1. Introduction
Quantum cryptography [1] [2] is a field which has matured since the first protocol, BB84, given by Bennett and Brassard in 1984 [3] [4] . The idea is to generate a secret key between two remote parties, traditionally called Alice and Bob using a quantum channel. The secret key may then be used in sending encrypted messages through the so-called Vernam Cipher [5] or one-time pad. Vernam cipher has been proved to be very secure under the condition that one shared key is to be used only once.
In principle, BB84 is proved to be one hundred percent secure [6] . However, when implemented in real life with non-ideal sources and detectors, several attacks have been successfully demonstrated against commercial QKD systems [7] -[12] .
In the traditional BB84 scheme, Alice sends a stream of single qubits to Bob which eventually leads to the generation of a secure key. Here we propose a new QKD scheme in which Alice sends a stream pairs of qubits to Bob. We will show that this scheme introduces an additional feature over the standard BB84 protocols, which should make it more difficult to break. It should be mentioned that QKD protocols using qubit pairs have also been proposed earlier [13] .
2. Quantum Key Distribution: BB84
To set the ball rolling, we describe the BB84 QKD protocol [3] [4] .
• Alice sends single qubits to Bob randomly in one of the following states:  and
and , where
, where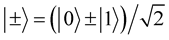 .
.
• Bob measures the incoming qubit’s state by randomly choosing a measurement of either the x-component of the qubit or the z-component, with equal probability. Let us say,  are eigenstates of the z-component of the qubit, and
are eigenstates of the z-component of the qubit, and 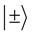 are the eigenstates of the x-component.
are the eigenstates of the x-component.
• Bob publicly tells Alice which bases he used for each qubit he received (but, of course not the result of his measurement).
• Alice publicly tells Bob which basis she sent each qubit in.
• Alice and Bob keep only the data from those measurements for which their bases are the same, discarding all the rest.
• This data is interpreted as a binary sequence according to the coding scheme ,
,  ,
,  ,
, .
.
• Alice announces the results of a small subset of her measurements. Bob checks if he has identical results. Any discrepancy here indicates a possible eavesdropping attempt.
• If there is no discrepancy, the rest of the binary sequence is treated as the new key, and is identical for both Alice and Bob.
3. New QKD with Qubit Pairs
In our new scheme, Alice sends pairs of qubits to Bob, randomly chosen to be in one of the following states,
 (1)
(1)
where . For Alice, the key bits associated with each state she sends are as follows:
. For Alice, the key bits associated with each state she sends are as follows:
 (2)
(2)
In addition, she calls the first two states as z-basis, and the other two as x-basis.
Bob uses one qubit for his secure key and one for the auxiliary key. For generating the secure key, he randomly measures the x-component or the z-component of the qubit. For the auxiliary key he measures only the x-component. For his secure key measurement results, he uses the following convention for key bit values:
 ,
,  ,
,  ,
, . For his auxiliary key measurement results, he uses the following convention for key bit values:
. For his auxiliary key measurement results, he uses the following convention for key bit values: ,
, 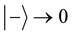 , if he measured x-component for the secure key;
, if he measured x-component for the secure key; ,
,  , if he measured z-component for the secure key.
, if he measured z-component for the secure key.
Alice and Bob announce their bases for secure key publicly, and discard those qubits for which their bases do not match. Various measurement results for rest of the cases where the bases agree, will be correlated in the following fashion. If Alice sends z-basis, the secure key bits of Alice and Bob will be identical. If Alice sends x-basis, the secure key bits of Alice and Bob will be identical if the auxiliary key bit is 0; the secure key bits of Alice and Bob will be different if the auxiliary key bit is 1.

Table 1. Result of a typical sequence of 15 qubits sent by Alice to Bob, where the measurement basis of Alice and Bob matches. When the auxiliary key is added to Bob’s secure key, it matches with Alice’s key.
Thus, for a sequence of qubit pairs sent, Alice and Bob’s secure key bits will be identical if the corresponding auxiliary bit is 0. Alice and Bob’s secure key bits will not match for cases where the auxiliary bit is 1. So, Bob just needs to add his final auxiliary key to his secure key bit by bit, modulo 2. This way, his auxiliary bit 1 added to his non-matching secure key bit will make it identical to Alice’s bit. The result of a typical sequence of qubit pairs is shown in Table1
4. Discussion
An eavesdropper trying to figure out the shared key in between, will have his task made difficult in more ways than it is in BB84. For correctly figuring out the auxiliary key, the eavesdropper has to know which of the two qubits was used for the auxiliary key for each and every pair, an impossible task. If we assume that the eavesdropper is able to correctly guess which of the two qubits is used for the auxiliary key, he can simply make an x-basis measurement on those qubits, and generate the correct auxiliary key without Bob’s knowledge. However, even in this near impossible circumstance, the rest of the communication still remains as the standard BB84.
However, there is subtlety involved here. If the eavesdropper attacks pairs of qubits, then she gains more information attacking this protocol than BB84, because the second qubit adds a certain amount of redundancy. In order to deal with such an attack, we introduce an additional step in the protocol. Alice generates pairs of entangled particles, but before sending them to Bob, she rearranges the order of particles in one of the channels using a predecided ordering-key shared with Bob. Now when she send out pairs of particles, the two particles in a pair are not in general correlated, but one particle of a pair is correlated with the second particle of another pair. Eve cannot know which pairs are correlated. After Bob receives all the pairs, he reorders particles in the relevant channel according the ordering-key. He then proceeds with the rest of the protocol as before. This reordering scheme is in the spirit of similar schemes proposed earlier [14] . With the reordering in place, the security of this protocol should be at least equal to that of BB84, but of course at the cost of additional resources.
5. Conclusion
In conclusion, we have introduced a new QKD scheme in which Alice sends pairs of qubits to Bob in four possible states. Bob randomly chooses one of the pairs for his secure key and one for the auxiliary key. The auxiliary key has to be added to Bob’s secure key in order to get the correct shared key. An eavesdropper’s job is made more difficult as he has to correctly predict which particle Bob is going to use for secure key and which one for auxiliary key, for every pair used in the communication. Even if the eavesdropper manages to achieve this near impossible feat, he is still left with the job of cracking the BB84 security. In addition, the scheme is modified using a reordering of particles to deal with two qubit attacks. We believe that this scheme should be implementable in practice.
Acknowledgements
Asad Siddiqui thanks the University Grants Commission for financial support. The authors thank an anonymous referee for suggesting improvements to the protocol.