1. Introduction
The process of embedding secret messages into digital sound is known as audio steganography [1] . The basic model of audio steganography consists of carrier (audio file) known as a cover-file, message and password (stego- key) as shown in Figure 1. The cover file conceals the secret information (data). Message is the embedded information that sender wants to be confidential. This message can be represented as an image, audio, plain text or any other file’s type [2] [3] . A stego-key is a private key which is used to embed the message in the cover audio file and hence the stego-file is created once the message hidden successfully in the cover audio file [3] . The most popular file formats for sounds which have been used are the Windows Audio Visual (WAV) and the Audio Interchange File Format (AIFF) [4] .
Embedding techniques are chosen according to requirement. Some of these are LSB coding, parity coding, spread spectrum phase coding and echo hiding [5] .
![]()
Figure 1. Basic audio steganographic model [2] .
Because of its highest capacity for data and the easiest way to implement in comparing with the other techniques, Least Significant Bit (LSB) method has been adopted in this research.
2. Least Significant Bit
Least Significant Bit (LSB) technique is one of the simplest approach for secure data transfer. In this technique, LSB of binary sequences of each sample of digitized audio file is replaced with the binary equivalent of the secret message [4] .
To hide the letter “D” as an example which has the ASCII code equal to 68 that is 01000100 inside eight bytes of a cover, the process of LSB can be shown as follow [6] .

3. Proposed Work
Among different approaches to hide a secret message inside an audio file, LSB coding method is proposed. This can be achieved by replacing the first, second, third and fourth bit of the audio file (.WAV format) respectively with its equivalent bit in the binary message. This process begins from the starting hiding position which is only known by the encrypted and recipient persons. Hiding results have been examined through some statistical estimators [7] - [11] .
I. Signal-to-Noise Ratio (SNR)
It is used as a measure of quality reconstruction of the audio file, given by
 (1)
(1)
where r(i), t(i) are the values of the ith samples in the original and stego audio file, respectively, n is the audio file’s length.
II. Peak Signal-to-Noise Ratio (PSNR)
The PSNR is the ratio between maximum possible power and corrupting noise that affect the representation of the audio file. In this case, the signal is the original audio file and the noise is the produced error for the embedding process. The PSNR is given by;
 (2)
(2)
The high values of SNR and PSNR indicates the high security, because they indicate the minimum difference between the original and the stego values.
III. Root Mean Square Error (RMSE)
It is used to quantify the difference between values implied by the original and the stego files. The RMSE is defined as;
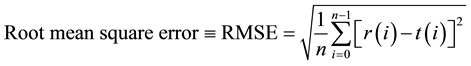 (3)
(3)
IV. Mean Absolute Error (MAE)
It is the difference between the original and stego values. So, no one can suspect the presence of any hidden information. The MAE is given by;
 (4)
(4)
The low values of RMSE and MAE indicate the high security, because they include the minimum difference between the original and new audio files.
4. Results and Discussions
The algorithm for LSB has been successfully tested through embedding a message into multiple wave audio files of various sizes which can be summarized in Table 1. According to HAS, no one can distinguishes the present of any difference between the cover (original) and the stego file.
Histograms for the audio wave file before and after coding are shown in Figure 2(a) and Figure 2(b), Figure 2(d) and Figure 2(e) while the difference between them is represented in Figure 2(c) and Figure 2(f) for the case of 1st & 4th bits respectively.
The symmetric with periodic behaviors for the difference between the two histograms can be seen clearly for the case of using 1st bit, while it isn’t the case for 4th bit in LSB. Figure 3 illustrates the variation of the adopted statistical estimators with LSB bit’s position. As expected and according to Figure 3 and Figure 4, the use of 1st bit in LSB technique is better than other used bits. Regardless to which bit is used, embedding a secret message inside the largest file’s size which have been examined here is better than with smallest one. This can be distinguished clearly through Figure 4.
For the first audio file, the process of hiding a secret message inside different positions of the audio wave file has been executed. Results show that starting hiding position doesn’t affect upon the variation of the statistical estimators regardless to which bit is used. This can be seen clearly from Figure 5.
In all figures, a similar behavior with equally spaced curves can be seen obviously for all SNR and PSNR variations. On the other hand, an increasing gap has been noticed between MAE and RMSE variation curves. In addition to the previous notice and according to its lowest value, MAE seems to be the best statistical estimator in testing hiding process.
![]()
Table 1. Information of the adopted audio files.
![]()
Figure 2. Results for LSB technique. (a), (b), (c) for the case of 1bit; (d), (e), (f) for the case of 4 bit.
![]()
Figure 3. Variation of statistical estimators with LSB bit’s position.
![]()
Figure 4. Variation of statistical estimators with file’s size. (a), (b) for 1bit; (c), (d) for 4 bit.
![]()
Figure 5. Variation of statistical estimators with starting hiding position.
5. Conclusion
Without any fear of eavesdropper, a new-audio file having a message hidden into it can be sent successfully by using different ways of LSB technique (i.e. 1st, 2nd, 3rd & 4th bit respectively). Regardless to which bit is used, starting hiding position doesn’t affect upon the statistical estimators in their variation. Results show that MAE can be used as a best estimator in testing hiding process. After all one can ensure that 1st bit in LSB technique is better than other used bits in hiding process.