1. Introduction
With the development of multimedia technology, computer technology and network technology, the digital multimedia can be completely reconstructed without any distortion. However, many new issues have emerged, such as the security of computer network transmission and the copyright protection of digital products [1]. For copyright protection application of digital multimedia, copyright owner generally embeds a watermarking signal (may be a number, a text or an image) into original digital multimedia to verify its copyright.
Current, most watermarking algorithms usually use gray-scale image as original cover signal. If the original cover image is color image, it can be as a three-dimensional signal and can be performed 3D transform firstly, and then embed watermarking signal into selected frequency domain coefficients [2] [3]. However, some researchers proposed color image digital watermarking algorithms embed directly watermarking signal into each channel or selected channel [1]. Besides, some researchers first convert color space from RGB to YCbCr or YUV and then select Y channel for watermarking embedding [4]-[10]. According to the watermarking embedding domain, digital watermarking algorithms can be classified into two categories: spatial domain algorithm and transform domain algorithm. Generally, spatial domain method has worse robustness performance than transform domain method. Hence, most watermarking algorithms usually embed watermarking signal into transform domain coefficients. For transform domain algorithms, first the cover image or image block is performed by DCT [4]-[10]. And then embed the watermarking signal into corresponding transform domain coefficients by proposed embedding rule.
In this paper, a new and blind robust RGB color image watermarking scheme based on 3D-DCT transform is proposed. Firstly, the original RGB color image is divided into non-overlapping blocks sized 8 × 8 × 3, and then performs 3D-DCT transform on each block. Secondly, embed a bit watermarking signal into each block’s 3D-DCT direct-current (DC) coefficient by quantization method. The proposed scheme can not only achieve good imperceptibility but also against the common image processing attacks, such as adding noise, filtering, cropping, JPEG compression, scaling and rotating. Compared with similar watermarking algorithm, it has a better robustness performance for most attacks.
The rest of the paper is organized as follows. Section 2 briefly defines 3D-DCT transform and its inverse transform. Section 3 proposes detailed watermarking embedding and extraction procedures. The corresponding experimental results are given in Section 4. Finally, the conclusions are drawn in Section 5.
2. 3D-DCT Transform
For a given 3D volume data sized , the 3D-DCT transform is defined as follows.
, the 3D-DCT transform is defined as follows.
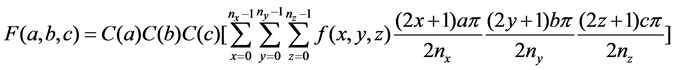 (1)
(1)
where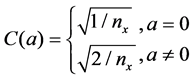 ,
, 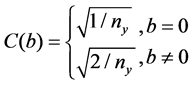 ,
, 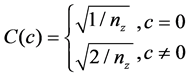 ,
, 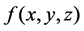 is the pixel value at position
is the pixel value at position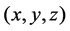 , and
, and 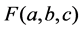 is 3D-DCT transform coefficient. The inverse 3D-DCT transform is defined as below.
is 3D-DCT transform coefficient. The inverse 3D-DCT transform is defined as below.
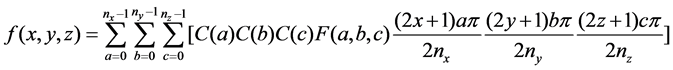 (2)
(2)
3. Proposed Scheme
For the proposed scheme, it consists of two phases: watermarking embedding procedure and extraction procedure.
3.1. Watermarking Embedding Procedure
The proposed watermarking embedding procedure is showed in Figure 1. The detailed steps are described as follows.
![]()
Figure 1. Flow diagram of watermarking embedding procedure.
Step 1. According to selected iteration times n, encrypt binary watermarking image with Arnold transform to obtain an encrypted watermarking image.
Step 2. For a given color image, it is divided into blocks sized 8 × 8 × 3.
Step 3. For each image block, 3D-DCT transform is performed on it.
Step 4. Suppose the watermarking embedding strength is Q. Modify the DC coefficient to embed watermarking signal. The watermarking embedding rule is defined as bellow.
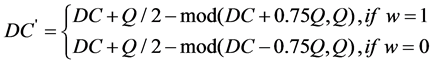 (3)
(3)
Step 5. Perform inverse 3D-DCT transform on new DC coefficient and other coefficients to obtain an embedded image block. When all blocks are embedded, the final watermarked image is obtained.
3.2. Watermarking Extraction Procedure
The watermarking extraction procedure is just the inverse procedure of the watermarking embedding procedure. The extraction procedure of the watermarking is blind, which does not need the original cover image. The watermarking extraction procedure is showed in Figure 2. The watermarking extraction steps can be described as below.
Step 1. For a given watermarked color image, it is divided into blocks sized 8 × 8 × 3.
Step 2. For each image block, 3D-DCT transform is performed on it.
Step 3. The binary watermarking bits can be extracted as follows.
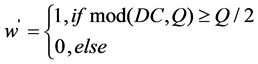 (4)
(4)
Step 4. According to selected iteration times n during watermarking embedding procedure, decrypt the extracted binary watermarking signal using inverse Arnold transform to obtain final extracted watermarking image.
4. Experimental Results
To test the robustness of proposed scheme, the original watermarking signal is a binary image sized 64 × 64 and is showed in Figure 3. The original cover images are four RGB true color image sized 512 × 512 × 3, namely Airplane, Sailboat, Peppers and Lena, as shown in Figure 4. The threshold Q of the proposed scheme defined in Section III is 60.
4.1. Imperceptibility Test
The Peak Signal to Noise Ratio (PSNR) is used to evaluate the distortion between the cover image  and the watermarked image
and the watermarked image , which is defined as below.
, which is defined as below.
![]()
Figure 2. Flow diagram of watermarking extraction procedure.
![]()
Figure 3. Original binary watermarking image.
![]()
Figure 4. Original images and watermarked images.
![]() (5)
(5)
The mean square error (MSE) between ![]() and
and ![]() is defined as blew.
is defined as blew.
![]() (6)
(6)
where M is width of original cover image.
The average PSNR between the original RGB image and its watermarked image are shown in Table 1. From Table 1, it can be seen that the proposed scheme and the algorithm in [3] have good visual quality of watermarked image. The average PSNR for proposed scheme are about 45.85 dB.
4.2. Robustness Test
The Normalized Cross-Correlation (NC) is used to measure the similarity between the original binary watermarking signal ![]() and the extracted binary watermarking signal
and the extracted binary watermarking signal![]() , which is defined as follows.
, which is defined as follows.
![]() (7)
(7)
where N is width of binary watermarking signal, ![]() symbol represents XOR operation.
symbol represents XOR operation.
To verify the robustness of the proposed scheme, the watermarked image is first attacked by common image processing. And then the embedded watermarking signal is extracted from attacked watermarked image. The results for watermarked Lena color image are shown in Figure 5 (The results of other images are similar with Lena image). It can be easily seen that the extracted watermarking images can be discriminated by human visual
system. These results show that the proposed scheme can achieve excellent robustness against common image processing attacks.
4.3. Performance Comparison
To test the superiority of the proposed scheme, we compared the proposed scheme with similar algorithm based on 3D-DCT in [3]. Under the same conditions, the results between PSNR and NC are shown in Table 2. From Table 2, it can be easily seen that the proposed scheme and the algorithm in [3] have almost same PSNR values after various attack, but the proposed scheme has better robustness performance.
Figure 6 gives the results between the proposed scheme and the algorithm in [3] on Lena image. From Figure 6, it can be easily seen that compared with the algorithm in [3], the proposed scheme has better robustness against most common image processing attacks.
![]()
Figure 5. Extracted watermarking image. Various attacks have been utilized independently to each component each time for Lena image. (a) Crop (1/4); (b) JPEG compression (Q = 80); (c) median filter (3 × 3); (d) rotate (10˚); (e) scale (0.5); (f) salt & peppers noise (0.001); (g) speckle noise (0.001); (h) wiener filter (3 × 3).
![]()
Table 1. PSNR comparisons between the proposed scheme and the algorithm in [3].
![]()
Table 2. PSNR and NC comparisons between the proposed scheme and the algorithm in [3].
5. Conclusion
In this paper, a new and blind color image watermarking scheme based on quantization modulation in 3D-DCT domain is proposed. The proposed scheme embeds only a bit into each block’s 3D-DCT DC coefficient by quantization rule. Experimental results show that the proposed scheme has good imperceptibility and robustness against common image processing attacks. The comparison results between the proposed scheme and the algorithm in [3] show that the proposed scheme has better performance for most attacks.
Acknowledgements
This work was funded by the Joint Foundation of Department of Science and Technology of Guizhou Province and Guizhou Normal University (Qian-Ke-He LH Zi [2014] 7041).