Research on Application of Mobile Agent Based on Immune Algorithms in Ad Hoc Network ()
1. Introduction
Mobile Ad Hoc network [1] is a collection of multiple mobile nodes that can communicate with each other without fixed infrastructure and network topology can arbitrarily change. As a kind of special wireless network, nodes in network generally consist of mobile terminal. Because Ad Hoc network has characteristics of open media, dynamic topology, lack of center authentication mechanism, and limited node ability, compared with traditional network, it has more network security problems. Security problems have become choke point to hinder the development of Ad Hoc network. Attacks in Ad Hoc network can be divided into “active attack” and “passive attack”. Active attack can be detected easily but passive attack has high concealment and it is not easy to be found [2] . While mobile agent based on immune system can well monitor each node in the network, timely find its misconduct and make use of the immune ability of the network to restore the health of network nodes or eliminate it out of the entire network. This article will focus on how to apply immune algorithms and mobile agent to improve network security performance in Ad Hoc network.
2. Immunology Principle
2.1. Immune System
Immune system is a highly collateral distributed, adaptive information processing learning system [3] . The system can recognize self and non-self materials, eliminate and defend foreign invasive viral substances or molecules. In order to recognize self and non-self materials, in biological systems, it usually has T cells that specially detect antigen and B cells that produce antibody. There are two types of T cells. One kind is the helper T cell Th that is in the majority to be responsible for promoting B cells to secrete antibodies and strengthen the immune function of T cells and macrophage; another kind is suppressor T cell Ts, which activates under the action of cytokines to form effector cell and eliminate bad cells.
The immune response can be divided into three phages: immune recognition phase, antibody production stage, antigen elimination stage.
1) Immune recognition phase: when external antigen enters in the system, at first, the T cell does immunological recognition. If it recognized similar antigen and retain the information before, the memory part of T cell will combine with the antigen to realize immunological recognition;
2) Antibody production stage: if T cell has recognized the antigen, T cell will be activated and stimulate B cell to secrete large amounts of antibodies;
3) Antigen elimination stage: antibodies produced by B cell combine with antigen, which destroy the activity of antigen and it excretes the antigen out of the body. The antigen disappears, and the immune system returns to normal.
2.2. Immune Algorithms
Immune algorithm is the learning algorithm based on the immune system [4] , and there are four basic elements, antigen recognition, antibody formation, immune selection and immune memory respectively. In the algorithm, regard the objective function of the optimal solution as the antigen, including problems to be solved and various constraint conditions. Solve the fitness function 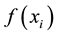 of
of 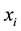 and regard it as antigen, search the direction and the distribution of solution group according to concentration adaptive modulation of antibody. The representa-
and regard it as antigen, search the direction and the distribution of solution group according to concentration adaptive modulation of antibody. The representa-
tion of immune selection is . Immune memory refers to reserving the solving result of a
. Immune memory refers to reserving the solving result of a
specific problem and characteristics and parameters of the problem as initial solutions to solve the similar problems next time so as to accelerate the solving speed and effect.
The process to realize immune algorithms is as follows:
1) Initialization, randomly generate initial B cell mass 
2) Calculate the fitness of each B cell to generate antibodies 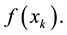
3) Save B cell with the optimal antibody as immune memory cell 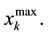
4) Calculate the concentration of antibody and generate B cell mass  according to the probability of immune selection.
according to the probability of immune selection.
5) 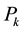 forms the next generation
forms the next generation 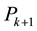 of B cell through clone and differentiation.
of B cell through clone and differentiation.
6) If immune memory cell hasn’t completely recognized antigen, return to step 2).
3. The Working Mechanism of Mobile Agent
Agent technology derives from artificial intelligence domain [5] , can simulate human behavior and relationships and it is a procedure that can run independently and provide specific service. It can sense the environment change, make judgment and reasoning for changes and form the decision to control corresponding behavior and complete a task. Compared with traditional distributed computing model, mobile agent technology has many advantages, such as save network bandwidth, support off-line calculating, unrelated to platform and balance computation load, etc. In the network environment, under the self-control, the mobile agent can move from one computer to another computer, hang up at any point, and it continues execution from the hanging point when moving to a new machine. Under normal circumstances, mobile agent system (MAS) includes mobile agent MA and mobile agent platform MAE. Mobile agent platform is responsible for establishing safe and correct operation environment for mobile agent, providing basic services and forming restriction mechanism, fault-tolerance strategy and security control for MA. The mobility of mobile agent and the solving ability of problems depend largely on the services provided by mobile agent platform.
4. The Application of Immune Agents in Ad Hoc Network
Because the Ad Hoc network topology is changeful, the establishment of a connection mode completely depends on the location of each node and coverage area of their transceiver. Each node in the network is equivalent to a router, realizing the retransmission of information packet and participating in the discovery and maintenance of route. Ad Hoc network brings convenience to people and is faced with serious security threat. Attacks from network can be divided into passive attacks and active attacks. Under passive attack mode, attackers don’t interfere with the communication of network nodes and their purpose is to obtain sensitive information in the network; active attack refers to that the attackers interfere with or destroy the communication of network nodes and cause that the network nodes cannot work normally. Flooding DDOS attack is a typical attack type. In order to early find misbehavior nodes in network and maintain normal communication of the system, this article combines immune algorithm with mobile agent and applies them to Ad Hoc network, makes network node can dynamically monitor change situation of other nodes in network, timely remove or restrict the behavior of misbehavior nodes and realize autonomous management of network nodes under the circumstances of no one involved.
4.1. Working Model of Immune Agent
It is easy to find the corresponding relation between immune system and Ad Hoc network through analyzing the division of labor of lymphocyte, T cell, B cell and the working mechanisms of mobile agent in immune system. The security architecture of Ad Hoc network is equivalent to the entire immune system; misbehavior nodes in Ad Hoc network are equivalent to the antigens in immune system; normal nodes in Ad Hoc network are equivalent to healthy cells in immune system; mobile agent in Ad Hoc network is equivalent to lymphocyte in immune system and responsible for transporting other agents with specific function. In view of the function of T cell and B cell, three types of agents have been set in the system, and they are monitoring agent, coordinating agent and blocking agent respectively. Monitoring agent is equivalent to T cell in immune system, distributes in all the nodes of the whole system, and it is responsible for collecting behavior information of neighbor nodes and regularly reports it to coordinating agent; coordinating agent distributes in different areas of the network and it is equivalent to B cell in immune system and responsible for arranging the information of nodes in the charge of it in the network and storing it into information memory bank. When coordinating agent receives a new report, it will compare the report with the information in memory bank and strategy library. If it is normal information, the agent will ignore it; if it isn’t normal behavior information (if a node receives routing information and doesn’t transpond), judge the time difference of bad report at the same node in last time. If the interval is nearer, then accumulate. Otherwise, remove the bad report number of this node. If it exceeds the threshold value, activate the blocking agent. Blocking agent is equivalent to antibody in immune system and can clone itself. Its task is to eliminate the misbehavior nodes [6] . Coordinating agent needs certain tolerance and can tolerate a small amount of bad behavior of individual nodes (some bad behaviors may be caused by network interference).
The safety verification of antibody moving from point  to
to 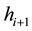 is described as follows:
is described as follows:
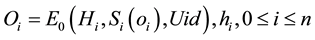
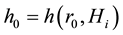
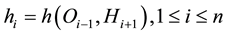
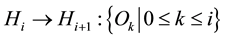
When the antibody begins to roam, ![]() produces a random number
produces a random number ![]() and a
and a![]() , and then calculate
, and then calculate ![]() and
and![]() , send
, send ![]() to
to![]() . When the antibody reaches
. When the antibody reaches![]() ,
, ![]() checks the chain relationship
checks the chain relationship![]() .
.
When the antibody moves to the position near the goal node, it clones, mutates and compresses [7] and produces a large number of antibodies that can kill the “virus”. These antibodies will isolate the communication between misbehavior nodes and other nodes in network and achieve the purpose of eliminating harmful nodes. When misbehavior nodes disappear, blocking agent will vanish by itself.
The mathematical description of antibody clone is as follows:
For binary coding, antibody![]() . Among them,
. Among them, ![]() represents the collection formed by all the binary strings with length of l. Antibody cluster
represents the collection formed by all the binary strings with length of l. Antibody cluster ![]() is n tuple of antibody a.
is n tuple of antibody a.
Clone operator is defined as follows:![]() . Among it,
. Among it,
![]() .
. ![]() is
is ![]() dimensional row vector
dimensional row vector![]() . Usually take
. Usually take
![]() . Among it,
. Among it, ![]() is concerned set value of clone size and
is concerned set value of clone size and ![]() is
is
top integral function. After the clone operation, it generates intermediate population ![]() and
and![]() .
.
The mathematical description of the variation is as follows:
![]() , H is Hamming distance. After variation, it generates in-
, H is Hamming distance. After variation, it generates in-
termediate population ![]() and
and![]() .
.
The main effect of compression choice is to choose n antibodies with the highest affinity in intermediate population ![]() to form a new generation of antibody group
to form a new generation of antibody group![]() .
.
Evaluate the immune system in the form of weighted sum, and the evaluation function is ![]() . In this formula,
. In this formula, ![]() and
and ![]() are weighted system of stimulating effect and inhabitant activity.
are weighted system of stimulating effect and inhabitant activity.
4.2. Result Analysis
It is can be seen from Figure 1 that when there is no attack in network, the message delay maintains at a relatively low level and the network communication is normal shown in the figure as “●”; when the network appears attack, the delay rate of message will rise rapidly. With the extension of time, network performance becomes worse and worse and the worst result is network paralysis, shown as “▲”; after applying the method of immune agent in network, the number of message delay of the system will reduce sharply, shown as “■”. Although it is higher than the message delay rate when there is no attack, it is still in a lower level and acceptable.