dealer picks a polynomial ![]() of degree
of degree ![]() with the secret S as constant term, that is,
with the secret S as constant term, that is, ![]() ,
, ![]() and
and![]() . He chooses pairwise distinct elements
. He chooses pairwise distinct elements![]() , with
, with ![]() for all
for all ![]() and distributes to each of the n participants a point
and distributes to each of the n participants a point ![]() as a share. By Theorem 1 any t participants can determine the polynomial
as a share. By Theorem 1 any t participants can determine the polynomial ![]() (for example with Lagrange interpolation, see [7] ) and hence recover the secret S. If less than t people combine their shares any element in
(for example with Lagrange interpolation, see [7] ) and hence recover the secret S. If less than t people combine their shares any element in ![]() can be the constant term and hence the secret. A. Shamir suggested to use
can be the constant term and hence the secret. A. Shamir suggested to use ![]() where p is a large prime number.
where p is a large prime number.
D. Panagopoulos presents in his paper [4] a ![]() -secret sharing scheme using group presentations with solvable word problem. For the secret sharing schemes in the following sections we use a combinatorial distribution of the shares, which is explained in the paper of D. Panagopoulos.
-secret sharing scheme using group presentations with solvable word problem. For the secret sharing schemes in the following sections we use a combinatorial distribution of the shares, which is explained in the paper of D. Panagopoulos.
Share distribution method explained by D. Panagopoulos.
To distribute the shares in a ![]() -secret sharing scheme the dealer does the follo- wing steps:
-secret sharing scheme the dealer does the follo- wing steps:
1) Calculate![]() , the number of all elements, for example
, the number of all elements, for example![]() , the participants need to know for the reconstruction of the secret.
, the participants need to know for the reconstruction of the secret.
2) Let ![]() be an enumeration of the subsets of
be an enumeration of the subsets of ![]() with
with ![]() elements. Define n subsets
elements. Define n subsets ![]() of the set
of the set ![]() with the property.
with the property.
![]() (1)
(1)
3) The dealer distributes to each of the n participants one of the sets![]() .
.
In addition to this share distribution method the new protocols in this paper are based on combinatorial group theory and Nielsen transformations. Therefore, we review some basic definitions concerning regular Nielsen transformations and Nielsen reduced sets (see [8] or [9] ).
Combinatorial group theory is the branch of algebra which studies groups with the help of group presentations. A group presentation for a group G consists of a set X of generators and a set R of defining relators on X. We write.
![]()
The group G is called finitely generated if both sets X and R are finite. The newly developed cryptographic protocols use finitely generated free groups. Let F be a finitely generated free group with free generating set![]() ,
, ![]() , then the
, then the
group F is the set of all reduced words in![]() , which is defined as
, which is defined as![]() , where a word is called reduced if it does not contain subwords of the form
, where a word is called reduced if it does not contain subwords of the form ![]() or
or![]() ,
,![]() . The identity is considered as the empty word, which is 1. The set of relators for a free group consists only of trivial relators, which are of the form
. The identity is considered as the empty word, which is 1. The set of relators for a free group consists only of trivial relators, which are of the form ![]() or
or![]() , with
, with ![]() a word in X, thus we denote F by
a word in X, thus we denote F by
![]()
The empty space on the right symbolized, that there are only trivial relators. For more information about group theory see for instance [8] , [9] or [10] .
Let F be a finitely generated free group on the free generating set![]() ,
, ![]() , and let
, and let![]() ,
, ![]() , with
, with ![]() reduced words in X.
reduced words in X.
Definition 2 An elementary Nielsen transformation on ![]() is one of the following transformations.
is one of the following transformations.
(T1) replace some ![]() by
by![]() ;
;
(T2) replace some ![]() by
by ![]() where
where![]() ;
;
(T3) delete some ![]() where
where![]() .
.
In all three cases the ![]() for
for ![]() are not changed. A (finite) product of elemen- tary Nielsen transformations is called a Nielsen transformation. A Nielsen transfor- mation is called regular if it is a finite product of the transformations (T1) and (T2), otherwise it is called singular. The set U is called Nielsen-equivalent to the set V, if there is a regular Nielsen transformation from U to V.
are not changed. A (finite) product of elemen- tary Nielsen transformations is called a Nielsen transformation. A Nielsen transfor- mation is called regular if it is a finite product of the transformations (T1) and (T2), otherwise it is called singular. The set U is called Nielsen-equivalent to the set V, if there is a regular Nielsen transformation from U to V.
Nielsen transformations are a linear technique to study free groups and general infinite groups. In addition the group of all automorphisms of a free group F, denoted by![]() , is generated by a regular Nielsen transformation between two basis of F, and each regular Nielsen transformation between two basis of F defines an automo- rphism of F, see ( [8] , Korollar 2.10).
, is generated by a regular Nielsen transformation between two basis of F, and each regular Nielsen transformation between two basis of F defines an automo- rphism of F, see ( [8] , Korollar 2.10).
Definition 3. A finite set U in F is called Nielsen reduced, if for any three elements ![]() from
from ![]() the following conditions hold:
the following conditions hold:
(N0)![]() ;
;
(N1) ![]() implies
implies![]() ;
;
(N2) ![]() and
and ![]() implies
implies![]() .
.
Here ![]() denotes the free length of
denotes the free length of![]() .
.
Proposition 4. ( [8] , Theorem 2.3) or ( [9] , Proposition 2.2)
If ![]() is finite, then U can be carried by a Nielsen transformation into some V such that V is Nielsen reduced.
is finite, then U can be carried by a Nielsen transformation into some V such that V is Nielsen reduced.
For the secret sharing schemes based on Nielsen transformations we will only use regular Nielsen transformations. We agree on some notations.
We write ![]() if we replace
if we replace ![]() by
by ![]() and we write
and we write ![]() if we replace
if we replace ![]() by
by![]() . If we want to apply t-times one after the other the same Nielsen transfo- rmation
. If we want to apply t-times one after the other the same Nielsen transfo- rmation ![]() we write
we write ![]() and hence replace
and hence replace ![]() by
by![]() . In all cases the
. In all cases the ![]() for
for ![]() are not changed.
are not changed.
Corollary 5. ( [8] , Korollar 2.9)
Let F be a free group with basis X and let U be a subset of X which is Nielsen reduced. Then it is
![]() (2)
(2)
Especially, if U is also a basis for F, then![]() .
.
Theorem 6. ( [8] , Satz 2.6)
Let U be Nielsen reduced, then ![]() is free on U.
is free on U.
For the next lemma we need some notations. Let ![]() be a freely reduced word in X. The initial segment s of w which is “a little more than half” of w (that is,
be a freely reduced word in X. The initial segment s of w which is “a little more than half” of w (that is,
![]() ) is called the major initial segment of w. The minor initial
) is called the major initial segment of w. The minor initial
segment of w is that initial segment ![]() which is “a little less than half” of w (that is,
which is “a little less than half” of w (that is,
![]() ). Similarly, major and minor terminal segments are defined.
). Similarly, major and minor terminal segments are defined.
If the free length of the word w is even, we call the initial segment s of w, with ![]() the left half of w. Analogously, we call the terminal segment
the left half of w. Analogously, we call the terminal segment ![]() of w with
of w with ![]() the right half of w.
the right half of w.
Let ![]() be a set of freely reduced words in X, which are not the identity. An initial segment of a w-symbol (that is, of either
be a set of freely reduced words in X, which are not the identity. An initial segment of a w-symbol (that is, of either ![]() or
or![]() , which are different w-symbols) is called isolated if it does not occur as an initial segment of any other w-symbol. Similarly, a terminal segment is isolated if it is a terminal segment of a unique w-symbol.
, which are different w-symbols) is called isolated if it does not occur as an initial segment of any other w-symbol. Similarly, a terminal segment is isolated if it is a terminal segment of a unique w-symbol.
Lemma 7. ( [10] , Lemma 3.1)
Let ![]() be a set of freely reduced words in X with
be a set of freely reduced words in X with![]() ,
,![]() . Then M is Nielsen reduced if and only if the following conditions are satisfied:
. Then M is Nielsen reduced if and only if the following conditions are satisfied:
1) Both the major initial and major terminal segments of each ![]() are isolated.
are isolated.
2) For each ![]() of even free length, either its left half or its right half is isolated.
of even free length, either its left half or its right half is isolated.
There are different problems known in combinatorial group Theory, for example:
Theorem 8. ( [8] , Satz 1.9) Isomorphism problem in free groups:
Let X and Y be two sets. Let ![]() and
and ![]() be two free groups on X and Y, respectively. The free group G is isomorphic to the free group H if and only if
be two free groups on X and Y, respectively. The free group G is isomorphic to the free group H if and only if![]() .
.
Problem 9. Word problem:
Let ![]() be a presentation of a group and
be a presentation of a group and ![]() a given word in X. Determine algorithmically (in finitely many steps) if g represents the identity or not.
a given word in X. Determine algorithmically (in finitely many steps) if g represents the identity or not.
A further problem, which is a more general problem than the word problem and is needed for some of the developed cryptographic protocols based on combinatorial group theory, is the membership problem or also called extended word problem.
Problem 10. Membership problem:
Given a recursively presented group G, a subgroup H of G generated by ![]()
and an element![]() , determine whether or not
, determine whether or not![]() .
.
A related problem (to the membership problem) is the constructive membership problem.
Problem 11. Constructive membership problem:
Given a recursively presented group G, a subgroup H of G generated by ![]() and an element
and an element![]() , find an expression of h in terms of
, find an expression of h in terms of![]() .
.
Theorem 12. ( [8] , Satz 1.9) Isomorphism problem in free groups:
Let X and Y be two sets. Let ![]() and
and ![]() be two free groups on X and Y, respectively. The free group G is isomorphic to the free group H if and only if
be two free groups on X and Y, respectively. The free group G is isomorphic to the free group H if and only if![]() .
.
Furthermore, we introduce a linear congruence generator because it is also used for the cryptosystems in this paper.
For ![]() let
let ![]() be the ring of integers modulo n. The corresponding residue class in
be the ring of integers modulo n. The corresponding residue class in ![]() for an integer
for an integer ![]() is denoted by
is denoted by ![]() (see also [1] ).
(see also [1] ).
Definition 13. [1]
Let ![]() and
and![]() . A bijective mapping
. A bijective mapping ![]() given by
given by ![]() is called a linear congruence generator.
is called a linear congruence generator.
Theorem 14. [1] (Maximal period length for n = 2m,![]() )
)
Let![]() , with
, with![]() ,
, ![]() and let
and let ![]() such that
such that![]() , with
, with![]() , is a linear congruence generator. Further let
, is a linear congruence generator. Further let ![]() be given and
be given and![]() ,
, ![]() ,
, ![]() ,
, ![]() .
.
Then the sequence ![]() is periodic with maximal periodic length
is periodic with maximal periodic length ![]() if and only if the following holds:
if and only if the following holds:
1) ![]() is odd, consequently
is odd, consequently![]() .
.
2) If ![]() then
then![]() .
.
3) ![]() is odd, consequently
is odd, consequently![]() .
.
3. A Combinatorial Secret Sharing Scheme
Now we present a ![]() -secret sharing scheme, whereby the secret is the sum of the multiplicative inverse of elements in the natural numbers. For the distribution of the shares the dealer uses the method by D. Panagopoulos described in Section 2.
-secret sharing scheme, whereby the secret is the sum of the multiplicative inverse of elements in the natural numbers. For the distribution of the shares the dealer uses the method by D. Panagopoulos described in Section 2.
The numbers n and t are given, whereby n is the number of participants and t is the threshold.
1) The dealer first calculates the number![]() .
.
2) He chooses m elements![]() . From these elements he constructs analogously as in Section 0 the sets
. From these elements he constructs analogously as in Section 0 the sets![]() . The secret S is the sum
. The secret S is the sum
![]() (3)
(3)
3) Each participant ![]() gets one share
gets one share![]() ,
,![]() .
.
If t of the n participants come together they can reconstruct the secret while they first combine their t private sets ![]() and get by construction the set
and get by construction the set![]() .
.
The secret is the sum of the inverse elements in the set![]() , that is
, that is
![]() (4)
(4)
This cryptographic protocol is summarized in Table 1 .
If the dealer needs a special secret ![]() he gives every participant one more element
he gives every participant one more element ![]() in each
in each![]() , with
, with
![]() (5)
(5)
The participants get ![]() by multiplying the reconstructed secret S with x.
by multiplying the reconstructed secret S with x.
Security 15. Each element ![]() is exactly contained in
is exactly contained in ![]() subsets. Hence for each
subsets. Hence for each ![]() the element
the element ![]() is not contained in
is not contained in ![]() subsets from
subsets from![]() . As a consequence,
. As a consequence, ![]() is in each union of t subsets. Otherwise, if just
is in each union of t subsets. Otherwise, if just ![]() arbitrary sets from
arbitrary sets from ![]() are combined, there exist a j such that the element
are combined, there exist a j such that the element ![]() is not included in the union of this sets.
is not included in the union of this sets.
![]()
Table 1. Summary of the combinatorial ![]() -secret sharing scheme.
-secret sharing scheme.
If just one element ![]() is absent, the participants do not get the correct sum S, and hence cannot compute the correct secret.
is absent, the participants do not get the correct sum S, and hence cannot compute the correct secret.
Remark 16. We realize that the share distribution method by D. Panagopoulos is also given as a special case by M. Ito, A. Saito and T. Nishizeki in [11] . In [5] it is shown that if the method in [11] is used to generate a ![]() -secret sharing scheme then the same share distribution method as by D. Panagopoulos is described. M. Ito, A. Saito and T. Nishizeki use a multiple assignment scheme, which is a method to distribute to each participant more than only one share, together with a
-secret sharing scheme then the same share distribution method as by D. Panagopoulos is described. M. Ito, A. Saito and T. Nishizeki use a multiple assignment scheme, which is a method to distribute to each participant more than only one share, together with a ![]() -secret sharing scheme. Thus, the share distribution method by D. Panagopoulos is a special case of paper [11] .
-secret sharing scheme. Thus, the share distribution method by D. Panagopoulos is a special case of paper [11] .
In addition, in [5] it is shown in detail, that the purely combinatorial secret sharing scheme is very similar to a scheme, which J. Benaloh and J. Leichter obtain if they realize a ![]() -secret sharing scheme using minimal CNF-formula, described in their paper [12] .
-secret sharing scheme using minimal CNF-formula, described in their paper [12] .
Remark 17. It is important in terms of practicability, that the dealer calculates and distributes the shares for the participants long before the secret is needed by the participants. Hence, the dealer has enough time to execute the share distribution method and his computational cost should be of no consequence for the cryptographic protocol. If t participants reconstruct the secret, they add up only m elements, which is feasible in linear time.
Example 18. We perform the steps for a ![]() -secret sharing scheme. It is
-secret sharing scheme. It is ![]() and
and![]() .
.
The dealer follows the steps:
1) He first calculates![]() .
.
2) The dealer chooses the numbers![]() ,
, ![]() and
and![]() . The secret is
. The secret is
![]()
(a) The six subsets with size 2 of the set ![]() are
are
![]()
![]()
With help of the ![]() the dealer gets the sets
the dealer gets the sets ![]() and
and![]() , which contain elements from
, which contain elements from![]() . He puts the element
. He puts the element ![]() for which i is not contained in the set
for which i is not contained in the set ![]() for
for ![]() and
and![]() , into the set
, into the set![]() , thus it is:
, thus it is:
![]()
![]()
![]()
![]()
3) The dealer distributes the set ![]() to the participant
to the participant![]() , for
, for![]() .
.
If three of the four participants come together, they can calculate the secret S. For example the participants ![]() and
and ![]() hold the set
hold the set
![]()
and hence get the secret
![]()
4. A Secret Sharing Scheme Using a Regular Nielsen Transformation
![]()
We use the special linear group over the rational numbers because these numbers can be stored and computed more efficiently on a computer than irrational numbers.
Let F be a free group in ![]() of rank
of rank![]() . The dealer wants to
. The dealer wants to
The numbers n and t are given, whereby n is the number of participants and t is the threshold. The dealer does the following steps:
![]() (6)
(6)
He also needs an explicit free generating set M, that is
![]() (7)
(7)
and![]() .
.
2) With the known matrices in the set M he computes the secret
![]() (8)
(8)
![]() is the trace for the matrix
is the trace for the matrix![]() , that is,
, that is,![]() .
.
If the dealer needs a special secret he can act as in Section 3 described.
3) The dealer constructs the shares for the participants in the following way:
(a) He first applies a regular Nielsen transformation simultaneously for both sets X and M to get Nielsen-equivalent sets U and N to X and M, respectively (see Figure 1).
The elements ![]() are words in X and the elements
are words in X and the elements ![]() are words in M. Hence, it is
are words in M. Hence, it is![]() .
.
(b) The dealer now uses the method of D. Panagopoulos to split U and N and to get the shares ![]() for the participants with
for the participants with ![]() and
and![]() .
.
4) The dealer distributes the shares.
If t of the n participants combine their parts they obtain the sets U and N. The secret can be recovered as follows:
1. The participants apply regular Nielsen transformations in a Nielsen reduction manner for U and step by step simultaneously for N. By Proposition 4 they get Nielsen reduced sets ![]() and
and ![]() with
with![]() , see Figure 2.
, see Figure 2.
Because of Corollary 5 it is ![]() and
and![]() , respectively. Hence,
, respectively. Hence, ![]() differs to
differs to ![]() just in the position order and inverses. That means the set
just in the position order and inverses. That means the set ![]() is the set X up to inverses. The same is true for
is the set X up to inverses. The same is true for ![]() and
and![]() . Thus, it is
. Thus, it is ![]() and also
and also ![]() with
with![]() .
.
The cryptographic protocol is summarized in Table 2 (page 73).
Less than t participants can neither get the whole set U, which is Nielsen-equivalent to X, nor the set N, which is Nielsen-equivalent to M.
For the calculation of the secret, the participants need the set M, because the secret depends on the traces of the matrices![]() . The participants need both sets U and N. If they just have one set U or N they cannot get information about the set M.
. The participants need both sets U and N. If they just have one set U or N they cannot get information about the set M.
If the set U is known, it is only known which Nielsen transformation should be done to get the Nielsen-equivalent set X, but it is unknown on which matrices they should be done simultaneously.
If only the set N is known, then the matrices in ![]() are known, but nobody knows which Nielsen transformation should be done on N to get the set M. It is also unknown how many Nielsen transformations were used.
are known, but nobody knows which Nielsen transformation should be done on N to get the set M. It is also unknown how many Nielsen transformations were used.
In the book ( [13] , page 247) of J. Lehner a method is given to explicitly obtain a free
![]()
Figure 1. Simultaneously regular Nielsen transformations for the dealer.
![]()
Figure 2. Simultaneously regular Nielsen transformations for the participants.
![]()
Table 2. Summary of the secret sharing scheme using Nielsen transformations and![]() .
.
Theorem 19. [13] Let F be a free group with countably many free generators![]() . Corresponding to
. Corresponding to ![]() define the matrix
define the matrix
![]() (9)
(9)
with ![]() such that the following inequalities hold:
such that the following inequalities hold:
![]() (10)
(10)
The group G generated by ![]() is isomorphic to F.
is isomorphic to F.
We now present an example for this secret sharing scheme.
Example 20. We perform the steps for a ![]() -secret sharing scheme with the help
-secret sharing scheme with the help
of the computer program Maple 16. It is![]() ,
, ![]() and hence
and hence![]() .
.
First the Dealer generates the shares for the participants.
![]()
He takes an explicit presentation
![]()
![]() as above. We first mention that the inequalities (10) hold for
as above. We first mention that the inequalities (10) hold for
![]()
and hence the set of the matrices
![]()
![]()
![]()
is a free generating set for a free group of rank 3.
2) The dealer chooses
![]()
and hence the secret is
![]()
3) Construction of the shares for the participants:
(a) First the dealer applies regular Nielsen transformations (NTs) simultaneously for both sets X and M to get Nielsen-equivalent sets U and N to X and M, respectively. These transformations are shown in Table 3 (see page 75) and Table 4 (see page 76).
The Dealer obtains the sets
![]()
and
![]()
(b) He gets the shares ![]() for the participants with
for the participants with ![]() and
and ![]() as follows:
as follows:
![]()
Table 3. Nielsen transformations (NTs) of the dealer I.
![]()
Table 4. Nielsen transformations (NTs) of the dealer II.
i) It is![]() .
.
ii) The dealer chooses the elements ![]() and gets the three sets
and gets the three sets
![]()
With the help of the ![]() the dealer gets the sets
the dealer gets the sets ![]() and
and ![]() which contain elements from the set
which contain elements from the set![]() . He puts the element
. He puts the element ![]() by which i is not contained in the set
by which i is not contained in the set ![]() for
for ![]() and
and![]() , into the set
, into the set![]() ..
..
![]()
![]()
![]()
Now we apply this to U and N to create the share-sets for the participants, respec- tively:
![]()
![]()
![]()
4) The Dealer distributes to each participant a tuple![]() . Participant
. Participant ![]() gets
gets![]() ,
, ![]() gets
gets ![]() and
and ![]() gets
gets![]() .
.
Assume the participants ![]() and
and ![]() come together to reconstruct the secret. They are able to generate the sets
come together to reconstruct the secret. They are able to generate the sets ![]() and
and![]() . The secret can be recovered as follows.
. The secret can be recovered as follows.
The participants apply regular Nielsen transformations step by step simultaneously for both sets U and N to get ![]() and
and![]() . The steps are shown in the Table 5 (see page 77) and Table 6 (see page 78).
. The steps are shown in the Table 5 (see page 77) and Table 6 (see page 78).
With the knowledge of the set ![]() the participants can reconstruct the secret easily. It is
the participants can reconstruct the secret easily. It is
![]()
Table 5. Nielsen transformations (NTs) from the participants I.
![]()
and hence it is
![]()
In general we can use any free matrix group F of rank ![]() for a
for a ![]() - secret sharing scheme as it is described in this section. The shares can be generated by the above method and are tuples
- secret sharing scheme as it is described in this section. The shares can be generated by the above method and are tuples ![]() with
with ![]() and
and![]() . Some other ideas for the secret S are
. Some other ideas for the secret S are
![]() (11)
(11)
![]() (12)
(12)
![]() (13)
(13)
![]()
Table 6. Nielsen transformations (NTs) from the participants II.
5. Another Secret Sharing Scheme Based on Nielsen Transformations
![]()
For a ![]() -secret sharing scheme the dealer chooses a Nielsen reduced set
-secret sharing scheme the dealer chooses a Nielsen reduced set![]() , with
, with![]() . The
. The ![]() are given as words in X. The secret is the sum
are given as words in X. The secret is the sum
![]() (14)
(14)
with ![]() the length of the word
the length of the word![]() .
.
The dealer does a regular Nielsen transformation on the set U to get the Nielsen- equivalent set V (see Figure 3).
Each participant![]() ,
, ![]() , gets one set
, gets one set![]() , as in the previous secret sharing scheme above.
, as in the previous secret sharing scheme above.
![]()
Figure 3. Regular Nielsen transformation.
If t of the n participants come together to reconstruct the secret, they combine their shares and get the set![]() . They have to find a Nielsen-reduced set
. They have to find a Nielsen-reduced set ![]() to V. They apply Nielsen transformations in a Nielsen reducing manner as described in [8] and [9] , and get from V a Nielsen-reduced set
to V. They apply Nielsen transformations in a Nielsen reducing manner as described in [8] and [9] , and get from V a Nielsen-reduced set![]() . The secret is the sum
. The secret is the sum
![]() (15)
(15)
because for each i it is ![]() for some j (see the proof of Corollary 3.1 in [10] ). From
for some j (see the proof of Corollary 3.1 in [10] ). From ![]() we get
we get ![]() by permutations and length preserving Nielsen transformations.
by permutations and length preserving Nielsen transformations.
This ![]() -secret sharing scheme is summarized in Table 7 (page 80).
-secret sharing scheme is summarized in Table 7 (page 80).
6. A Symmetric Key Cryptosystem Using Nielsen Transformations
In this section we introduce a symmetric key cryptosystem using Nielsen transfo- rmations. Before Alice and Bob are able to communicate with each other, they have to make some arrangements.
We speak about public parameters also in private key cryptosystems, because these are parameters which each person, also an eavesdropper, Eve, gets, if she looks at the sent ciphertext. Public parameters are also elements, which Alice and Bob communicate with each other publicly. It is also not a secret which plaintext alphabet is used for the communication.
Public Parameters.
They first agree on the following public parameters.
1) A finitely generated free group F with free generating set ![]() with
with![]() .
.
2) A plaintext alphabet ![]() with
with![]() .
.
4) A subset ![]() of automorphisms of H. It is
of automorphisms of H. It is![]() and the
and the![]() ,
, ![]() , pairwise different, are generated with the help of 0-1-sequence (of different length) and random numbers, see ( [5] , Section 4.4).
, pairwise different, are generated with the help of 0-1-sequence (of different length) and random numbers, see ( [5] , Section 4.4).
![]()
Table 7. Summary of the ![]() -secret sharing scheme using Nielsen transformations together with Nielsen reduced sets and free lengths of certain words.
-secret sharing scheme using Nielsen transformations together with Nielsen reduced sets and free lengths of certain words.
The set ![]() is part of the key space.
is part of the key space.
5) They agree on a linear congruence generator ![]() with a maximal period length.
with a maximal period length.
Private Parameters.
Now, they agree on the private parameters.
1) Alice and Bob choose an explicit Nielsen reduced set U with N elements, which are words in X. Such systems U are easily to construct (see Lemma 7 and Theorem 6 or also [8] and [9] ).
Now, it is ![]() a free subgroup of F with rank N. It is
a free subgroup of F with rank N. It is ![]() the set of all minimal Nielsen reduced sets with N elements in F, which is part of the key space.
the set of all minimal Nielsen reduced sets with N elements in F, which is part of the key space.
2) They use a one-to-one correspondence
![]() (16)
(16)
3) Alice and Bob agree on an automorphism![]() , hence
, hence ![]() is the common secret starting point
is the common secret starting point![]() , with
, with![]() , for the linear congruence generator. With this
, for the linear congruence generator. With this ![]() they are able to generate the sequence
they are able to generate the sequence ![]() (with z the number of the plaintext units, which are letters from A) of automorphisms of the set
(with z the number of the plaintext units, which are letters from A) of automorphisms of the set![]() , which they need for encryption and decryption, respectively.
, which they need for encryption and decryption, respectively.
Remark 21. If the explicit set![]() ,
, ![]() word in X, is used, then
word in X, is used, then ![]() is a free subgroup of F and with the automorphism
is a free subgroup of F and with the automorphism ![]() with
with![]() , the set
, the set ![]() is generated, which is Nielsen equivalent to the set U.
is generated, which is Nielsen equivalent to the set U.
The key space: The set ![]() of all minimal (with respect to a lexicographical order) Nielsen reduced set of F with N elements. The set
of all minimal (with respect to a lexicographical order) Nielsen reduced set of F with N elements. The set ![]() of 2128 randomly chosen automorphism of
of 2128 randomly chosen automorphism of![]() .
.
Private Key Cryptosystem.
Now, we explain the private key cryptosystem and look carefully at the steps for Alice and Bob.
Public knowledge:![]() ,
, ![]() with
with![]() ; plaintext alphabet
; plaintext alphabet ![]() with
with![]() ; the set
; the set![]() ; a linear congruence generator h.
; a linear congruence generator h.
Encryption and Decryption Procedure:
1) Alice and Bob agree privately on the private parameters: a set ![]() and an automorphism
and an automorphism![]() . They also know the one-to-one correspondence between U and A.
. They also know the one-to-one correspondence between U and A.
2) Alice wants to transmit the message
![]() (17)
(17)
with ![]() to Bob.
to Bob.
2.1) She generates with the linear congruence generator h and the knowledge of ![]() the z automorphisms
the z automorphisms![]() , which she needs for encryption. It is
, which she needs for encryption. It is![]() ,
, ![]() ,
, ![]() ,
,![]() .
.
2.2) The encryption is as follows.
![]() (18)
(18)
Recall that the one-to-one correspondence ![]() with
with![]() , for
, for![]() , holds. The ciphertext
, holds. The ciphertext
![]() (19)
(19)
is sent to Bob. The ![]() are called the ciphertext units and we do not perform cancell- ations between
are called the ciphertext units and we do not perform cancell- ations between ![]() and
and ![]() and the end of each
and the end of each ![]() is marked,
is marked, ![]() , for exa- mple with the symbol “
, for exa- mple with the symbol “![]() ”. On the one hand the ciphertext unit
”. On the one hand the ciphertext unit ![]() can be seen as a word in U, because the set
can be seen as a word in U, because the set ![]() is Nielsen equivalent to U and
is Nielsen equivalent to U and![]() , for
, for![]() , is an element in
, is an element in![]() . On the other hand it can be written as a word in X, because the explicit elements in U are words in X and so are the elements in the Nielsen equivalent set
. On the other hand it can be written as a word in X, because the explicit elements in U are words in X and so are the elements in the Nielsen equivalent set ![]() to U.
to U.
3) Bob gets the ciphertext
![]() (20)
(20)
with![]() ,
, ![]() , words in X. He knows where each ciphertext unit
, words in X. He knows where each ciphertext unit ![]() begins and ends. Hence, he gets the information that he has to use z automorphisms of F from the set
begins and ends. Hence, he gets the information that he has to use z automorphisms of F from the set ![]() for decryption. He has two possibilities for decryption.
for decryption. He has two possibilities for decryption.
3.1.a) With the knowledge of![]() , the set
, the set![]() , the linear congruence generator h and the number z, he computes for each automorphism
, the linear congruence generator h and the number z, he computes for each automorphism![]() ,
, ![]() , the set
, the set
![]() (21)
(21)
with ![]() written as a reduced word in X. Hence, with the one-to-one correspondence between U and A, he gets a one-to-one correspondence between the letters in the alphabet A and the words of the ciphertext depending on the automorphisms
written as a reduced word in X. Hence, with the one-to-one correspondence between U and A, he gets a one-to-one correspondence between the letters in the alphabet A and the words of the ciphertext depending on the automorphisms![]() . This is shown in Table 8 (page 82).
. This is shown in Table 8 (page 82).
With the knowledge of the Table 8 (page 82) the decryption is as follows
![]() (22)
(22)
He generates the plaintext message
![]() (23)
(23)
with![]() , from Alice.
, from Alice.
3.1.b) Bob knows the Nielsen reduced set U, hence with an algorithm as for example explained in the book ( [8] , page~33) he is able to write the elements ![]() as words in U. With the knowledge of the automorphism
as words in U. With the knowledge of the automorphism![]() , the set
, the set![]() , the linear congruence generator h and the number z, he gets the automorphisms
, the linear congruence generator h and the number z, he gets the automorphisms ![]() which Alice used for encryption of
which Alice used for encryption of![]() . Because of the fact that a one-to-one correspondence between A and U is used and the ciphertext unit
. Because of the fact that a one-to-one correspondence between A and U is used and the ciphertext unit ![]() is an image of an element in U under the automorphism
is an image of an element in U under the automorphism![]() , Bob knows with the automorphism
, Bob knows with the automorphism ![]() and the ciphertext unit
and the ciphertext unit ![]() written as word in U, the plaintext letter
written as word in U, the plaintext letter ![]() which corres- ponds to the ciphertext unit
which corres- ponds to the ciphertext unit![]() .
.
This cryptographic protocol is summarized in Table 9 (page 83).
Remark 22. As soon as Alice and Bob agree on the starting seed automorphism and the Nielsen reduced set U, Bob is able to calculate the first columns of Table 8 (page 82) for decryption (he does not know how many columns he will need because he does not know yet how long the plaintext from Alice will be). If he gets the ciphertext C from Alice, he only has to do a search in the table to get the corresponding plaintext units to
![]()
Table 9. Summary of the private key cryptosystem.
the ciphertext units. If columns are missing to decrypt the ciphertext, he calculates the missing columns. Thus, in Version 3.1.a. instead of Version 3.1.b. for decryption Bob is able to do calculations for decryption even before he knows the ciphertext.
Remark 23. The cryptosystem is a polyalphabetic system, that means, a word![]() , and hence a letter
, and hence a letter![]() , is encrypted differently at different positions in the plaintext, because different automorphisms are used during the encryption procedure for each ciphertext unit. Thus, for the ciphertext, a statistical frequency attack (see for instance [1] ) over the frequency of words, which correspond to letters in the plaintext alphabet, or groups of words, is useless.
, is encrypted differently at different positions in the plaintext, because different automorphisms are used during the encryption procedure for each ciphertext unit. Thus, for the ciphertext, a statistical frequency attack (see for instance [1] ) over the frequency of words, which correspond to letters in the plaintext alphabet, or groups of words, is useless.
It follows an example, in which for decryption a table (see Table 8 (page 82)) is used, which stores the ciphertext alphabet ![]() and is generated with the automorphisms Alice uses for encryption, see Example 24.
and is generated with the automorphisms Alice uses for encryption, see Example 24.
Additionally, in [5] an example is given, in which Bob knows the Nielsen reduced set U, hence with a known algorithm he is able to write the ciphertext as a sequence of words in U. With the automorphisms Alice uses for encryption he is able to decrypt the ciphertext correctly.
Example 24. This example was executed in GAP1. All details are given in Appendix A. Firstly, Alice and Bob agree on public parameters.
1) Let F be the free group on the free generating set![]() .
.
2) Let ![]() be the plaintext alphabet.
be the plaintext alphabet.
4) A set ![]() is determined. In this example we give the automorphisms, which Alice and Bob use for encryption and decryption, respectively, just at the mom- ent when they are needed.
is determined. In this example we give the automorphisms, which Alice and Bob use for encryption and decryption, respectively, just at the mom- ent when they are needed.
5) The linear congruence generator with maximal periodic length is
![]()
![]()
The private parameters for this example are the following:
1) Let ![]() be the explicit finitely generated free group, which is generated with the free generating set
be the explicit finitely generated free group, which is generated with the free generating set ![]() with words in X, for this example it is
with words in X, for this example it is
![]()
![]()
The starting automorphism ![]() is
is![]() , hence it is
, hence it is![]() . It is known, that
. It is known, that![]() ,
, ![]() , for
, for ![]() and
and![]() , therefore.
, therefore.
![]()
![]()
We now look at the encryption and decryption procedure for Alice and Bob.
2) With the above agreements Alice is able to encrypt her message
![]()
Her message is of length 4. She generates the ciphertext as follows:
2.1) First, she determines, with the help of the linear congruence generator ![]() with
with![]() and the starting seed
and the starting seed![]() , the four automorphisms
, the four automorphisms![]() ,
, ![]() , which she needs for encryption. It is
, which she needs for encryption. It is
![]()
![]()
The automorphisms are describable with the help of regular Nielsen transformations, it is
![]() ,
,
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]() ,
,
![]()
![]()
![]()
![]()
![]()
the Nielsen transformations are applied from the left to the right.
2.2) Secondly, she encrypts her message. The ciphertext is
![]()
The ciphertext C is written as words in X, it is
![]()
3) Bob gets the ciphertext
![]()
from Alice. Thus, he knows that he needs 4 automorphisms for decryption.
3.1) Bob knows the set U, the linear congruence generator h and the starting seed automorphism![]() . For decryption he uses tables like Table 8 (page 82).
. For decryption he uses tables like Table 8 (page 82).
Now, he is able to compute for each automorphism ![]() the set
the set![]() ,
, ![]() , and to generate Table 10 (page 86) and Table 11 (page 87).
, and to generate Table 10 (page 86) and Table 11 (page 87).
With these tables he is able to reconstruct the plaintext from Alice. He searches for the plaintext element ![]() the ciphertext unit
the ciphertext unit ![]() in the column
in the column![]() ,
, ![]() , and hence gets the alphabet letter
, and hence gets the alphabet letter ![]() for a
for a![]() . Therefore, he decrypts the ciphertext to the message.
. Therefore, he decrypts the ciphertext to the message.
![]()
Table 10. Correspondence: Plaintext alphabet to ciphertext alphabet I.
![]()
Table 11. Correspondence: Plaintext alphabet to ciphertext alphabet II.
![]()
![]()
Security 25. The cryptosystem is a polyalphabetic system, that means, a word![]() , and hence a letter
, and hence a letter![]() , is encrypted differently at different positions in the plaintext, because different automorphisms are used during the encryption procedure for each ciphertext unit. Thus, for the ciphertext, a statistical frequency attack (see for instance [1] ) over the frequency of words, which correspond to letters in the plaintext alphabet, or groups of words, is useless.
, is encrypted differently at different positions in the plaintext, because different automorphisms are used during the encryption procedure for each ciphertext unit. Thus, for the ciphertext, a statistical frequency attack (see for instance [1] ) over the frequency of words, which correspond to letters in the plaintext alphabet, or groups of words, is useless.
The security depends on the fact, that the set U is private. Note, that the ciphertext units ![]() are elements in
are elements in![]() , with
, with![]() . An eavesdropper, Eve, knows that the elements of the set U, which where used for the encryption, can be found in the ball
. An eavesdropper, Eve, knows that the elements of the set U, which where used for the encryption, can be found in the ball ![]() of the Cayley graph from F, with
of the Cayley graph from F, with
![]() (24)
(24)
and ![]() ciphertext units of an intercepted ciphertext
ciphertext units of an intercepted ciphertext
![]() (25)
(25)
The symbol “![]() ” marks the end of each ciphertext unit
” marks the end of each ciphertext unit![]() ,
,![]() .
.
Let
![]() (26)
(26)
be the set of ciphertext units and let ![]() be a Nielsen reduced set of
be a Nielsen reduced set of![]() , hence the
, hence the
group![]() , generated by
, generated by![]() , is a free subgroup of
, is a free subgroup of ![]() and
and![]() . The
. The
main security certification depends on the fact, that for a single subset V of ![]() with K elements Eve finds a Nielsen reduced set in the running time
with K elements Eve finds a Nielsen reduced set in the running time![]() , with
, with ![]() the maximum over the free length of the elements in the subset V with K primitive elements, but she has to test all possible subsets of K elements for which she needs exponential running time, because the number of primitive elements grows exponen- tially with the free length, here with
the maximum over the free length of the elements in the subset V with K primitive elements, but she has to test all possible subsets of K elements for which she needs exponential running time, because the number of primitive elements grows exponen- tially with the free length, here with![]() . She searches in a ball
. She searches in a ball![]() , with
, with ![]() for these primitive elements.
for these primitive elements.
A subset of V is also known, it is ![]() but she has to put all other primitive elements to this set and proves if
but she has to put all other primitive elements to this set and proves if![]() , which is Nielsen reduced to V, is of order N and
, which is Nielsen reduced to V, is of order N and
hence a candidate for U.
A more detailed cryptographical analysis can be found in [5] and there are also three modifications given, which are summarized as follows:
1) We present a modification where the ciphertext is only one reduced word in X instead of a sequence of words, in this case it is possible that additional information is needed for decryption, thus these are sent with the ciphertext if required. The ciphertext can be interpreted as words in X and as words in U, thus the additional information could be given about the ciphertext written as a word in U or as a word in X.
Security: The security certification is extended to the fact that Eve is in general not able to identify the beginning and end of a ciphertext unit![]() ,
,![]() . There could also be cancellations, which she is not able to recognize. Eve is neither able to determine the number
. There could also be cancellations, which she is not able to recognize. Eve is neither able to determine the number ![]() because she does not know what the ciphertext units
because she does not know what the ciphertext units ![]() exactly look like, nor is she able to generate the set
exactly look like, nor is she able to generate the set![]() . This worsens her attacks of the unmodified cryptographic protocol above.
. This worsens her attacks of the unmodified cryptographic protocol above.
2) We present a modification, which uses a faithful representation from F into the special linear group ![]() such that the ciphertext is a sequence of matrices in
such that the ciphertext is a sequence of matrices in![]() . Furthermore, a variation can be used, where the ciphertext is not a sequence of matrices but a sequence of entries of matrices. This reduces the space for the ciphertext and the memory space for the decryption table.
. Furthermore, a variation can be used, where the ciphertext is not a sequence of matrices but a sequence of entries of matrices. This reduces the space for the ciphertext and the memory space for the decryption table.
Security: The security certification is extended to the fact, that there is no algorithm known to solve the (constructive) membership problem for (discrete) free subgroups of ![]() which are of rank greater than or equal to 2 and not subgroups of
which are of rank greater than or equal to 2 and not subgroups of![]() , see [15] . Therefore, the attack which uses a Cayley graph and automorphisms of
, see [15] . Therefore, the attack which uses a Cayley graph and automorphisms of ![]() in the unmodified cryptographic protocol is not realizable in this modification.
in the unmodified cryptographic protocol is not realizable in this modification.
3) We present a modification, which utilizes the negative solution of Hilbert's Tenth Problem. Instead of a presentation of the ciphertext as a sequence of matrices in ![]() the ciphertext is represented as a sequence of matrices in
the ciphertext is represented as a sequence of matrices in ![]() with
with![]() , the integral polynomial ring in
, the integral polynomial ring in ![]() variables. Here we get two subcases, the first applies the modification with Hilbert's Tenth Problem on a text given as a sequence of words in X and the second applies it to a text given as a sequence of words in U.
variables. Here we get two subcases, the first applies the modification with Hilbert's Tenth Problem on a text given as a sequence of words in X and the second applies it to a text given as a sequence of words in U.
Security: The security certification is extended to Hilbert’s Tenth Problem. In addition the security is improved by the fact, that for each encryption Alice and Bob can take privately ephemeral matrices in![]() ,
, ![]() , with the property that the common private point
, with the property that the common private point ![]() generates the correct matrices in
generates the correct matrices in![]() . This gives randomness to ciphertexts, which complicates attacks for Eve. The attack which uses a Cayley graph and automorphisms of
. This gives randomness to ciphertexts, which complicates attacks for Eve. The attack which uses a Cayley graph and automorphisms of ![]() in the unmodified cryptographic protocol is not realizable in this modification.
in the unmodified cryptographic protocol is not realizable in this modification.
Remark 26. In [5] are two more private key cryptosystems given, which use finitely generated free groups, Nielsen transformations and automorphisms on finitely generated free group. The first one uses automorphisms on F instead of a subgroup of F, as in the above described private key cryptosystem. It also has three modifications, which use the ideas for the modifications above. The second protocol uses automo- rphisms on plaintext units and in addition randomly chosen ephemeral keys (matrices of![]() ), which give randomness to the ciphertexts.
), which give randomness to the ciphertexts.
7. Cryptosystem with Nielsen Transformation Inspired by the ElGamal Cryptosystem
Now we describe a public key cryptosystem for Alice and Bob which is inspired by the ElGamal cryptosystem (see [16] or ( [2] , Section 1.3)), based on discrete logarithms, that is:
1) Alice and Bob agree on a finite cyclic group G and a generating element![]() .
.
2) Alice picks a random natural number a and publishes the element![]() .
.
3) Bob, who wants to send a message ![]() to Alice, picks a random natural number b and sends the two elements
to Alice, picks a random natural number b and sends the two elements ![]() and
and![]() , to Alice. Note that
, to Alice. Note that![]() .
.
4) Alice recovers![]() .
.
For the new public key cryptosystem in this section let![]() ,
, ![]() , be the free generating set of the finitely generated free group
, be the free generating set of the finitely generated free group![]() . It is
. It is![]() . The message is an element
. The message is an element![]() ,
, ![]() denotes the set of all freely reduced words with letters in
denotes the set of all freely reduced words with letters in![]() . Public are the free group F, its free generating set X and an element
. Public are the free group F, its free generating set X and an element![]() . The automorphism f, given as a Nielsen transformation or a Whitehead-Automorphism (see for instance the book [17] ), should be chosen randomly, an approach is given in ( [5] , Section 4.4).
. The automorphism f, given as a Nielsen transformation or a Whitehead-Automorphism (see for instance the book [17] ), should be chosen randomly, an approach is given in ( [5] , Section 4.4).
An ElGamal like public key cryptosystem, with public parameters determined by Alice, is now as follows:
Public parameters: The finitely generated free group![]() , a freely reduced word
, a freely reduced word ![]() in the free group F and an automorphism
in the free group F and an automorphism ![]() of infinite order.
of infinite order.
Encryption and Decryption Procedure:
1) Alice chooses privately a natural number n and publishes the element![]() .
.
2) Bob picks privately a random ![]() and his message
and his message![]() . The number t is an ephemeral key for this message, he changes t for each message m, because of Remark 27. He calculates the freely reduced elements
. The number t is an ephemeral key for this message, he changes t for each message m, because of Remark 27. He calculates the freely reduced elements
![]() (27)
(27)
He sends the ciphertext ![]() to Alice.
to Alice.
3) Alice calculates
![]() (28)
(28)
and gets the message m.
The ElGamal like public key cryptosystem is summarized in Table 12 (page 90).
Remark 27. It is important that different random ephemeral keys t are used to encrypt different messages. As it is for the standard ElGamal cryptosystem (see [18] ). Suppose that Bob uses the same ephemeral key t to encrypt two messages ![]() and
and ![]() and assume that
and assume that ![]() is known. The ciphertext pairs are
is known. The ciphertext pairs are ![]() and
and![]() , with
, with![]() ,
, ![]() and
and![]() . Eve only has to calculate
. Eve only has to calculate ![]() to get the message
to get the message![]() .
.
Security 28. A possible attacker, Eve, can see the elements![]() . She does not know the free length of m and the cancellations between m and
. She does not know the free length of m and the cancellations between m and ![]() in
in![]() . It could be possible that m is completely canceled by the first letters of
. It could be possible that m is completely canceled by the first letters of![]() . Hence, she cannot determine m from the given
. Hence, she cannot determine m from the given![]() . Eve just sees words,
. Eve just sees words, ![]() and
and![]() ,
,
![]()
Table 12. Summary of the ElGamal like public key cryptosystem using automorphisms on a finitely generated free group F.
in the free generating set X from which it is unlikely to realize the exponents n and t, that is, the private keys from Alice and Bob, respectively. The security is based on the Diffie-Hellman problem and discrete logarithm problem in cyclic subgroups of automorphisms in free groups.
Variation 29. We give some ideas to enhance the security, they can also be combined:
1) The element ![]() could be taken as a common private secret between Alice and Bob. They could use for example the Anshel-Anshel-Goldfeld key exchange protocol (see for instance [2] ) to agree on the element a.
could be taken as a common private secret between Alice and Bob. They could use for example the Anshel-Anshel-Goldfeld key exchange protocol (see for instance [2] ) to agree on the element a.
2) Alice and Bob agree on a faithful representation from F into the special linear group
of all ![]() matrices with entries in
matrices with entries in![]() , that is,
, that is,![]() . Now,
. Now, ![]() and Bob sends the element
and Bob sends the element ![]() instead of
instead of![]() ; c and
; c and ![]() remain the same. Therefore, Alice calculates
remain the same. Therefore, Alice calculates ![]() and hence the message
and hence the message![]() . This variation in addition extends the security certification to the constructive membership problem in the matrix group
. This variation in addition extends the security certification to the constructive membership problem in the matrix group ![]() (see [15] ).
(see [15] ).
We now explain this variation in more details.
Alice needs a faithful representation of ![]() into
into ![]() such that
such that
![]()
![]() (29)
(29)
![]() (30)
(30)
Thus, each ![]() has at least one entry which is an element in
has at least one entry which is an element in![]() .
.
(a) The public element from Alice is as before![]() , with private key
, with private key![]() .
.
(b) Bob chooses privately a message![]() , a random
, a random ![]() and calculates
and calculates
![]() as before. After this he computes
as before. After this he computes ![]()
and writes it as a word in Y whereby he used the assignment ![]() for
for![]() . We denote
. We denote ![]() as
as ![]() when
when ![]() is written as a word in Y. The element
is written as a word in Y. The element ![]() is a reduced word in Y. Bob’s element
is a reduced word in Y. Bob’s element ![]() is now a reduced word in
is now a reduced word in![]() . He applies the faithful representation g on this element. It is
. He applies the faithful representation g on this element. It is
![]() (31)
(31)
Instead of ![]() he sends
he sends ![]() to Alice.
to Alice.
(c) Firstly, Alice calculates ![]() and hence gets the same element
and hence gets the same element ![]() as
as
Bob, because
![]() (32)
(32)
Secondly, she writes ![]() as a word in Y, thus she gets
as a word in Y, thus she gets![]() . Thirdly, she uses the faithful representation g to calculate
. Thirdly, she uses the faithful representation g to calculate ![]() and together with
and together with ![]() she gets
she gets
![]() (33)
(33)
She gets a matrix in ![]() and she knows that this matrix is a word in the letters of
and she knows that this matrix is a word in the letters of![]() ,
, ![]() , hence there is an algorithm (see for instance [8] ) to write
, hence there is an algorithm (see for instance [8] ) to write ![]() as a word in
as a word in ![]() and therefore as a word in X. Thus, she is able to recon-struct m.
and therefore as a word in X. Thus, she is able to recon-struct m.
An eavesdropper, Eve, gets a matrix ![]() and she is not able to write it as a word in the set
and she is not able to write it as a word in the set ![]() (because there is no algorithm known to solve the constructive membership problem in a (discrete) free subgroup of
(because there is no algorithm known to solve the constructive membership problem in a (discrete) free subgroup of ![]() of rank greater than or equal to 2 (see [15] ), which is not in
of rank greater than or equal to 2 (see [15] ), which is not in![]() ). Thus, she cannot get the situation as in the cryptosystem without the faithful representation g into
). Thus, she cannot get the situation as in the cryptosystem without the faithful representation g into![]() . There is no hint for the message m, instead of the system above in which it is possible that an initial segment of m is visible whereby Eve does not know how long this initial segment is and if it is relay visible. Thus, this variation extends the security certification to the constructive membership problem in the matrix group
. There is no hint for the message m, instead of the system above in which it is possible that an initial segment of m is visible whereby Eve does not know how long this initial segment is and if it is relay visible. Thus, this variation extends the security certification to the constructive membership problem in the matrix group![]() .
.
We now end this section with an example.
Example 30. This example, is a very small one and it is just given for illustration purposes. The calculations were done with GAP, see Appendix B. Bob wants to send a message to Alice.
The public parameters are the free group F of rank 3 with free generating set![]() , the freely reduced word
, the freely reduced word![]() , with
, with ![]() and the automor- phism
and the automor- phism![]() , which is given, for this example, by the regular Nielsen transform- ation:
, which is given, for this example, by the regular Nielsen transform- ation:![]() , thus, it is:
, thus, it is:
![]()
![]()
![]()
![]()
1) Alice’s private key is![]() . Thus, she gets the automorphism
. Thus, she gets the automorphism
![]()
![]()
![]()
![]()
Her public key is
![]()
2) Bob privately picks the ephemeral key ![]() and gets the automorphism
and gets the automorphism
![]()
![]()
![]()
![]()
His message for Alice is![]() . He calculates
. He calculates
![]()
and
![]()
The ciphertext for Alice is the tuple![]() .
.
3) Alice first computes
![]()
and gets m by
![]()
8. Conclusions
A. Shamir’s secret sharing protocol (see [6] ) has become the standard method for solving the ![]() -secret sharing problem. The introduced secret sharing schemes are of mathematical interest.
-secret sharing problem. The introduced secret sharing schemes are of mathematical interest.
In contrast to other secret sharing schemes the part for the participants at the combinatorial secret sharing scheme, see Section 3, is very easy, they only have to add up m elements. The (time) expensive part is the part of the dealer, who has to generate the sets ![]() for the participants. In contrast to Shamir's scheme, where the part of the dealer is the easier one and the participants have to do polynomial interpolation to reconstruct the secret.
for the participants. In contrast to Shamir's scheme, where the part of the dealer is the easier one and the participants have to do polynomial interpolation to reconstruct the secret.
The secret sharing scheme of Section 4 uses combinatorial group theory, especially Nielsen transformations and finitely generated free groups. It is mathematically a very interesting cryptographic protocol, which serves very good as a basis to develop other cryptographic protocol. In addition the secret sharing scheme of Section 5 is also a mathematically very interesting cryptographic protocol. Both secret sharing schemes are the basis for the newly developed cryptosystems.
In comparison to the standard cryptosystems which are mostly based on number theory we explained two cryptosystems which use combinatorial group theory. The first cryptosystem in Section 6 is a kind of a one-time pad, which choice of the random sequence for encryption is not number-theoretic. Especially the modifications with matrices are of interest for cryptography. If the symmetric key cryptosystem is used together with the second modification, which uses a faithful representation into![]() , then the system is secure and the security depends on the unknown solution of the (constructive) membership problem in the used matrix groups. If it is used together with the third modification, which uses matrices in
, then the system is secure and the security depends on the unknown solution of the (constructive) membership problem in the used matrix groups. If it is used together with the third modification, which uses matrices in![]() ,
, ![]() ,
, ![]() , then the system is secure and the security depends in addition on the negative solution of Hilbert’s Tenth Problem. Moreover, we get also randomness to each ciphertext by the ephemeral matrices which the encrypter used for encryption. To generate these ephemeral matrices he only needs the common secret point
, then the system is secure and the security depends in addition on the negative solution of Hilbert’s Tenth Problem. Moreover, we get also randomness to each ciphertext by the ephemeral matrices which the encrypter used for encryption. To generate these ephemeral matrices he only needs the common secret point![]() , this improves also the security. Altogether, we get interesting new private key cryptosystems, which use non-commutative groups and are based on combinatorial group theory and not only on number theory. They provide other options for private key cryptosystems which are based on combinatorial group theory. The second cryptosystem in Section 7 is similar to the ElGamal cryptosystem (see [16] ), which is easier to handle. The ElGamal cryptosystem is based on the discrete logarithm problem over a finite field. If this problem should eventually be solved we introduced here an alternative system, which is not based on number theory.
, this improves also the security. Altogether, we get interesting new private key cryptosystems, which use non-commutative groups and are based on combinatorial group theory and not only on number theory. They provide other options for private key cryptosystems which are based on combinatorial group theory. The second cryptosystem in Section 7 is similar to the ElGamal cryptosystem (see [16] ), which is easier to handle. The ElGamal cryptosystem is based on the discrete logarithm problem over a finite field. If this problem should eventually be solved we introduced here an alternative system, which is not based on number theory.
For further research one could search for other cryptographic protocols, which can be based on Nielsen transformations, for example a public key cryptosystem which is not ElGamal like or a key exchange protocol. There is no algorithm known to solve the (constructive) membership problem for (discrete) free subgroups of rank equal or greater than 2 in![]() . Thus, the following questions appear: Are there quantum algorithms for solving the (constructive) membership problem in
. Thus, the following questions appear: Are there quantum algorithms for solving the (constructive) membership problem in![]() ? Are there quantum algorithms for solving other problems in combinatorial group theory, which are used in cryptography?
? Are there quantum algorithms for solving other problems in combinatorial group theory, which are used in cryptography?
Appendix
We now give the computer code in GAP2 for Example 24 and Example 30. Therefore we use the FGA3 package in GAP and also Nielsen transformations.
If there are Nielsen transformations of type ![]() one after another we can do them in one step. For example if the Nielsen transformations
one after another we can do them in one step. For example if the Nielsen transformations ![]() are applied to a set
are applied to a set ![]() we write instead of
we write instead of
![]()
the following
![]()
A. Calculations in GAP for Example 24
Alice and Bob use the free group![]() , with free generating set
, with free generating set![]() , and the explicit free subgroup
, and the explicit free subgroup ![]() of F with free generating set
of F with free generating set![]() ,
, ![]() words in X, they choose
words in X, they choose
![]()
![]()
In GAP they define
LoadPackage("FGA");;
F:=FreeGroup("x", "y", "z");;
AssignGeneratorVariables(F);;
u1:=x*y*z;;
u2:=y*z*y^-1;;
u3:=x^-1*z*x^-1;;
u4:=y^-1*x^2;;
u5:=z^-1*x*y*x;;
u6:=z^-1*y*x^-1;;
u7:=x^3*y;;
u8:=y^3*z^-2;;
FU:=Group(u1, u2, u3, u4, u5, u6, u7, u8);;
and prove that U is a Nielsen reduced set with the operation
> FreeGeneratorsOfGroup(FU)
which gives a Nielsen reduced generator set for the group FU:
gap> Free Generators Of Group (FU);
[x*y*z, y*z*y^-1, x^-1*z*x^-1, y^-1*x^2, z^-1*x*y*x,\
z^-1*y*x^-1, x^3*y, y^3*z^-2 ]
Alice knows the linear congruence generator h hence she can get the 4 required automorphisms of the set ![]() to encrypt her message.
to encrypt her message.
These automorphisms are describable with Nielsen transformations as follows:
Automorphism![]() :
:
![]()
Hence, the automorphism is
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Automorphism![]() :
:
![]()
Hence, the automorphism is
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Automorphism![]() :
:
![]()
Hence, the automorphism is
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Automorphism![]() :
: ![]()
![]()
Hence, the automorphism is
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
In GAP she defines for the automorphisms:
#Automorphism f_{u_1}
u11:=u1*u7*u2*u4;;
u12:=u2*u4*u3*u4^2;;
u13:=u3*u4^2;;
u14:=u4*u6*u5^-1*u1*u7;;
u15:=u5^-1*u1*u7;;
u16:=u6*u3*u4^2;;
u17:=u6^-1*u4^-1*u7*u8;;
u18:=u8*u1*u7;;
#Automorphism f_{u_2}
u21:=u3^-1*u1^-1*u2*u4;;
u22:=u2^-1*u8*u6*u5;;
u23:=u3*u5*u4^-2;;
u24:=u2*u4*u7*u6*u5;;
u25:=u5*u2^-1*u6*u5;;
u26:=u6*u5*u2*u4;;
u27:=u7*u6*u5;;
u28:=u8*u4^-1*u2^-1;;
#Automorphism f_{u_3}
u31:=u1*u2^-1*u7^-1*u3^-1*u8;;
u32:=u2^-1*u3*u7;;
u33:=u3*u7*u4*u8^-2;;
u34:=u4*u8^-2;;
u35:=u5^-1*u6*u3;;
u36:=u6*u2^3*u7;;
u37:=u7*u4*u8^-2;;
u38:=u7^-1*u3^-1*u8;;
#Automorphism f_{u_4}
u41:=u4*u3*u1;;
u42:=u3*u2^-1*u4*u3;;
u43:=u4*u3*u5*u2*u3^-1;;
u44:=u4^-1*u5*u2*u3^-1;;
u45:=u5*u2*u3^-1;;
u46:=u6*u2*u4*u3*u1;;
u47:=u7*u4^-1*u3*u2^-1;;
u48:=u8*u2^3*u3^-1*u4^-1;;
Hence, to get the ciphertext
![]()
as a word in X, she calculates in GAP:
gap > u11;
x*y*z*x^3*y^2*z*y^-2*x^2
gap> u24;
y*z*y^-2*x^5*y*z^-1*y*x^-1*z^-1*x*y*x
gap> u37;
x^5*(z^2*y^-3)^2
gap> u42;
x^-1*z*x^-1*y*z^-1*y^-2*x*z*x^-1
Thus, the ciphertext is
![]()
and this is sent to Bob.
For decryption Bob calculates the tables Table 10 (page 86) and Table 11 (page 87). For this he chooses the automorphisms in![]() , which Alice also used. In GAP it is:
, which Alice also used. In GAP it is:
gap> u11; u12; u13; u14; u15; u16; u17; u18;
x*y*z*x^3*y^2*z*y^-2*x^2
y*z*y^-2*x*z*x^-1*(y^-1*x^2)^2
x^-1*z*x^-1*(y^-1*x^2)^2
y^-1*x^2*z^-1*y*x^-2*y^-1*x^-1*z*x*y*z*x^3*y
x^-1*y^-1*x^-1*z*x*y*z*x^3*y
z^-1*y*x^-2*z*x^-1*(y^-1*x^2)^2
x*y^-1*z*x^-2*y*x^3*y^4*z^-2 y^3*z^-2*x*y*z*x^3*y
gap> u21; u22; u23; u24; u25; u26; u27; u28;
(x*z^-1)^2*y^-1*x^-1*y*z*y^-2*x^2
y*z^-1*y^2*z^-3*y*x^-1*z^-1*x*y*x
x^-1*z*x^-1*z^-1*x*(y*x^-1)^2*x^-1*y
y*z*y^-2*x^5*y*z^-1*y*x^-1*z^-1*x*y*x z^-1*(x*y)^2*z^-1*y^-1*z^-1*y*x^-1*z^-1*x*y*x z^-1*y*x^-1*z^-1*(x*y)^2*z*y^-2*x^2
x^3*y*z^-1*y*x^-1*z^-1*x*y*x
y^3*z^-2*x^-2*y^2*z^-1*y^-1
gap> u31; u32; u33; u34; u35; u36; u37; u38;
x*y*z*y*z^-1*y^-2*x^-2*z^-1*x*y^3*z^-2
y*z^-1*y^-1*x^-1*z*x^2*y
x^-1*z*x^4*(z^2*y^-3)^2
y^-1*x^2*(z^2*y^-3)^2
x^-1*y^-1*x^-1*y*x^-2*z*x^-1
z^-1*y*x^-1*y*z^3*y^-1*x^3*y
x^5*(z^2*y^-3)^2
y^-1*x^-2*z^-1*x*y^3*z^-2
gap> u41; u42; u43; u44; u45; u46; u47; u48;
y^-1*x*z*y*z
x^-1*z*x^-1*y*z^-1*y^-2*x*z*x^-1
y^-1*x*z*x^-1*z^-1*(x*y)^2*z*y^-1*x*z^-1*x x^-2*y*z^-1*(x*y)^2*z*y^-1*x*z^-1*x
z^-1*(x*y)^2*z*y^-1*x*z^-1*x
z^-1*y*x^-1*y*z*y^-2*x*z*y*z
x^3*y*x^-2*y*x^-1*z*x^-1*y*z^-1*y^-1
y^3*z^-2*y*z^3*y^-1*x*z^-1*x^-1*y
With this information Bob is able to reconstruct the message![]() .
.
B. Calculations in GAP for Example 30
Alice defines the public parameters.
Let ![]() be the free generating set for a free subgroup of rank 3:
be the free generating set for a free subgroup of rank 3:
LoadPackage("FGA");;
F:=FreeGroup("x", "y", "z");;
AssignGeneratorVariables(F);;
Additionally she defines the freely reduced word ![]() and describes the automorphisms f with the following regular Nielsen transformation
and describes the automorphisms f with the following regular Nielsen transformation
![]()
hence the automorphism is
![]()
![]()
![]()
![]()
and she defines in GAP:
x1:=x*y^2;;
y1:=z^(-1);;
z1:=y^(-1)*z^(-1);;
Alice chooses as private key![]() , hence she must calculate the automorphism
, hence she must calculate the automorphism![]() . For this she calculates in GAP:
. For this she calculates in GAP:
#Calculate automorphism f^2=f^1(f^1)
x2:=x1*y1^2;;
y2:=z1^(-1);;
z2:=y1^(-1)*z1^(-1);;
gap> x2; y2; z2;
x*y^2*z^-2
z*y
z^2*y
#Calculate automorphism f^3=f^1(f^2)
x3:=x2*y2^2;;
y3:=z2^(-1);;
z3:=y2^(-1)*z2^(-1);;
gap> x3; y3; z3;
x*y^2*z^-1*y*z*y
y^-1*z^-2
(y^-1*z^-1)^2*z^-1
#Calculate automorphism f^5=f^2(f^3)
x5:=x3*y3^2*z3^(-2);;
y5:=z3*y3;;
z5:=z3^2*y3;;
gap> x5; y5; z5;
x*y^2*z^-1*y^2*z*(z*y)^2
y^-1*(z^-1*y^-1*z^-1)^2*z^-1
((y^-1*z^-1)^2*z^-1)^2*y^-1*z^-2
#Calculate automorphism f^7=f^2(f^5)
x7:=x5*y5^(2)*z5^(-2);;
y7:=z5*y5;;
z7:=z5^2*y5;;
gap> x7; y7; z7;
x*y^2*z^-1*y*(y*z)^2*(z*y*z^2*y)^2*z*y y^-1*((z^-1*y^-1*z^-1)^2*y^-1*z^-1)^2*z^-1*y^-1*z^-2 (((y^-1*z^-1)^2*z^-1)^2*y^-1*z^-2)^2*y^-1*(z^-1*y^-1*z^-1)^2*z^-1
Thus, the automorphism ![]() is
is
![]()
![]()
![]()
![]()
Her public key is![]() :
:
c:=x7^2*y7*z7^(-2)*y7;;
gap> c;
(x*y^2*z^-1*y*(y*z)^2*(z*y*z^2*y)^2*z*y)^2*(z^2*y)^2*\ ((z*y*z)^2*y*z)^2*z*y*z^2*y*z^-1
Bob is now able to send a message to Alice. Let ![]() be the message for Alice. He chooses the ephemeral key
be the message for Alice. He chooses the ephemeral key ![]() and hence calculates the automorphism
and hence calculates the automorphism ![]() in GAP as follows:
in GAP as follows:
m:=z^-2*y^2*z*x^2*y^-1*x^-1;;
#Calculate automorphism f^2=f^1(f^1)
x2:=x1*y1^2;;
y2:=z1^(-1);;
z2:=y1^(-1)*z1^(-1);;
gap> x2; y2; z2; x*y^2*z^-2 z*y z^2*y
#Calculate automorphism f^3=f^1(f^2)
x3:=x2*y2^2;;
y3:=z2^(-1);;
z3:=y2^(-1)*z2^(-1);;
gap> x3; y3; z3;
x*y^2*z^-1*y*z*y
y^-1*z^-2
(y^-1*z^-1)^2*z^-1
#Calculate automorphism f^5=f^2(f^3)
x5:=x3*y3^2*z3^(-2);;
y5:=z3*y3;;
z5:=z3^2*y3;;
gap> x5; y5; z5;
x*y^2*z^-1*y^2*z*(z*y)^2
y^-1*(z^-1*y^-1*z^-1)^2*z^-1
((y^-1*z^-1)^2*z^-1)^2*y^-1*z^-2
Hence, the automorphism ![]() is
is
![]()
![]()
![]()
![]()
He now calculates his ciphertext ![]() for Alice with
for Alice with ![]() and
and ![]() in GAP:
in GAP:
#c22:=f^5(c)
c22:=(x5*y5^2*z5^(-1)*y5*(y5*z5)^2*(z5*y5*z5^2*y5)^2*z5*y5)^2*\ (z5^2*y5)^2*((z5*y5*z5)^2*y5*z5)^2*z5*y5*z5^2*y5*z5^(-1);;
c1:=m*c22;;
gap> c1;
z^-2*y^2*z*x^2*(y*z^-1)^2*((z^-1*y^-1*z^-2*y^-1)^2\ *z^-2*y^-1)^2*(z^-1*y^-1*z^-1)^2*z^-1*y^-1*((((z^-\ 1*y^-1*z^-1)^2*y^-1*z^-1)^2*z^-1*y^-1*z^-1*y^-1*z^\ -1)^2*(z^-1*y^-1*z^-2*y^-1)^2*z^-1*y^-1*z^-1)^2*((\ z^-1*y^-1*z^-2*y^-1)^2*z^-2*y^-1)^2*(z^-1*y^-1*z^-\ 1)^2*z^-1*x*y^2*z^-1*y*(z^-1*(((z^-1*y^-1*z^-2*y^-\ 1)^2*z^-2*y^-1)^2*(z^-1*y^-1*z^-1)^2*z^-1*y^-1)^3*\ (z^-1*y^-1*z^-1)^2*y^-1*z^-1*((z^-1*y^-1*z^-2*y^-1\
)^2*z^-2*y^-1)^2*(z^-1*y^-1*z^-1)^2*y^-1)^3*z^-1*(\ (z^-1*y^-1*z^-2*y^-1)^2*z^-2*y^-1)^2*(z^-1*y^-1*z^-1)^2*\
y^-1*z^-1*y
#c2:=f^5(a)
c2:=x5^2*y5*z5^(-2)*y5;;
gap> c2;
(x*y^2*z^-1*y^2*z*(z*y)^2)^2*z^2*y*(z*y*z)^2*z*y*z^-1
Bob sends ![]() to Alice. Alice gets the message m by calculating
to Alice. Alice gets the message m by calculating
![]()
In GAP she computes:
#dc:=f^7(c2)
dc:=(x7*y7^2*z7^(-1)*y7^2*z7*(z7*y7)^2)^2*z7^2*y7*\ (z7*y7*z7)^2*z7*y7*z7^(-1);;
gap> dc;
(x*y*(y*z^-1)^2*((z^-1*y^-1*z^-2*y^-1)^2*z^-2*y^-1\
)^2*(z^-1*y^-1*z^-1)^2*z^-1*y^-1*((((z^-1*y^-1*z^-\ 1)^2*y^-1*z^-1)^2*z^-1*y^-1*z^-1*y^-1*z^-1)^2*(z^-\ 1*y^-1*z^-2*y^-1)^2*z^-1*y^-1*z^-1)^2*((z^-1*y^-1*\ z^-2*y^-1)^2*z^-2*y^-1)^2*(z^-1*y^-1*z^-1)^2*z^-1)\ ^2*y^-1*(((z^-1*y^-1*z^-1)^2*y^-1*z^-1)^2*z^-1*y^-\ 1*z^-1*y^-1*z^-1)^2*(z^-1*y^-1*z^-2*y^-1)^2*z^-1*y\ ^-1*z^-1*((((z^-1*y^-1*z^-2*y^-1)^2*z^-2*y^-1)^2*(\ z^-1*y^-1*z^-1)^2*z^-1*y^-1)^2*((z^-1*y^-1*z^-1)^2\ *y^-1*z^-1)^2*z^-1*y^-1*z^-2*y^-1)^2*(((z^-1*y^-1*\ z^-1)^2*y^-1*z^-1)^2*z^-1*y^-1*z^-1*y^-1*z^-1)^2*(\ z^-1*y^-1*z^-2*y^-1)^2*z^-1*y^-1*z^-1*y
gap> dc^-1;
y^-1*(((((z*y)^2*z)^2*z*y*z)^2*z*y*(z*y*z)^2)^2*z*\ y*((z*y*z)^2*y*z)^2*z*y*z)^2*(z*y*(((z*y*z)^2*y*z)\ ^2*z*y*z*y*z)^2*(z*y*z^2*y)^2*z)^2*y*(((((z^2*y)^2\ *z*y)^2*z^2*y*z*y)^2*z*(z*y*z^2*y)^2*z*y)^2*z*(z*y\ *z^2*y)^2*z^2*y*(((z*y*z)^2*y*z)^2*z*y*z*y*z)^2*(z\ *y*z^2*y)^2*z*(z*y^-1)^2*y^-1*x^-1)^2
gap> c1*dc^-1;
z^-2*y^2*z*x^2*y^-1*x^-1
Finally, she reconstructs the correct message
![]()
NOTES
![]()
1Groups, Algorithms and Programming [14] .
![]()
2Groups, Algorithms and Programming [14] .
3Free Group Algorithms. A GAP4 Package by Christian Sievers, TU Braunschweig.