1. Introduction
Counterfeiting product is one of the serious problems that most product manufacturers and customers have to confront. The intent to make counterfeiting products is to take advantage of the original value of the genuine products. According to the report of International Chamber of Commerce (ICC), the global market loss due to counterfeiting products reaches $1.7 trillion by 2015 [1]. As a result, several countermeasure solutions have been proposed such as the barcodes, the hologram stickers, and the Radio-Frequency Identification (RFID) tags.
Among the aforementioned countermeasures, RFID technology is the most viable solution for product anti- counterfeiting due to the difficulty for the adversary to access to the sensitive information, e.g., the tag identity and the tag authenticity, of the RFID tag. Typically, each tag is equipped with an authentication protocol which provides more rigorous access control to the tag information. The verifier has to successfully pass the authentication procedure to get this information. Thus, the RFID tag with an authentication protocol is a viable and proactive solution for anti-counterfeiting. Currently, the tag-side authentication protocol [2] [3] and the mutual authentication protocol [4]-[7] have been proposed for anti-counterfeiting.
Obviously, the latter protocol is more secure than the former protocol as it requires both sides of the protocol - the server and the tag-to get authenticated. However, we argue that the mutual authentication protocol is inappropriate for use in product retailing systems. First, since the mutual authentication protocol takes time to authenticate the server, to update and to synchronize the secret shared between the server and the tag [4]-[7], it increases the computation and the communication cost whereas most of the tags used in consumer products has weak computational resources. Second, the update and synchronization of the secret shared between the tag and the server can be suffered from the de-synchronization problem [4]. Finally, if the server authenticity must be taken into account, the tag might intentionally refute the authentication request from the verifier by abusing the server authenticity. Instead, customers should be able to verify any tag without hindrance from the tag. Thus, a secure tag-side authentication protocol where tags have to answers their proof of authenticity for any request is sufficient for use in the retailing system.
Additionally, the current proposed RFID authentication systems for anti-counterfeiting do not consider the role of the product seller. These systems consist of three parties: the RFID tag, the reader, and the server [8]-[10]. Meanwhile, the sellers/retailers always exists in the retailing system. Hence, in this paper, our anti-counterfeiting system considers the role of the seller. In the retailing system, a seller who distributes products can be either an authorized entity or an unauthorized one. If a seller is honest (authorized), he can support the product anti- counterfeiting systems. In contrast, if the seller is dishonest (unauthorized), he may conspire with the adversary in selling counterfeit products along with the genuine ones in his shop. Thus, to improve the anti-counterfeiting capability, we need a mechanism in which the seller has to support the anti-counterfeiting whilst refraining him from being dishonest. The contributions of our paper are summarized as follows:
l We propose an RFID-based anti-counterfeiting system consisting of two protocols: the tag authentication protocol and the database correction protocol. The tag authentication protocol increases the usability for the customers by allowing them to authenticate RFID tags without the need of authenticating the reader and the server. Meanwhile, the database correction protocol helps the seller and the server to update the tag status in the server database periodically.
l The proposed anti-counterfeiting system is secure against various attacks such as RFID tag counterfeit, seller impersonation, server impersonation and the database spoiling attack. Further, the proposed system not only allows the customer to detect the counterfeit tags, but also reduces the market loss due to counterfeit products.
The remainder of this paper is organized as follows. Section 2 discusses several related work. Section 3 describes the RFID-based anti-counterfeiting model and the both tag authentication protocol and database correction protocol in detail. Section 4 discusses the function $F$ which involves in the tag authentication protocol. Section 5 analyzes the security of the anti-counterfeiting system. Section 6 analyzes the efficiency and the usability of our system. Finally, Section 7 concludes our paper.
2. Related Work
In recent years, researchers have been proposed numerous RFID-based systems for solving the counterfeiting problem [4] [5] [7] [11]. Their RFID systems consist of three parties: the server, the reader, and the RFID tag. They consider the reader and the server as an integrated entity. They assume that the communication channel between them are secure.
Although the mutual authentication protocols allow the two parties to authenticate each other, they also require the RFID tag to do more computational tasks such as random number generation and tag identity number update [6] [9] [12]. Paradoxically, most of the RFID tags belong to low-cost passive class, which means they have limited hardware resources and need the power supplied from the reader’s radio energy.
Additionally, the mutual authentication protocols [9] [13]-[15] usually need to update and synchronize the secret information shared between the tag and the server database after each authentication session. The adversary can exploit this task to destroy the functionality of the tag by de-synchronizing the common information shared between the server database and the tag [4] [16]-[18]. As a result, we only need tag-side authentication RFID system which can prevent counterfeiting problem while allowing the customer (the reader) to freely inquire the tag without the need to update the common information shared between the tag and the server database.
In terms of tag-side authentication, several schemes have been proposed [2] [3]. However, several limitations makes them inappropriate for use in the retailing system. Typically, the OSK protocol [2] suffers from the de-synchronization problem due to the update operation between the tag and the server database after each authentication session. Although this problem has been solved in the work of Godor et al. [6], their protocol is mutual authentication category, and hence it is not suitable for the context of retailing system. Our work can be considered as a variant of the Feldhofer et al. scheme [3] which is ISO/IEC 9798-2 unilateral authentication standard. However, this scheme uses AES encryption for providing the proof of identity. Note that AES encryption primitive is not compatible for lightweight application, especially for RFID tag [19]. Therefore, this scheme is not practical in the retailing system.
3. The Proposed Anti-Counterfeiting System
3.1. System Model
The RFID tag, the reader, the server, and the seller are the four parties of the RFID anti-counterfeiting system. Each RFID tag, attached on a product, stores the unique 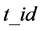 and the corresponding secret . The reader is a device used by the customer to verify if a product is genuine. A reader might be a smart phone with the authentication protocol downloaded from the product manufacturer. The product manufacturer (the tag issuer) maintains a database of the tags. The entities of the database are the tag identification number
and the corresponding secret . The reader is a device used by the customer to verify if a product is genuine. A reader might be a smart phone with the authentication protocol downloaded from the product manufacturer. The product manufacturer (the tag issuer) maintains a database of the tags. The entities of the database are the tag identification number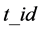 , the secret
, the secret , the tag status
, the tag status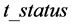 , and the seller name
, and the seller name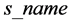 . Each tag has unique
. Each tag has unique 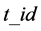 and the corresponding secret .The tag status
and the corresponding secret .The tag status 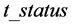 is either
is either 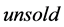 or
or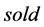 . When issuing a tag, the product manufacturer assigns
. When issuing a tag, the product manufacturer assigns 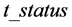 to
to 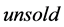 in the server database. The server uses the database to authenticate and to maintain the status of tags. Whenever a product is shipped to a seller, the information of the tag is created to the database as shown in Table 1.
in the server database. The server uses the database to authenticate and to maintain the status of tags. Whenever a product is shipped to a seller, the information of the tag is created to the database as shown in Table 1.
The tag authentication protocol and the database correction protocol are the two protocols in the RFID anti-counterfeiting system. Through the tag authentication protocol, the sever verifies if a specific product is genuine. Then the sever notifies the result (either 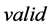 or
or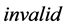 ) to the reader. In this protocol, the server checks two things. One is to check whether the inquired product has been already sold out. If this is the case, the server sends the message
) to the reader. In this protocol, the server checks two things. One is to check whether the inquired product has been already sold out. If this is the case, the server sends the message 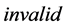 to the reader. Another one is to check whether the tag stores the secret
to the reader. Another one is to check whether the tag stores the secret 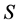 as same as the one stored in the server database. If both secrets do not match, the server also sends the message
as same as the one stored in the server database. If both secrets do not match, the server also sends the message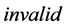 . The message implies that the product is a fake. The server sends the message
. The message implies that the product is a fake. The server sends the message 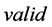 to the reader only when the product is unsold and the tag’s secret is matched as well.
to the reader only when the product is unsold and the tag’s secret is matched as well.
In this RFID anti-counterfeiting system, the server always updates the database by changing the tag status for any inquired product. By doing this, the system prevents selling fake products with the same tag identification number more than once. However, a customer may visit a shop checking the genuineness of several products and leaves without buying anything. In this case, the database needs to be corrected by changing the tag status from ![]() to
to![]() . This can be done by the database correction protocol. The server finds the seller of an inquired product from the database and sends him the tag identification number. If the product has been actually sold out, the seller does not need to do anything. Otherwise, the seller sends the message to the sever that the product is not sold out. If this is the case, the server updates the database by changing the tag status back to
. This can be done by the database correction protocol. The server finds the seller of an inquired product from the database and sends him the tag identification number. If the product has been actually sold out, the seller does not need to do anything. Otherwise, the seller sends the message to the sever that the product is not sold out. If this is the case, the server updates the database by changing the tag status back to![]() . Table 2 shows the notations used in the protocol.
. Table 2 shows the notations used in the protocol.
3.2. The Tag Authentication Protocol
The players of the RFID tag authentication protocol are the server, the reader, and the tag. The purpose of this protocol is to verify if a product is genuine. The reader initiates the protocol by sending a query to the tag. The query consists of two numbers, a tag identification number ![]() and a random number
and a random number![]() . The
. The ![]() can be
can be
found from the sticker on the product. Then the tag checks if the received ![]() matches with its own tag identification number. If so, the tag computes the response
matches with its own tag identification number. If so, the tag computes the response ![]() and sends
and sends ![]() to the reader. If not, the tag does not respond and the protocol terminates. Here the function
to the reader. If not, the tag does not respond and the protocol terminates. Here the function ![]() is a one-way function, which is described in Section 4. If the reader receives the response
is a one-way function, which is described in Section 4. If the reader receives the response ![]() from the tag, it generates another random number
from the tag, it generates another random number![]() . And then the reader sends
. And then the reader sends![]() , which is the encryption of four numbers,
, which is the encryption of four numbers, ![]() and
and ![]() by the server’s public key
by the server’s public key![]() . By this encryption, only the server knows the second random number
. By this encryption, only the server knows the second random number![]() . After receiving the encrypted message
. After receiving the encrypted message ![]() from the reader, the server decrypts it using his private key
from the reader, the server decrypts it using his private key![]() . The server checks if the database has the tag information corresponding to
. The server checks if the database has the tag information corresponding to![]() . If not, the server does nothing and the protocol terminates. If so, then the server checks the tag status. If the tag status is
. If not, the server does nothing and the protocol terminates. If so, then the server checks the tag status. If the tag status is![]() , the server sends the message
, the server sends the message![]() . If the tag status is
. If the tag status is![]() , the server computes
, the server computes ![]() and check if
and check if![]() . If so, the server sends the message
. If so, the server sends the message![]() , and changes the tag status to
, and changes the tag status to![]() . Otherwise, the server sends the message
. Otherwise, the server sends the message![]() .
.
![]()
3.3. The Database Correction Protocol
The seller and the server are the two players of the database correction protocol. The server uses this protocol to request the seller report the current status of the tag inquired by the reader. After the inquiry from the reader, the server changes the tag status ![]() from
from ![]() to
to ![]() in the database. If the customer buys the product with this tag, the tag status
in the database. If the customer buys the product with this tag, the tag status ![]() is correct, and the server does not need to update the database. However, if that product is not sold out,
is correct, and the server does not need to update the database. However, if that product is not sold out, ![]() should be changed back to
should be changed back to![]() . To do this, the server has to correct
. To do this, the server has to correct ![]() in its database before the next authentication session. For increasing the security of the protocol, the server and the seller use the public key infrastructure to exchange their messages. We assume that their public keys
in its database before the next authentication session. For increasing the security of the protocol, the server and the seller use the public key infrastructure to exchange their messages. We assume that their public keys ![]() and
and ![]() are distributed by a trusted certificate authority (CA).
are distributed by a trusted certificate authority (CA).
For requesting the seller to report the current status of the inquired tag, the server sends the seller the message![]() ,where
,where ![]() is the identity number of the inquired tag, and
is the identity number of the inquired tag, and ![]() is a random number. After receiving
is a random number. After receiving![]() , the seller decrypts it using his private key
, the seller decrypts it using his private key ![]() to get
to get ![]() and
and![]() . If the product with
. If the product with ![]() is not sold, the seller responds the server the message
is not sold, the seller responds the server the message![]() . Otherwise, the seller responds with the message
. Otherwise, the seller responds with the message![]() .Once receiving
.Once receiving ![]() or
or![]() , the server decrypts it, and check received
, the server decrypts it, and check received ![]() with the original version (the
with the original version (the ![]() generated by the server). If they are matched, the server updates the database. Otherwise, the server terminates the protocol without updating the database. The use of
generated by the server). If they are matched, the server updates the database. Otherwise, the server terminates the protocol without updating the database. The use of ![]() guarantees that the message
guarantees that the message ![]() or
or![]() , is sent from the legitimate seller. The database correction protocol is described follows.
, is sent from the legitimate seller. The database correction protocol is described follows.
Remark 1. By changing ![]() to for all of the inquired tags, the adversary-who can make a large number of counterfeit tags (products) with the same
to for all of the inquired tags, the adversary-who can make a large number of counterfeit tags (products) with the same ![]() -could only sell at most one counterfeit product before the server changes the tag status
-could only sell at most one counterfeit product before the server changes the tag status ![]() to
to![]() . Once a product has
. Once a product has ![]() status, this fact discourages the customer’s willingness to buy this product. Thus, the customer might not buy it, or buy it with a price significantly cheaper than the $unsold$ product. Note that the adversary only gets benefit from counterfeit products when he sella large number of them. Hence, it is not worth for him to sell only one fake product. Therefore, our anti- counterfeiting system reduces the market loss significantly in the case when the secret
status, this fact discourages the customer’s willingness to buy this product. Thus, the customer might not buy it, or buy it with a price significantly cheaper than the $unsold$ product. Note that the adversary only gets benefit from counterfeit products when he sella large number of them. Hence, it is not worth for him to sell only one fake product. Therefore, our anti- counterfeiting system reduces the market loss significantly in the case when the secret ![]() is disclosed to the adversary.
is disclosed to the adversary.
Remark 2. The seller involves in the RFID system for updating the tag status ![]() from
from ![]() to
to ![]() after a tag is inquired by the customer. As we explain in Remark 1, the customer is unwilling to buy a product having
after a tag is inquired by the customer. As we explain in Remark 1, the customer is unwilling to buy a product having ![]() tag status even though it is a genuine one. However, the server always changes
tag status even though it is a genuine one. However, the server always changes ![]() to
to ![]() every time a tag is inquired by a customer by using a reader. Hence, we need the seller to change
every time a tag is inquired by a customer by using a reader. Hence, we need the seller to change ![]() back to
back to![]() ―via the database correction protocol (Protocol 2)―when the product with this tag is still in the shop (Note that the reader can only check the product’s status). As well, the sold fake product can be identified immediately when the server notifies the legitimate seller of product through the database correction protocol.
―via the database correction protocol (Protocol 2)―when the product with this tag is still in the shop (Note that the reader can only check the product’s status). As well, the sold fake product can be identified immediately when the server notifies the legitimate seller of product through the database correction protocol.
4. Function F
The successful probability of figuring out the inputs of ![]() from the output must be negligible. This is the most important requirement for
from the output must be negligible. This is the most important requirement for![]() . Specifically, the tag uses the output
. Specifically, the tag uses the output ![]() of
of ![]() to prove his knowledge about the secret
to prove his knowledge about the secret ![]() in the tag authentication protocol. If the tag is legitimate, i.e., it has the correct secret
in the tag authentication protocol. If the tag is legitimate, i.e., it has the correct secret ![]() corresponding to
corresponding to![]() , the tag can compute the
, the tag can compute the ![]() accurately. However, because the adversary can eavesdrop
accurately. However, because the adversary can eavesdrop ![]() in Protocol 1 (step 3.2), it must be impossible for the adversary to figure out
in Protocol 1 (step 3.2), it must be impossible for the adversary to figure out ![]() from
from![]() . Further, for authenticating the tag, the server only needs to verify the correctness of
. Further, for authenticating the tag, the server only needs to verify the correctness of ![]() instead of getting back S from
instead of getting back S from![]() .
. ![]() must be lightweight enough for use in low-cost RFID tags as well. Specifically, the number of logic gates (GE) used for implementing
must be lightweight enough for use in low-cost RFID tags as well. Specifically, the number of logic gates (GE) used for implementing ![]() must be less than 2000 GEs, which is the hardware budget for the security function in the RFID tag [8] [20]. Therefore,
must be less than 2000 GEs, which is the hardware budget for the security function in the RFID tag [8] [20]. Therefore, ![]() must be lightweight and secure one-way function. With this principal, we can choose an appropriate hash function having a decent collision and pre-image resistant level for our RFID system.
must be lightweight and secure one-way function. With this principal, we can choose an appropriate hash function having a decent collision and pre-image resistant level for our RFID system.
Recently, there are numerous lightweight hash function such as PHOTON [21], QUARK [22] and SPONGENT [23]. Among these lightweight hash functions, we choose SPONGENT-128 (128-bit output) as it requires the smallest number of GEs for implementation while providing decent collision and pre-image resistance level for RFID-based applications. Specifically, SPONGENT-128, PHOTON -128, and QUARK-128 require 1122, 1379, and 1060 GEs, respectively. Further, SPONGENT-128 provides 120-bit collision resistance and 64-bit pre-image security, which is strong enough for RFID-based applications.
To adapt the SPONGENT-128 hash function in our RFID system, ![]() is assigned as the initial value of
is assigned as the initial value of ![]() while the random number
while the random number ![]() is concatenated with the secret
is concatenated with the secret ![]() before being processed by
before being processed by![]() . The bit-size of
. The bit-size of ![]() should be smaller than the memory size of the tag, but must be long enough to prevent the brute-force search attack. As the memory of the popular low-cost tag is up to 512 bits [24] [25], we choose the size of
should be smaller than the memory size of the tag, but must be long enough to prevent the brute-force search attack. As the memory of the popular low-cost tag is up to 512 bits [24] [25], we choose the size of ![]() is at least 128 bits, which satisfies both the memory size and the security requirement.
is at least 128 bits, which satisfies both the memory size and the security requirement.
5. Security Analysis
5.1. Adversarial Model
The adversary will exploit the weaknesses of the RFID system to achieve malicious goals. In [8], the authors classify adversaries based on their goals, level of interference, and available resources. In our model, we assume that there are two major goals of the potential adversary: 1) to counterfeit tags by stealing the secret information of the tags; 2) to corrupt the system functionality by attacking the server database. Additionally, the adversary can be a dishonest seller, who wants to sell counterfeit products along with the genuine ones. Depending on the specific goal of the adversary, the damage of the RFID system is different. If goal (1) is accomplished, the tags of the RFID system will be suffered from being counterfeited, thus, a large number of fake products will be produced. Meanwhile, if goal (2) is successful, the server functionality, and the tag status will be corrupted, and hence, the RFID system cannot provide its authentication service for the honest customers and the honest sellers.
5.2. RFID Tag Counterfeit
To counterfeit an RFID tag, the adversary must know the secret ![]() corresponding to the tag number
corresponding to the tag number![]() . During authentication session, the reader and the tag transfer
. During authentication session, the reader and the tag transfer ![]() and
and![]() , the output of
, the output of![]() . Therefore, the adversary can use brute-force search technique to figure out
. Therefore, the adversary can use brute-force search technique to figure out ![]() from
from ![]() and X. Specifically, the adversary tries to search for the whole value space of
and X. Specifically, the adversary tries to search for the whole value space of![]() . Recall that
. Recall that ![]() is at least 128-bit length (Section 4), thus this length satisfies the key-size requirement according to the report on key lengths from ECRYPT II [26] and from NIST [27] [28]. Therefore, it is impossible for the adversary to do brute-force key search to find out
is at least 128-bit length (Section 4), thus this length satisfies the key-size requirement according to the report on key lengths from ECRYPT II [26] and from NIST [27] [28]. Therefore, it is impossible for the adversary to do brute-force key search to find out![]() .
.
Because ![]() operates as a hash function, the adversary can get
operates as a hash function, the adversary can get ![]() by using the collision or the pre-image attacks, which are popular attacks on hash function [29]. Typically, in the collision attack, the adversary tries to find two distinct inputs
by using the collision or the pre-image attacks, which are popular attacks on hash function [29]. Typically, in the collision attack, the adversary tries to find two distinct inputs ![]() and
and ![]() such that
such that![]() . In the pre-image attack, given
. In the pre-image attack, given ![]() produced by
produced by![]() , the adversary tries to find any
, the adversary tries to find any ![]() such that
such that![]() . However,
. However, ![]() is a cryptographic one-way function which has decent collision resistance and pre-image security level, as shown in Section 4.Thus, it is difficult for the adversary to find out an arbitrary
is a cryptographic one-way function which has decent collision resistance and pre-image security level, as shown in Section 4.Thus, it is difficult for the adversary to find out an arbitrary ![]() value different from the original
value different from the original ![]() value inside the RFID tag, which can cause
value inside the RFID tag, which can cause ![]() to generate the same
to generate the same ![]() value. In other words, the probability for the adversary to find out
value. In other words, the probability for the adversary to find out ![]() from
from![]() , and
, and ![]() is negligible.
is negligible.
5.3. Server Impersonation
To sell fake products, a dishonest seller must deceive a customer’s reader through the tag authentication protocol. To do this, he needs to make a fake server which generates the valid message ![]() for the reader’s inquiry. Here,
for the reader’s inquiry. Here, ![]() is the random number chosen by the reader. This
is the random number chosen by the reader. This ![]() is encrypted by the legitimate server’s public key
is encrypted by the legitimate server’s public key![]() , and then sent to the server. Hence, the seller cannot figure out
, and then sent to the server. Hence, the seller cannot figure out ![]() because he does not know the server’s private key
because he does not know the server’s private key![]() . This means that his fake server cannot generate the valid message
. This means that his fake server cannot generate the valid message![]() .
.
5.4. Seller Impersonation
An adversary may impersonate the legitimate seller. His goal is to corrupt the server’s database by keeping the tag status of the sold product as![]() . If this is the case, the impersonated seller (the adversary) can sell several counterfeit products with the same tag number
. If this is the case, the impersonated seller (the adversary) can sell several counterfeit products with the same tag number![]() .The only possible way is to send the message
.The only possible way is to send the message ![]() for the sold product with
for the sold product with ![]() through the database correction protocol. Here
through the database correction protocol. Here ![]() is the random number chosen by the server. This
is the random number chosen by the server. This ![]() is encrypted by the legitimate seller’s public key
is encrypted by the legitimate seller’s public key![]() , and then sent to the seller. If the impersonated seller does not have the correct seller’s private key
, and then sent to the seller. If the impersonated seller does not have the correct seller’s private key![]() , he cannot figure out
, he cannot figure out![]() . Therefore, the impersonated seller cannot generate the valid message
. Therefore, the impersonated seller cannot generate the valid message![]() . Additionally, whenever the server receives the message
. Additionally, whenever the server receives the message![]() , the server can identify the seller based on the seller’s name
, the server can identify the seller based on the seller’s name ![]() in the database. If the seller is an illegitimate agency, the server just ignores this wrong message. Otherwise, if the seller is a legitimate agency, the manufacturer can accuse him for this database corruption attempt later. The seller may lose the dealership. In other words, a legitimate agency will not do this wrong doing.
in the database. If the seller is an illegitimate agency, the server just ignores this wrong message. Otherwise, if the seller is a legitimate agency, the manufacturer can accuse him for this database corruption attempt later. The seller may lose the dealership. In other words, a legitimate agency will not do this wrong doing.
5.5. Database Spoiling Attack
Since the server always assigns ![]() to
to ![]() after the tag authentication protocol, the adversary who impersonates as a customer can exploit this fact to spoil the server database by requesting the server to authenticate a large number of genuine and unsold tags. Therefore, the honest seller cannot sell the products attaching these tags anymore. However, the seller can continue to sell these unsold products (these inquired tags) by requesting the server to correct
after the tag authentication protocol, the adversary who impersonates as a customer can exploit this fact to spoil the server database by requesting the server to authenticate a large number of genuine and unsold tags. Therefore, the honest seller cannot sell the products attaching these tags anymore. However, the seller can continue to sell these unsold products (these inquired tags) by requesting the server to correct ![]() in the database through the database correction protocol.
in the database through the database correction protocol.
5.6. Denial of Service Attack
Because anyone can freely request the server to authenticate the tag, the adversary can exploit this characteristic to conduct the Denial-of-Service (DoS) attack. However, we can efficiently mitigate this problem by asking the reader to solve the CAPTCHA puzzle [30] for each time the reader inquires the server. Specifically, between step 3.3 and 3.4 in the tag authentication protocol (Protocol 1), the server asks the reader to solve a CAPTCHA puzzle. Unless the reader solve this puzzle correctly, the server dose not proceed step 3.4. This additional procedure prevents the reader-which is controlled by the adversary-from automatically and continuously inquiring the server.
6. Protocol Efficiency and Customer Usability Analysis
6.1. Protocol Efficiency Analysis
In the tag authentication protocol, function ![]() is the main operation which the tag has to handle. Following the choice in Section 4, the
is the main operation which the tag has to handle. Following the choice in Section 4, the ![]() function requires 1060 GEs, which satisfies the hardware resource constraints for the low-cost RFID tag [8] [20]. In terms of number of operations, the tag has to handle one
function requires 1060 GEs, which satisfies the hardware resource constraints for the low-cost RFID tag [8] [20]. In terms of number of operations, the tag has to handle one ![]() operation; the reader has to handle one random number generation and one encryption operation; and the server has to handle one search operation, one
operation; the reader has to handle one random number generation and one encryption operation; and the server has to handle one search operation, one ![]() operation, and one decryption operation. Additionally, the database correction protocol only requires one encryption operation and one random number generation for the server and one decryption operation for the seller. As both the server and the seller have enough computational power to handle the public-key encryption, the practicality of the system is guaranteed.
operation, and one decryption operation. Additionally, the database correction protocol only requires one encryption operation and one random number generation for the server and one decryption operation for the seller. As both the server and the seller have enough computational power to handle the public-key encryption, the practicality of the system is guaranteed.
6.2. Customer Usability Analysis
Our proposed RFID system increases the usability for the customer as he can freely request the server to authenticate the tag without needing to identify himself to the server. The customer only needs to get the server’s public key and send the tag identification number printed on the product for authentication. Further, the customer can use any device that can communicate with the tag and handle the public-key encryption scheme to communicate with the server as a reader.
7. Conclusion
We have proposed an RFID anti-counterfeiting system, which is secure against the RFID tag counterfeit, the server impersonation, the seller impersonation, and the database spoiling attack. Our system not only can detect the counterfeit tag, but also reduces the market loss due to the counterfeit problem. Next, we strengthen the anti-counterfeiting capability of our system by changing the database update permission to the seller who is identified and authenticated by the server, instead of the reader. Consequently, our system improves the usability for the customer by removing the reader-side (the server-side) authentication, thus the customer can freely inquire the tag and the server in the tag authentication protocol. Finally, our system is practical as the tag only has to handle the one-way function![]() , which is compatible with the low-cost RFID tag.
, which is compatible with the low-cost RFID tag.
Acknowledgements
This work was supported by National Research Foundation of Korea under Grant NRF-2013R1A1A2016723.