Secured Data Transmission Using Modified LEHS Algorithm in Wireless Sensor Network ()
Received 17 March 2016; accepted 30 May 2016; published 2 June 2016

1. Introduction
Recent advancement in computer industry, communication and technology leads to an information revolution for past two decades. In information revolution, securing the information is the major issue. Also it throws many unique challenges in transmitting the digital information, a digital data or a multimedia data, through an unsecured wireless network. Cryptology is the science used to secure the information. Cryptology is a Greek word compounded by “kryptos” means hidden and “logos” means word. The study of “cryptology” is called cryptography. The art of sending message secretly was in practice even before four thousand years as a safety measure in military and diplomatic communications.
In cryptography and network security by William stallings, encryption and decryption are the two terms used for secured communication. In encryption, the information which is to be transmitted safely (plaintext) is converted to cipher text using any algorithm or logic. In decryption, the received cipher text is decrypted using the same algorithm or logic used during the encryption to obtain the original information.
Nowadays, the computer ciphers substitute the mechanical cryptology techniques. Many ciphers are formulated with the help of substitution and transposition principles. All the ciphers depend on choosing a key either public or private. Three issues have to be addressed to propose a new cipher. The operations used to convert plaintext to cipher text and cipher text to plaintext are formed meticulously. Then the status of keys used for encryption and decryption as private or public and number of keys used in the process are arrived and the processing of the plaintext had to finalized.
All traditional cryptosystems developed before 1970s are symmetric key cryptosystems. Most of the contemporary cryptosystem are symmetric such as Advanced Encryption Standard [1] (AES), Data Encryption Standard [2] (DES), RC5 [3] , Hill Cipher [4] , and many more. Hill cipher is a classical symmetric block cipher utilized in different ways according to the applications and it is also possible to encrypt and validate the information at the same time. It can be intended to have high speed of ciphering and deciphering with high data throughput [5] . Also, Hill cipher has a weak security cryptosystem due to the linearity property and it is vulnerable to known-plaintext attack.
In Hill cipher alphabets, A to Z was masked with the values of 0 to 25 and ciphered using private key matrix. Hill cipher is capable of encrypting alphabets alone not the numerals and special characters. It is susceptible to “Known Plain text attack” as the key matrix is not permutated. To conquer this security flaw, many researchers proposed the unique modification. Ismail et al. [6] proposed a modified Hill cipher named HILLMRIV algorithm, a secret initial vector is used to obtain the unique key for enciphering. Rangel-Romero et al. [7] claimed that HILLMRIV algorithm has few major drawbacks and it is still prone to Known-plaintext attacks.
V. U. K. Sastry et al. [8] - [10] customized the original Hill cipher by including interweaving, interlacing and iteration. Modified Hill cipher [8] [9] have avalanche effect and are believed to defend against any cryptanalytic attack. Many of the modifications such as how the interweaving and interlacing along with the iteration will strengthen the Hill cipher and the necessity of the number of iteration to be 16 are not argued. The crisis of non-invertible key matrix in Hill cipher is addressed by Rushdi et al. [11] . The key problem is resolved by translating each character of the plaintext to two cipher text characters but the computational complexity and duration is increased. Bibhudendra et al. [12] proposed AdvHill (Advanced Hill) algorithm to address the non- invertible matrix key issue by involving involutory matrix key for enciphering. The computational complexity is reduced by removing the inverse key calculation process in AdvHill algorithm.
Many researches are performed to improve the security flaws in Hill cipher by strengthening the key matrix. To prevent the vulnerability against the known plaintext attack Yeh et al. [13] make use of securely shared two co-prime numbers between the communication parties. Even though it reaches its basic objective it cannot be efficiently used for a bulk of data as it is time consuming and need many mathematical manipulations. Saeednia [14] proposed a secured Hill cipher by permuting the rows and columns of the key matrix randomly, still it is vulnerable to known plaintext attack. Once again V. U. K. Sastry et al. [15] modified the Hill cipher by masking the letters using Extended Binary Coded Decimal Interchange Code (EBCDIC) to support IBM mainframes. But it is not suitable energy constrained networks as the iteration process of the data is performed bit wise. In order to strengthen the Hill cipher the key dependent permutation and interlacing is used for large block size of the plain text in [16] . Again to make the cipher stronger author combined the modified Hill cipher with playfair cipher [17] .
Hill cipher is modified using Maximum Distance Separable (MDS) variable length key matrix to strengthen the security of the cryptosystem [18] . The security level of the cryptosystem is strengthen by modifying the private key matrix of the Hill cipher and proposed a double guard Hill cipher [19] . It supports ASCII values and the private key matrix is permutated to triumph over the known plaintext attack. Also, double protection is given to the cryptosystem by shuffling the enciphered text with respect to “t” matrix before transmitting so that it can overcome chosen plaintext attack, cipher text attack as well as chosen cipher text attack. Images can be transmitted energy efficiently in a secured manner by combining Losningen cross layer approach with the double guard Hill cipher algorithm (DGHC) in [20] . Further, the energy consumption can be reduced by reducing the computational time and by reducing the number of bits to be transmitted. In order to reduce the computation time efficiently, the number of calculation can be reduced to minimize the energy consumed in the proposed modified Double Guard Hill cipher (MDGHC).
2. A Modified Double Guard Hill Cipher with Non Square Matrix
The Double Guard Hill Cipher is modified with the non-square key matrix of the order (p × q) and the message matrix is obtained with respect to the values of p and q of key matrix. This novel modification is performed expecting to reduce the computational time and the number of bits transmitted. The permutation procedure is replaced by simply exchanging either rows or columns without changing its determinant. The encryption and decryption algorithm of the proposed modified double guard Hill cipher is
2.1. Encryption Algorithm
The encryption algorithm (Figure 1) to convert the plaintext into cipher text is
1) Let [K] by the non-square key matrix of p × q. If p > q, it is called as vertical matrix else it is horizontal matrix.
2) The message matrix [M] is arranged according the key matrix [K].
For vertical key matrix: order of the message matrix [M] is q × n.
For horizontal key matrix: order of the message matrix [M] is m × p.
3) Obtain the encrypted cipher matrix [C] by
For vertical key matrix:
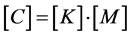 (1)
(1)
For horizontal key matrix:
 (2)
(2)
Note: In a non-square matrix, two matrix [A] and [B] of different order is not associative.
4) Before transmitting, the rows and columns are interchanged so that it is prone to various attacks like “known plain text attack”, “chosen plain text attack”, “cipher text attack” as well as “chosen cipher text attack”.
![]()
Figure 1. Encryption algorithm of modified double guard hill cipher.
![]()
Figure 2. Decryption algorithm of modified double guard hill cipher.
Thus the encrypted matrix is obtained for transmission. As the permutation of the key matrix is not performed, there is no need to transmit the “t” matrix along with the encrypted matrix.
2.2. Decryption Algorithm
The decryption algorithm (Figure 2) to convert the cipher text to the plaintext is
1) Received encrypted matrix is rearranged with respect to the key matrix.
2) Plain text is obtained by multiplying the Mod-128 inverse key with the rearranged encryption matrix.
For vertical key matrix,
 (3)
(3)
For horizontal key matrix,
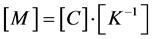 (4)
(4)
Note: According to theorem 1 [21] , right inverse exist for horizontal matrix and left inverse exist for vertical matrix.
Theorem 1
Every non singular horizontal matrix A having a right inverse 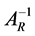 such that
such that
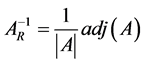
2.3. Illustration of Proposed Modified Double Guard Hill Cipher
The modified Double Guard Hill Cipher is illustrated with a sample message as
Message: “Meet on 3-3@ #R”
ASCII value: [77 101 101 116 32 111 110 32 51 45 51 64 35 82]
Encryption for vertical key matrix:
Key matrix of order 4 × 3: 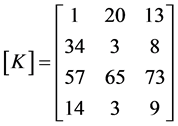
Since the message matrix should have 3 × n, it is arranged to 3 × 5 for the given key matrix. Arrange [M] column wise
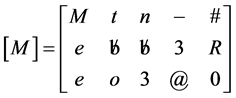
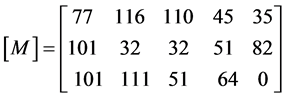
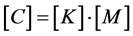
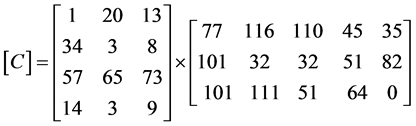
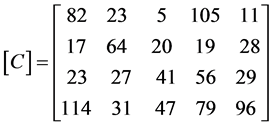
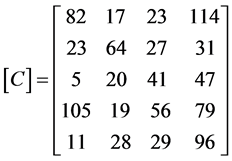
The encrypted matrix in row wise,
[C] = [82 17 23 114 23 64 20 19 28 23 27 41 56 29 114 31 47 79 96] is transmitted.
Decryption for vertical key matrix:
The received encrypted cipher matrix is rearranged column wise with respect to the column of mod-128 inverse of the key matrix, [K−1]
![]()
Note: The determinant of the non-square matrix is obtained by using the Theorem 2 and the modulo inverse of the non-square matrix is obtained by Theorem 3.
Theorem 2
The determinant of a non-square matrix is given as
If ![]() then its
then its ![]()
If ![]() then its
then its ![]() where
where
![]()
Theorem 3
Inverse of the non-square matrix is given by
![]() where cofactor is given by
where cofactor is given by![]() ,
, ![]() is minor of
is minor of![]() .
.
The mod-128 inverse of the key matrix [K] is
![]()
![]()
![]()
![]()
Similarly the encryption and decryption for horizontal key matrix can be performed.
The cipher text obtained by using the vertical key matrix and horizontal key matrix are different for the same plaintext. Similarly, according to the non-square matrix theorem, right inverse matrix exist for the horizontal matrix and left inverse matrix exist for the vertical matrix. The original plaintext cannot be retrieved if the inverse matrices are multiplied reversely.
In the modified double guard Hill cipher the encryption time is reduced as it avoid the permutation and the transmitted are reduced as it avoids the transmission of ‘U’ matrix along with the cipher text. The execution time and the encryption speed (Table 1) of the modified double guard Hill cipher is compared with large block cipher involving key dependent permutation, interlacing and iteration, block cipher with the blending of Hill cipher and playfair cipher, double guard Hill cipher and the contemporary ciphers such as DES and AES.
The proposed cipher is strengthened against the ‘known plaintext attack’ without the procedure of permutation by the property of non-square matrix and shuffling the order of the cipher text. The transmission of ‘U’ matrix along with encrypted cipher text in double guard Hill cipher is eluded by evading permutation. So, in the modified double guard Hill cipher the encryption time is reduced by reducing the number of computation, also it reduce the bits transmitted when compared with double guard Hill cipher. The proposed cipher is capable of encrypting the data faster than the various ciphers.
![]()
Table 1. Comparison of encryption speed and execution time of the proposed cipher with other ciphers.
3. Secured Data Transmission Using Modified LEHS
In Wireless Sensor Network (WSN), data can be securely transmitted in an energy efficient manner using modified LEHS (Low Energy High Secured) algorithm. In modified LEHS algorithm, the backbone of the network to transmit the data to the base station is configured by Losningen cross-layer approach (LCA) to enable the energy efficient transmission in order to enhance the network’s lifetime and the data is secured using modified Double Guard Hill cipher. Losningen approach [22] merges the MAC layer, sublayer of the data link layer, with network layer. Normally for various services and protocols, the lowest layers of the system were used maximally to pass information to the higher layers. So the cross layered approach of merging MAC layer with network layer is carried out to obtain the information about the link quality and the congestion from the MAC layer when routing is performed. This achieves the energy efficiency by balancing the network traffic that limits the queuing delay and packet loss due to the traffic. So, the objective of enhancing the network’s lifetime with reasonable delay and throughput is obtained by implementing the cross layer approach for routing. This approach will provide the overall view of underlying information to the routing layer for choosing the better path.
Routing performance can be increased enormously by this approach as the link quality and the congestion information are revealed to network layer immediately. The cross-layer designs with tight coupling between many layers become hard to review and redesign. Since changing one subsystem leads to changing of all other parts because of interconnection. Hence in Losningen cross layer approach, the merging of MAC layer with the network layer preserves the modularity of the network to ease the review and redesign for the future enhancement.
An earnest effort has been made to develop the cross layer approach [20] that improves the throughput by 1.7 times higher than the network without cross layer approach with AODV routing protocol. Network’s lifetime is prolonged by 1.2 times more by the proposed approach. It is achieved by reducing 42% of data packet loss. The end-to-end delay is reduced by the factor of 1.5 by reducing the delays caused by route discovery, queuing delay at network interface and retransmission delays due to the transmission of data from source to sink.
At the network layer, the traffic is balanced through the AOMDV routing protocol. AOMDV routing protocol allows significant energy conservation as it has the ability to reduce the route discovery frequency. This routing algorithm is on-demand algorithm that enables self-starting, dynamic, multihop routing when a source node wants to send a data packet. Since the routing messages are of small fixed length packets and uses it on-demand basis, it suits well for WSNs. As it is capable of providing multiple redundant paths, the data can be transferred using alternate path during path failure.
The three main phases of this algorithm are route discovery, route updation and route re-establishment. When a node wants to transmit a data to another node without prior knowledge of the destination, it enables the route discovery phase by flooding the route request (RREQ) in order to notify the destination of the data packet. To minimize the energy required for flooding, the length of the request is small and constant.
The propagation of RREQ from the source to the sink (destination) node launches multiple reverse paths at the intermediate nodes as well as the destination nodes. The frequency of route discovery is reduced as the AOMDV routing protocol provides the alternate paths for the intermediate nodes too. The destination node responds to the first received request and discards the duplicate ones. It sends the route reply (RREP) back to the source node on the fastest route called on-route nodes. This routing protocol establishes and maintains efficient routes in dynamic topology. When the routes are disconnected, the routing protocol makes use of local topology information gathered by the medium access protocol to re-establish the route efficiently.
Performance of the modified LEHS algorithm for data transmission is simulated using network simulator-2 (NS2). Simulation results are obtained by considering maximum of 100 nodes randomly deployed in a uniform rectangular field of dimension 1000 m × 1000 m. Traffic pattern between the chosen source sink pair consist of several CBR/UDP connections. Let the packet size be 500 bytes and the number of packets transmitted per second be 25 with the packet transfer interval time of 0.04 seconds.
The metric used to evaluate the performance is network lifetime. Network lifetime measures the amount of time before a certain percentage of sensor nodes run out of battery power. During the simulation, the whole network is considered to be down when 25% of the normal sensor nodes are depleted of power. The simulation result of modified LEHS algorithm for data transmission is compared with LEHS algorithm with DGHC in order to prove the enhancement of network’s lifetime. From the readings, the network lifetime of LEHS-MDGHC is seems to be enhanced by 2.4 times than LEHS-DGHC as shown by Figure 3.
![]()
Figure 3. Comparison of network lifetime between LEHS-DGHC and LEHS-MDHGC.
4. Conclusion
In the modified double guard Hill cipher, the non-square matrices are used as private key matrix. Because of the property of non-square matrix and obtaining the cipher text by twisting the order of the cipher text strengthen the proposed cipher against the “known plaintext attack” without the procedure of permutation. Also by avoiding permutation, the transmission of “U” matrix along with encrypted cipher text in double guard Hill cipher is eluded. So, in the modified double guard Hill cipher the number of computation is reduced by avoiding the permutation, also it reduce the bits transmitted when compared with double guard Hill cipher. The proposed cipher is capable of encrypting the data faster than the various ciphers. Therefore in future, it can be refined for image encryption in wireless sensor network in order to enhance the network’s lifetime for secure image transmission.