Nodewise Decay in Two-Way Flow Nash Network: A Study of Network Congestion ()
1. Introduction
This paper presents a model of network formation game that is built upon the two-way flow model with imperfect information transmission of (Bala & Goyal, 2000a) , It envisages a situation in which information decays due to the agents’ imperfect ability to communicate as opposed to the imperfect connection/link, which is an assumption in most of the existing literature. It thus assumes that information decays as it traverses through each agent, hence the term nodewise decay. Moreover, aiming to shed light on the realism that agent’s effort to communicate tends to be limited, it assumes that nodewise decay level is strictly concave in the amount of agent’s links. Each agent thus knows that whenever he establishes a link with another agent both of them transmit information less efficiently, causing a decline in the value of information that flows through them. This paper aims to understand how this assumption may affect link-formation decision of agents and hence the shape of equilibrium networks. To this end, it identifies the shapes of equilibrium networks and analyzes why they differ from those of other models in the literature. Finally, the paper discusses how the results of the analyses may explain some features of real-world networks.
We argue that this paper’s assumption is worth studying. Consider a firm in which employees’ task is to communicate with each other. In this network, there may be a center-like agent whose role is to collect and distribute information of other agents. Such an agent is important because the degree to which the information is lost depends on his ability to communicate. This is likely to decline as there are more contacts between him and other agents. This fact has two consequences. First, each agent has to take into account that contacting the center damages the information flow. Second, the value of information that he receives in turn may not worth the efforts to contact. Consequently, he may avoid contacting the center by contacting another agent or choosing to be completely disconnected. The fact that the center finds more difficulties in transmitting information as he has more links may be considered as a form of network congestion, and the fact that other agents may avoid contacting the center may be considered as a form of congestion avoidance. However, how this realism affects agents’ linking decision has not been investigated in the literature of game-theoretic network formation to our knowledge. This paper’s attempt to address this issue is therefore the central contribution to the literature.
With this situation in mind, this paper modifies the two-way flow model of BG as follows. In a network g we let the decay factor be nodewise: as information is transmitted through agent i, a fraction of information equal to 1 − σ (i; g) is lost. Moreover, σ (i; g) is decreasing and strictly concave on the amount of i’s links. The strict concavity is assumed for two reasons. First, it reduces mathematical difficulties. The strict concavity assumption implies that information decays completely if an agent possesses a sufficiently large number of links. Second, nodewise decay can be considered as a productivity of an agent in transmitting information. While there is no theoretical support, the following examples show that the difficulties that an agent face in transmitting information tend to increase at an increasing rate. Suppose that an agent stores all pieces of information in one place, then due to the limitedness of space, the chance that multiple pieces of information get mixed up, and hence cause more difficulties in communicating accurately, is arguably likely to increase at an increasing rate. Another example is when the pieces of information are very similar to one another. Then, the chance that an agent does not know which is which, as he has more pieces of information to transmit, is also arguably likely to increase at an increasing rate.
Besides these two assumptions, this paper retains all assumptions of two-way flow of BG, which are briefly described here for unfamiliar readers. Each agent possesses a piece of information that is nonrival. He can choose to sponsor costly links to any agents without their agreements. All links together form the network. If there is a link or a series of links between two agents, they are obliged to share their private information. Thus, the decision of agent to form a link represents his decision to make his private information available to other agents in exchange for receiving their information, and concurrently his willingness to be an information transmitting device. In BG, the decay factor is assumed to be geometric and linkwise: each link causes a fraction of information loss equal to 1 − σ, where σ is constant.
Since this paper models network congestion in a stylized way, we provide two justifications. First, this model makes observing the effects of congestion avoidance easier. The original model of BG and this model permit each agent to access others without their agreements. This implies that each agent decides on his own as to how to avoid the congestion he finds in the network, hence easing the observation. This advantage is also facilitated by the assumption that agents’ information is nonrival. If it is assumed otherwise, it may be difficult to distinguish whether an agent decides not to access another as a result of the congestion or the rival nature of information. Second, because links are formed in a noncooperative way, Nash equilibrium in pure strategies can be applied as the solution concept. This eases the analysis.
Admittedly, the assumption of unilateral link formation has a disadvantage. It entails that agent cannot defend against an access by another agent, even when the access lowers his payoffs. This implication is not realistic in many cases. For example, in a file sharing network, one agent may decline an access by another agent if the access lowers his internet speed. Hence, our model does not provide an insight to this side of reality. We believe, however, that there are some situations in which this model can be applied. These are such as workplace environment in which agent is obliged to disseminate all information he receives even when his productivity is declining, or friendship and kindred networks in which agents voluntarily feel obliged to welcome link formation due to psychological and peer pressure.
Based on the observation from the main results, two insights on the structure of real-world networks can be learned. First, through nodewise decay assumption equilibrium network tends to be fragmented, consisting of disconnected components. The intuition is that agent in one component may avoid entering another in order to avoid the network congestion. This may explain why empirical literature finds that disconnected networks are common in the real world. Second, moving from a smaller network to a larger one (a network with more agents) does not imply that the moving agent will improve his payoffs. The intuition is that agents in a larger network may be more congested (having more links), causing information to flow better in a smaller network. This may explain why real-world networks often consist of fragmented communities of notably different sizes. For example, in a friendship network, some students may prefer to keep their friendship within a small group rather than joining the crowd because they enjoy a stronger friendship that provides a better flow of benefits. These insights can be observed in our first proposition, which finds that no Nash network is connected if information decays at least by half whenever it is transmitted through an agent that has two links. This disconnectedness stands in contrast to the result in the original model of BG that all nonempty Nash networks are connected.
Beside the above disconnectedness, two results are also different from BG’s. First, Nash Network (in pure strategy) does not always exist. This result is shown by an example. Second, no stars are Nash except a centersponsored star if the network has more than three agents1.
This paper contributes to the literature in game-theoretic network formation, which is pioneered by the work of Jackson & Wolinsky (1996) 2. Their model assumes that two agents must share a mutual consent in order that a link is established. A seminal work that contrasts to this model is that of BG in which one-sided link formation is assumed. Since it assumes several simple assumptions such as agent homogeneity and linkwise decay, it has spawned a vast literature that questions how certain realisms, when incorporated as assumptions, influence the shape of equilibrium networks.
A strand of this literature which this paper belongs studies various forms of inefficiency in information flow. Interestingly, most models in this literature focus on link, which is a connection between agents, as a source of inefficiency in information flow rather than agents themselves. For example, Bala & Goyal (2000b) , Haller & Sarangi (2005) and Billand et al. (2011) extend the two-way flow model of BG by assuming that link formation may fail with a positive probability. Also, Billand et al. (2010) studies the insider-outsider model of Galeotti et al. (2006) , which is an extension of BG, by varying the level of linkwise decay. Among this group of literature, noteworthy is that of Bloch & Dutta (2009) and Deroian (2009) , which assume that the decay level of each link varies based upon the extent to which the agents are willing to spend their limited resources. These models share a similarity to the model of this paper in the sense that in this paper each agent is also assumed to have limited ability to communicate. However, a major difference does exist. Unlike the model of Bloch & Dutta (2009) and Deroian (2009) , this model assumes that the decay is nodewise in the sense that the decay occurs each time information traverses through an agent. Thus, it perceives agent, rather than link, as a direct and primary cause of inefficiency in information flow. This difference entails a major interpretation of realism. If the decay is assumed to be linkwise, as most papers do, then the major cause of the decay is the connection or the relationship between agents. On the other hand, if the decay is nodewise, then what causes the decay is the inability of agent to communicate perfectly.
Another paper that shares a certain extent of similarity to this paper is Feri (2011) , which also assumes that the decay is nodewise. Indeed, to our knowledge, apart from this paper Feri (2011) is the only paper that assumes nodewise decay. However, a major difference exists in terms of how the nodewise decay is modeled. In Feri (2011) , the decay level is an outcome of the coordination game played between two agents who share the same link. Thus, it can be interpreted that the decay depends on the compatibility of technology adopted by the two agents. On the other hand, this paper assumes that the decay level depends on the quantity of links that each agent possesses. Thus, our concern is on the limitedness of the efforts of agent to communicate, rather than the technology that he adopts.
The paper proceeds as follows. In Section 2, the model and all assumptions are introduced. Subsequently Section 3 introduces the main results. It consists of two propositions. The first proposition fully characterizes Nash networks under the restriction that information decays at least by half if it traverses through an agent that has more than two links. Admittedly, due to the mathematical difficulties full characterization of Nash network is not achieved when this restriction is removed. The second proposition, instead, discusses certain properties of Nash networks given the removal of this restriction. We also provide some examples of Nash network and their supporting parameters. Subsequently Section 4 uses the analysis from these results to provide some insights to certain features of real-world networks. Finally, Section 5 concludes.
2. The Model
is a set of agents. i and j are typical members of this set. Each agent possesses a nonrival piece of information that is valuable both to himself and any other agent who has an entry to it. Information flow in this model is two-way in the following sense. If i has an entry to j information, then j also has an entry to i’s information. An entry to information is made possible through the existence of a link or a path, a series of multiple links, between two agents.
Link establishment is costly and one-sided. i can choose to form a link with any other agent without his consent so long as he bears the link formation cost c. A strategy of i is a set
where
and
if and only if i forms a link with j. In this case, it is said that i accesses j. Throughout the entire paper the our analysis is restricted to pure strategies. Let
be a strategy profile. The strategy space of i is
and the set of all pure strategy profiles is
.
To visualize how information flows among agents, a strategy profile g can be represented by a network. Pictorially, a network consists of a set of nodes, each represents an agent, and a set of arrows pointing from one node to another. There exists an arrow from node i to node j if and only if i accesses j in a strategy profile g. As a consequence of this symbolization the term network g and strategy profile g are used interchangeably onwards. Figure 1 depicts an example of a network.
Because a link between i and j can be sponsored by either i or j, to distinguish
![]()
Figure 1. A network with five agents.
,
,
,
,
,
.
the link sponsorship let
be the set of all agents whom i accesses and
be the number of links that i establishes. To indicate whether there is a link between i and j, let
so that
if and only if there is a link between i and j. Similarly, let
and
so that
represents the number of I’s links.
Based upon these notations, information flow is formalized as follows. i’s information flows to j if there exists an ij-path. Formally, an ij-path,
, is a sequence
whose each element is 1. If
exists, it is said that i observes j. The set of all agents observed by i is
. Note that if i observes j then j also observes i.
To maintain a comparison with the original two-way flow model with linear payoff in BG, the value of each piece of information that is perfectly transmitted and received is 1. However, in the process of transmitting and receiving this value may decay. In this paper, the decay is incurred nodewise. That is, for each agent k a decay factor
is assigned. As information traverses through k, a fraction of information equal to
is lost. That is,
, is the percentage rate at which the value of information is preserved. Therefore, if the information of j is transmitted to i through a path
, the value of j’s information
that i receives is
, where
is the set
of all agents in
. Figure 2 illustrates how the values of information of other agents flow to agent 1 in a network.
Naturally, if multiple ij-paths exist the value of j’s information received by i is given by the optimal path(s). Formally, let
be the set of all paths, each enumerated by the superscript, through which i observes j in a network g. The value of the information of j that i obtains in this network is
. An optimal ij-path,
, is thus a path that solves
. The set of all optimal paths is
. Similarly, the value of i’s own information is
if i has a link and
if i has no link. This assumption is justified as follows. As the amount of i’s links increases, so is the amount of information that arrives to him. This decreases his ability to correctly process each piece information before he transmits it to other agents. This in turn affects his ability to process his own information. Alternatively, if he has no link, then he can consume his own information with no decay. That is,
if i has no link.
Having defined the value of information, we are now ready to define the payoff of player i from the strategy profile g in a game with n players. It is:
![]()
Figure 2. In the above network,
,
,
,
.
To adjourn this section a major difference between our model and BG’s is pointed out. This difference is in how information decays. In BG, the decay is assumed to be linkwise and geometric. For example, let λ be this decay. If an ij-path consists of m links, then the information of j decays to
when it arrives to i. Hence, the aggregated decay of a path depends solely on its length. In contrast, the decay in our model is defined nodewise, σ(), which depends on the amount of links of each agent who lies on the path. Consequently, two ij-paths with the same length may not provide the same value of information to i. We remark that this is a major cause of mathematical difficulties in the analysis of equilibrium characterization.
2.1. Nash Networks and Strict Nash Networks
In a network, a point of view of an agent i can be considered as the set of all links formed by all agents in the network except himself. Let this set be
. That is, an agent i takes a look at this set and then decides with whom he wishes to form links for the best of his interest. This is his strategy
. A set that is a union of
and
of course form the network g. We denote this set by
and use these notations to define the term Nash network and Strict Nash network below.
Definition 1 (Best response). A strategy
is a best response of i to
if
Definition 2 (Nash network). A network g is a Nash network if
is a best response to
for every agent
.
Moreover, if the inequality is strict for all
, Nash network is a Strict Nash Network. We abbreviate the term Strict Nash Network by SNN.
2.2. Assumptions on Decay
Our key assumption is that the decay factor
depends solely on the number of i’s links. This is formalized as follows.
Assumption 1 (Concave Decreasing Nodewise Decay). Let
be a function such that:
1)
be the value at x.
2)
.
3) there exists
such that
for all
. Moreover, for
,
is decreasing and strictly concave.
Throughout this paper we assume that
for all
.
Certain remarks on these assumptions are worth elaborating. First,
implies that an agent’s decay factor depends solely on the number of links. Moreover, two agents have the same decay factor if they have the same amount of links. That is, agent homogeneity is assumed. Second,
entails that perfect information transmission occurs if an agent has exactly one link. Finally, the existence of K in the last part warrants that the nodewise decay factor becomes zero, rather than being negative, once the amount of agent’s link reaches a certain extent.
2.3. Network-Related Definitions
This subsection introduces some properties of networks and definitions of some particular patterns of network that are used in the analysis. A network is minimal if every ij-path is unique. If an ij-path exists for any
, a network is said to be connected. Let
and
be networks and
and
be their set of agents,
is a subnetwork of
if
and
.
is said to be a component of
if
is a maximally connected subgraph of
.
The particular patterns of network that are used in the equilibrium analysis are introduced as follows. A network is a line if there are exactly two agents that have one link and every other agent has two links. A network is a wheel if every agent has exactly two links. Note that if a link is removed from a wheel the resulted network is a line. A network is empty if every agent has no link. In such a network, each agent is said to be a singleton. A network is a star if it is a minimally connected network such that there is a unique agent
that has exactly one link with every other agent. A star is a center-sponsored star if
sponsors all links. A star is a periphery-sponsored star if
sponsors no links.
3. Main Results
The goal of this section is to identify Nash networks and their properties. I
summarize main results as follows. For
, Proposition 1 guarantees the
existence of Nash network regardless of the values of ς2 and c. It also provides an expansive equilibrium characterization.
Proposition 1. 1) If
, Nash network exists for any cost c and number
of players n. Moreover, each component of a Nash network is one of the following three types.
a) A three-agent periphery-sponsored star, ie., network (a) in Figure 3.
b) A pair, i.e., network (b) in Figure 3.
c) A singleton, i.e., network (c) in Figure 3.
![]()
Figure 3. Three types of components in a Nash network, given that
.
2) Using the network (a), (b) and (c) in Figure 3, the set of Nash networks for each set of parameters c and
is given below.
a) If
and
, then the empty network is a unique Nash network.
b) If
and
, then Nash network is either the empty network or
the network that contains at most one component that is a singleton, and every other component is either a three-agent peripherysponsored star or a pair.
c) If
and
, then the set of Nash networks consists of all networks
that have the following architectures:
· the empty network.
· the network that has at most one component that is a singleton, and every other component is a pair.
d) If
and
, then Nash network has at most one component that is a singleton, and every other component is a pair.
e) If
and
, then Nash network is.
· the network that has at most one component that is a singleton, and every other component is a pair.
· the network such that each component is either a three-agent periphery-sponsored star or a pair.
A particular feature of Nash networks in Proposition 1 is that none of them are connected, given that
. This is a contrast to Proposition 5.3 in BG which shows that every non-empty Nash Network is connected. What drives this contrast? In BG, if i finds that the component that he accesses provides more benefits than the component that j accesses, then j always finds likewise. Since BG assumes that link formation cost is homogeneous, it follows that j has a positive deviation by removing his link with his component and access i’s component instead. However, under the concave decreasing nodewise decay assumption this reasoning is not valid. Whenever j enters the component of i, he reduces the decay factor at the agent with whom the link is formed. This entails that the value of information that j receive may be sufficiently low that it does not cover his link formation cost. Consequently there is no guarantee that his payoff will improve. The following example clarifies this intuition by showing what happens when the linkwise decay assumption in BG is replaced by our nodewise decay assumption.
Example 1. Consider the Nash network for
and
in Figure 4. It is easy to check that i’s payoff does not improve if he removes his link with j
![]()
Figure 4. A Nash network with five agents for
and
.
and imitate the strategy of k by forming the link with l. Indeed, his benefit from accessing l is 0 since
.
On the other hand, suppose it is assume that the decay is geometric, linkwise, and the decay factor is
as in BG, then k’s benefit from accessing l is
and i’s benefit from accessing j is merely
. As a result, i has a positive deviation by removing his link with j and accessing l instead.
Contrary to Proposition 1, for
Nash network does not exist for some
parameters c and n. An example is given below.
Example 2. Let
, and
, no network with 5 agents
is Nash3.
Contrary to Proposition 1, for
Nash network does not exist for some
parameters c and n. An example is given below.
Example 3. Let
, and
, no network with 5 agents
is Nash4.
A remark is that the nonexistence of equilibrium originates stems from the fact that nodewise decay assumption causes agents’s payoffs to change discretely. Indeed, due to this complication the provision of full equilibrium characterization
for
is not attained. Instead, Proposition 2 below describes some properties of Nash network for
. It states that no two agents who have exactly
one link want to access the same agent in Nash network. The intuition, which is a result of congestion avoidance, is straightforward. Let i and j have exactly one link with k, and i accesses k. Then i is better off avoiding the link formation with k and accessing j instead. Such avoidance is profitable because initially j has only one link. The link addition by i thus increases the amount of j’s links from one to
two. This fact and the fact that
guarantee that information loss that is
incurred by j is sufficiently low. Formally, let an agent who has exactly one link be called end node and the agent who is his neighbor parent.
Proposition 2. Given that
and
5. In a minimal Nash network
g, let j be an end node and i be his parent,
1) if j accesses i, j is the only end node of i;
2) if i accesses j, i accesses all his end nodes.
A corollary of Proposition 2 which is establish below is straightforward: no star is a candidate for Nash network, except center-sponsored star. A notable remark is that this result differs from Proposition 5.3 in BG which shows that all kinds of stars are Nash if decay falls within a certain range.
Corollary 1. Given that
and
, no star is a candidate for Nash
network, except center-sponsored star.
Beside center-sponsored star, line is also a candidate for Nash network. Figure 5 shows some Nash networks and their supporting parameters.
4. Discussions
This section points out two particular features of equilibrium networks in this model. It questions why they arise and provide intuitions as to what causes agents to make such link formation decision. Finally it discusses how these intuitions may explain some features of real-world networks.
4.1. Network Congestion May Lead Equilibrium Networks to Be Disconnected
The first observation comes from the fact that all Nash networks for
are
disconnected, as in Proposition 1. The intuition, which is made clear by Example 1, can be summarized as follows. While establishing a link to an agent is a way to reach a component, it also increases the congestion at the agent who receives the link. This congestion may cause much loss in the information transmitted via the agent. When such congestion, or inefficiency in information transmission, is sufficiently high, an agent may be better off avoiding the congestion altogether and staying disconnected from the component.
![]()
Figure 5. Two lines and a star that are Nash.
How does this observation help us understand real-world phenomena? This observation may serve as a hypothesis that explains why empirical evidence finds that real-world networks are often disconnected. If a community is considered as a network in which information is exchanged among agents, it is likely that it is fragmented into sub-communities if agents find that avoiding connection between each sub-community is a way to reduce inefficiency in information flow. For instance, sociologists have long observe that a common feature of friendship networks is that there are agents who are social isolates, disconnecting themselves from the principal component (Ennett & Bauman, 2009) . Also Kumar et al. (2010) give a surprising remark that several online social networks contain isolated communities and singletons.
4.2. Connecting to a Larger Component Does Not Imply Larger Benefits
Our second observation is that a smaller component may provide higher benefits to their members than a larger one. The is evident through the fact that many Nash networks in Proposition 1 consist of components whose sizes, or the numbers of agents, are not equal. Consider, for example, the equilibrium network in Example 1. Observe that i chooses to access an isolated agent j rather than an agent in the larger component. If i accesses j, j’s productivity is
. If i accesses someone in the larger component, the productivity of the accessed agent is at most
. Hence, if
is sufficiently lower than
, then his strategy to abandon the smaller component that contains j and enter a larger one gives i relatively lower benefits compared to his strategy to maintain the link with j.
This observation may explain why there are agents who prefer to reside in a relatively smaller component rather than a relatively larger one that contains most of agents. Consider the following hypothesis. While a larger component contains more agents, and hence more information, each agent may possess relatively more connections than his counterpart in a smaller component. If the increase in connections is further assumed to increase inefficiency in information flow, then an agent may prefer to stay in a smaller component rather than joining a larger one. Put differently, when choosing between joining a smaller component or a larger component, an agent faces a tradeoff between the quantity of information and quality of information that he receives. If the quality of information prevails, then he is better off being in a smaller component. A friendship network among adolescent students may serve as an example of this hypothesis. Some students may choose to be “social isolates,” defined as students who are alone or those who maintain their friendships within a smaller group and avoid contacting the major group (Ennett & Bauman, 2009) . This model thus hypothesizes that such behavior arises because by avoiding the crowd the social isolates enjoy higher benefits shared among one another.
Noteworthy is how the above insight relates to literature in Sociology. This model proposes that the existence of social isolates may be explained by a reason that is not agent heterogeneity, which appears to be the most natural reason. The insight from this model, therefore, stands in contrast with a vast literature in Sociology that places agent heterogeneity in terms of ethnics, attitude or physical appearance as a primary cause of social isolates. For example, Haas et al. (2010) assume that poor health in adolescent such as substantial physical handicap may be a cause of social isolation, and Kennedy & Kennedy (2004) suggest that individuals with anxious resistance have a higher risk of becoming social isolates. In addition, a recent work in game-theoretic network formation by Fershtman & Persitz (2021) also illustrates a similar tradeoff in the context of social clubs. In this paper, players face tradeoffs between “high quality links through a series of small clubs and…low quality links produced in large clubs”. Finally, I remark this insight and the aforementioned insight in Section 4.1 are closely related. Indeed, if agents find that joining a larger network does not lead to higher benefits as mentioned in this section, then a better alternative for them is to form another component that is disconnected from the main component, which is what is discussed in Section 4.1.
5. Conclusion
This paper provides a stylized model of network formation with two key assumptions. First, link can be formed without a mutual consent between agents. Second, link addition increases the congestion, or more information loss, at the agent who receives the link and the agent who forms the link. The model allows an ease of observation on how an agent may avoid forming links with other agents due to increasing congestion. As shown in Proposition 1, under a large set of parameters the two key assumptions lead to equilibrium networks that consist of disconnected components. In some cases, these components also have different sizes.
While it is difficult to make generalization from this simplified model, the link-formation behavior of agents in equilibrium networks may provide some insights to two common features of real-world networks. First, the fact that real world networks are often disconnected may be explained by the fact that agents choose to avoid forming a link that bridges two components since the link addition increases congestion, and hence increasing inefficiency in information flow. Second, an agent may prefer maintaining a link with an agent in a smaller component rather than with an agent in a larger component. This is because he takes into account the tradeoff between receiving less quantity of information with higher quality of transmission in a smaller component and more quantity of information with lower quality of information in a larger component and finds that the former prevails.
This model can be extended in several ways. First, to move closer to reality an extension may assume that an agent can choose to vary his nodewise decay for each link that he possesses. Second, since in this model agent homogeneity is assumed, an extension may be to assume a certain form of agent heterogeneity. For example, some agents may have nodewise decay that incurs less information loss than that of other agents. Third, it may be interesting to apply an equilibrium prediction criterion that assumes that link is formed under mutual consent (eg., pairwise stability of (Jackson & Wolinsky, 1996) ).
Appendix
1.1. The Concepts of Marginal Cost and Marginal Potential Benefit and a Useful Lemma
In this subsection, two useful definitions and a lemma for the proofs of Proposition 1 and 2 are introduced. The first two definitions, Marginal Potential Benefit and Marginal Cost, concern the (potential) gain and loss to an agent whenever he adds or removes exactly one link. Subsequently we introduce a lemma that states that an agent has an increasing (decreasing) payoff if the Marginal Potential Benefits are higher (lower) than the marginal cost. Naturally, in Propositions 1 and 2, this lemma is used to show whether a deviation of an agent by adding/removing a link is positive.
Consider an agent i in network g. Let
be the network that results from the addition (elimination) of the link
by i. In
, the set of all agents that i observes can be partitioned into three sets. The first set contains all agents that i observes in g, and the addition of
does not generate a new optimal path. On the other hand, the second set contains all agents that i observes in g, the addition of
generates a new optimal path to these agents. The third set contains all agents that i observes in
but not in g. These three sets are formalized as follows.
Consider all agents in
. Although i can use the same optimal paths to observe them, in
the value of information that he receives from these agents are lower than what he receives in g because
. This decline in i’s benefits, and the link formation cost c, are together called Marginal Cost of i for adding
to g.
Definition 3 (Marginal Cost). Let
be defined as above, the marginal cost of i for adding
to g is
The last inequality follows from the fact that the only difference between g and
is the addition of
. As a result,
,
and
for all
.
Consider all agents in
. Because i can observe in
but not in g, The value of information from these agents that i receives are considered as i’s benefit from the link
. Moreover, consider all agents in
. These are agents that i does observe in g. But by adding
he is able to find new optimal paths to reach them. Observe, however, that these new paths in
may yield benefits to i that are higher, lower, or equal to the optimal paths in g due to the concave decreasing nodewise decay. The gain from being able to observe
and the potential gain/loss from finding new paths to observe agents in
are together called Marginal Potential benefit of i for adding
to g.
Definition 4 (Marginal Potential benefit). the marginal potential benefit of i for adding
to g is
.
Having defined the marginal cost and marginal potential benefit, we are ready to introduce the following Lemma.
Lemma 3. Let
and
be defined as above. We have:
1)
2) (link addition proofness) If
, then g is not Nash
3) (link deletion proofness) If
, then g is not Nash
Proof. The first part is a direct consequence of how
and
are defined. The second part directly follows the first part, stating that has a positive deviation from his strategy in g by adding
if his marginal potential benefit for adding
is higher than the marginal cost. The third part is analogous to the second part, stating that i has a positive deviation from his strategy in g by eliminating
, if his marginal potential benefit for adding
to
is higher than the corresponding marginal cost. □
1.2. Proofs of the Propositions
Proof of Proposition 1. The proof consists of four steps. In the first three steps, we eliminate certain set of networks from being candidates for Nash networks. First, all networks that contains an agent that has more than two links are eliminated. This follows that a non-empty component of Nash network is either a wheel or a line. We subsequently eliminate the wheel in the second step. In the third step, all lines that contain an agent that receives one link and also establishes a link are eliminated. As a result of these three steps, a component in Nash network is a three-agent periphery sponsored star, a pair, or a singleton. Finally, in the fourth step we identify the exact combinations of these three types that are Nash for each pair of c and
. This is achieved through direct substitution.
Step 1: A network that contains an agent that has more than two links is
not Nash. Let this agent be i. Observe that
because
and
is strictly concave. Therefore,
. It follows that if i accesses an agent in this network, he is strictly better off removing the link to save the cost c. Conversely, if i is accessed by an agent j, for the same reason j is better off removing the link. Due to these deviations this network is not Nash.
Step 2: A network that contains a component that is a wheel is not Nash. Consider an agent i who establishes a link in a wheel. Without loss of generality enumerate the agents in
according to Figure A1. Let
. Observe that his direct neighbors are 2 and
. Observe further that if he removes the link
this wheel becomes a line. Denote this wheel and line by
and
respectively. In what follows it is shown that he is strictly better off removing the link
.
Consider an agent
. There are two 1k-paths through which 1 observes k. One contains
and the other one does not. Observe that the latter coexists with 1k-path in
but the former does not. Denote these two paths by
and
respectively. Observe further that:
·
and
· for
,
,
and,
· for
,
,
and,
As a result,
for
.
This in turn entails that in this wheel
is a unique optimal path for
. Based upon these observations, the marginal potential benefits and
marginal cost are expressed below:
![]()
![]()
Figure A1. A wheel with
agents, enumerated from left to right.
Because
, it holds true that
. Consequently, through Lemma
is not Nash.
Step 3: if a component of a network is a line that is neither a three-agent periphery-sponsored star nor a pair6, then this network is not Nash. The proof is by contradiction. Suppose that the component is neither a three-agent periphery-sponsored star nor a pair, so that the component has at least three agents. It is straightforward to check that in such a component there exists an agent who has two links such that one of the links is formed by himself. Let this agent be i and the link be
. In what follows it is shown that i is strictly better off deleting
.
First, observe that without
i is disconnected from the line that contains j.
thus consists of two components, one contains j and the other one contains i. Denote these two components by
and
respectively. Suppose that there are
agents in
, i’s marginal potential benefits for adding
to
are:
if
, and for
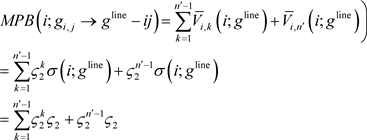
To compare the marginal potential benefits with the marginal cost, in what follows we identify a lower bound of
. Beside the cost c, i’s nodewise decay drops from
to
if he establishes
. Therefore, the lower bound
is
.
Because
and
. Therefore,
. Applying Lemma 3 to this inequality, it is concluded that i is strictly better off deleting
.
Step 4: Equilibrium Characterization for each pair of c and
. As a result of the three steps above, every Nash network is a combination of components that are a three-agent periphery sponsored star, a pair, or a singleton. Therefore, it is straightforward to identify which combination constitutes a Nash network. First, all deviations that arise from every combination are categorized. Each deviation is further coupled with the deviating agent’s payoff as a result of deviation and his payoff when he does not deviate. We then substitute the value of each pair of c and
to identify whether the deviation is positive. The combinations that have no positive deviations are concluded to be Nash networks accordingly.
To minimize the tedium, Step 4.1 and 4.2 below eliminate some types of deviations by pointing out that they are never positive.
Step 4.1: In a network where each component is a three-agent periphery-sponsored star, a pair, or a singleton, a deviation that causes the deviating agent to have more than one link is never a positive deviation. This result is a direct consequence of Step 2 and 3. Let i be an agent that does this deviation. This entails that i forms a link with an agent j. If j is in the same component as i, then this component becomes a wheel. However, in Step 2 it is shown that i’s payoff in a line is higher than his payoff in a wheel. Consequently this deviation does not make i better off.
Step 4.2: if c < 1, then a network that contains more than one singleton is not Nash. Let i and j be singletons. If i accesses j, his payoff is
. If i does not access j, he remains isolated and his payoff is 1. Therefore, if
i has a strictly positive deviation by accessing j.
Step 4.3: Equilibrium Characterization for each pair of c and
. Using Step 4.1 and 4.2, we classify all networks that remain candidates for Nash networks into seven classes as follows.
1) At least one A, at least one B, exactly one C
2) At least one A, at least one B, no C
3) At least one A, no B, exactly one C
4) No A, at least one B, exactly one C
5) All A
6) All B
7) All C (only for
)
Finally, identification of Nash network is achieved in the following manner. For each agent in each type of component, all deviations except those eliminated by Step 4.1 and 4.2 are listed and coupled with their deviationbased payoffs and no-deviation payoffs. Figures A2-A4 illustrate such. By substituting the value of c and
into the payoffs and subsequently comparing them, we reach the result of Proposition 1.
□
Proof of Proposition 2. In a minimal network g, let
be an agent that has a link with an end node. Let
be the end nodes that have a link with
. Suppose that
is accessed by
. We partition the set of all neighbors of
,
, into three subsets as follows: (i)
, (ii)
, and (iii)
and
. For each of these subsets, the value of information that
receives in g is identified. Subsequently, it is again identified under the assumption that
removes
and accesses
instead. We then compare the payoff of
in g with his payoff in
, where
is the network resulted from the removal of the link
and the addition of the link
(See Figure A5 for an illustrated example). Finally, it is shown that his payoff in
is higher than
![]()
Figure A2. Deviations by agents in a three-agent periphery-sponsored star.
![]()
Figure A3. Deviations by agents in a pair. Without loss of generality, it is supposed that deviations are caused by agent
. Notice that deviations from
are not listed as a result of Step 4.1.
![]()
Figure A4. Deviations by an agent that is a singleton. Without loss of generality, it is assumed that all deviations are from agent
.
![]()
Figure A5. The networks g and
in Proposition 2. Observe that in
accesses
instead of
, unlike in g. Observe that in g,
,
,
,
.
his payoff in g. This is the strategy of this proof.
To identify the value of information that
receives, the number of links that agents have in g and
are identified as follows: since the only difference between g and
is that in g
accesses
but in
accesses
, we have
,
but
, and
for
.
Using the above information,
’s payoff in g is:

Therefore,
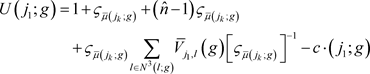 (1)
(1)
Next,
’s payoff in
is identified below. It makes use of the fact that information of
flows to
via
. Moreover, for any agent
and
, notice that l’s information flows to
,
and
in sequential order. As a result,
’s payoff in
is:
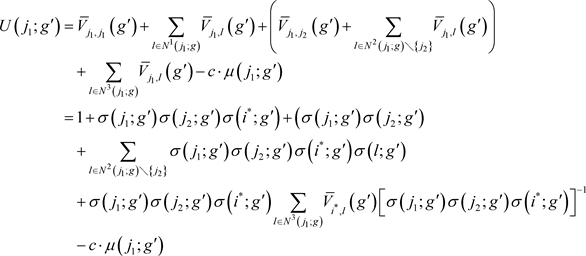
Therefore, applying the fact that
, and
but
, we have:
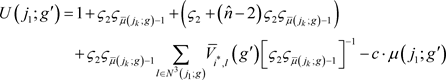 (2)
(2)
To be able to compare Equation (1) with (2), in what follows, it is shown that:
First, notice that
-path is unique for any
because g and
are minimal. This in turn necessitates that
has at most one link with an agent that is not an end node. Let this agent be k. Thus, for any
the sequence of agents in
and
are
and
respectively. Consequently,
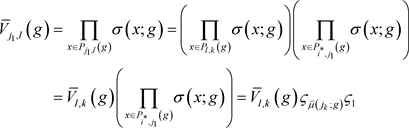 (3)
(3)
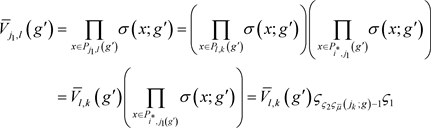 (4)
(4)
Since the only difference between g and
is the fact that
removes his link with
in g and accesses
instead in
, it holds true that
. Applying this fact to Equation (3) and (4) above, we have:
![]()
Finally, since σ() is strictly concave,
. This inequality, coupled with the Equation (3c) above, entail that
when Equation (1b) is compared with (2b). This completes the proof. □
NOTES
1A star is a network such that there is a unique center-like agent who connects to all other agents. But all other agents have no links with each other. A center-sponsored star is a star such that the center sponsors the link to every other agent.
2 Jackson (2007) and Jackson (2008) provides an overview of network formation literature and an overview of network studies in economics respectively.
3The proof tediously consists of proving that in each possible network there is at least one agent that finds a positive deviation. It is thus omitted.
4The proof tediously consists of proving that in each possible network there is at least one agent that finds a positive deviation. It is thus omitted.
5If n ≤ 3, this proposition does not apply. Every component of Nash network is either a line or empty. The proof is trivial and is omitted.
6Three-agent periphery-sponsored star and pair are lines