Trust Assessment Model Based on a Zero Trust Strategy in a Community Cloud Environment ()
1. Introduction
Cloud Computing (CC), described as the fifth utility service, provides on-demand computing resources (hardware and software) via the Internet [1]. The significant gains in terms of financial revenues linked to the use of Cloud services and to rich and diversified service offerings have favored its adoption by companies [2]. However, organizations with high security requirements and legal considerations are reluctant to use Cloud services. This distrust of CC by these companies is due to the dependency on Cloud service providers and the security of sensitive data [3]. One solution to this problem is the use of the Community Cloud (3C) deployment model. The 3C is defined as an infrastructure shared by several organizations and supported by a specific community for the purpose of exchanging resources [4]. Each organization can offer services or make its excess or unused resources available to the community. As an example, a Community Cloud for the agricultural sector can provide relevant services with specific requirements (seed orders, crop rotation, stakeholder investments, soil management techniques, product exposure, etc.) and a required level of security (authentication, confidentiality, communication security, data protection, denial of service protection, supply chain traceability, etc.) for farmers and companies in the sector. In such an environment, managing trust between different entities is a major challenge to meet security requirements and encourage resource sharing [5]. Trust is a prerequisite for building sustainable relationships [6]. Several works related to trust management in CC have been done. L. Guo et al. presented in [7], a trust management model based on mutual trust with a reward and punishment mechanism. The special feature of this system is that it considers the opinions of the user and the provider by expressing mutual trust between them. InterTrust, a trust management technique based on subjective logic was introduced in [8]. It shows an improvement of the Trust Network Analysis with Subjective Logic (TNA-SL) trust management algorithm [9] in terms of the significant reduction in execution time. In addition, work has been done to ensure trust in federated cloud environments. Performance-based Risk driven Trust (PRTrust) was presented in [10]. This model allows the establishment of performance and risk-based trust for secure service sharing. It is an extension of the EigenTrust model [11] and is an effective tool for recommending services to users. A study in [12] presented TrustyFeer, a trust management system for improving service quality using subjective logic. This technique shows better results in terms of reducing non-SLA compliant services compared to TNA-SL and EigenTrust models. Most of the models mentioned above only address trust from a cloud service provider and or user perspective. Moreover, most of these trust assessment models are based on feedback from previous exchanges that may be biased by malicious entities [13] [14]. Furthermore, these assessments are made without considering the specificities of an environment such as the Community Cloud. It is important to address trust management in 3C by considering the social and community aspects on the one hand and the security threats internal and external to the system on the other. Therefore, this article proposes, a trust management model (SeComTrust) based on Zero Trust strategy principles in a community cloud. Zero Trust is an architectural concept that aims to enhance the security of resources and services of an information system [15] [16]. Our strategy is based on the subdivision of our 3C into security zones as in [17]. These security perimeters are groupings of organizations providing resources with levels of sensitivities established based on the common vulnerability assessment system (CVSS) [18]. The contributions of our approach are as follows:
A community cloud architecture model segmented into security domains for sharing resources with well-defined levels of vulnerabilities;
- A technique for evaluating and selecting a trusted organization;
- A mechanism for updating trust values allowing the promotion or relegation of organizations in the security domains.
In the rest of this paper, Section 2 presents the model and its operation. Section 3 describes the experiments and the associated results. Finally, section 4 concludes the article and proposes perspectives for the improvement of our model.
2. Community Cloud Trust Management Model (SeComTrust)
2.1. Research Hypothesis
The SeComTrust, is based on a community cloud consisting of organizations interacting with each other for the purpose of sharing resources. Our 3C is subdivided into three security domains: the Low Security Domain (Lsd), the Intermediate Security Domain (Msd) and the High Security Domain (Hsd). A security domain is a grouping of organizations that demonstrate the ability to provide resources of a given sensitivity level. Exchanges can be made between organizations of the same or different security domains. From these interactions, trust relationships can be deduced. These trust relationships are described by opinions expressing the level of trust between the organizations. An opinion is a subjective belief based on trust and allows one to express the trust value given to an organization [19] [20]. Figure 1 below represents a trust network overlay (TON) to our community resource sharing cloud like the proposal in [21]. The vertices or nodes of this network illustrate organizations and the edges represent interactions between them. A trust relationship between two entities is represented by an arrow whose source is the requester and the tip is the resource provider. The label of an edge expresses the trust opinion of the requester towards the supplier. An organization requesting a resource will be referred to as a partner or applicant.
● C the community cloud shown in Figure 1 below.
(1)
●
The set of sharing relations, such as:
(2)
![]()
Figure 1. A trust overlay network for a community cloud computing multi-domain.
● Confidence opinions are deduced from the different interactions between organizations in Figure 1. Thus,
the set of confidence opinions is expressed as follows:
(3.1)
● Based on this set, the opinion matrix is obtained
:
(3.2)
● The low, intermediate, and high security domains are represented by L, M, H respectively. The security domains are formulated below as subsets of community organizations:
(4.1)
● Based on the sets of security domains and the opinion matrix, the following safety domain matrix
is obtained:
(4.2)
The security domain relationships in this matrix allow for thresholds of required opinion values for vendor selection. These thresholds are defined by the following governance matrices:
n Top: the supplier governance matrix that expresses the minimum threshold of the supplier’s opinion of an applicant (overall reputation of an applicant).
,
and
represent respectively of the low, intermediate, and high security domain organizations.
(5.1)
n Tou : the partner governance matrix that expresses the minimum threshold of the applicant’s opinion of the supplier.
(5.2)
As an example, a share is allowed between a high security domain OpjH provider and a low security domain OuiL requester, if:
(5.3)
2.2. Workflow of SeComTrust
The SeComTrust operating process consists of first identifying and selecting the trusted provider for a given resource, then updating the trust values and transaction lists, and finally applying the promotion relegation protocol to update the security domains. The different selection phases are presented below:
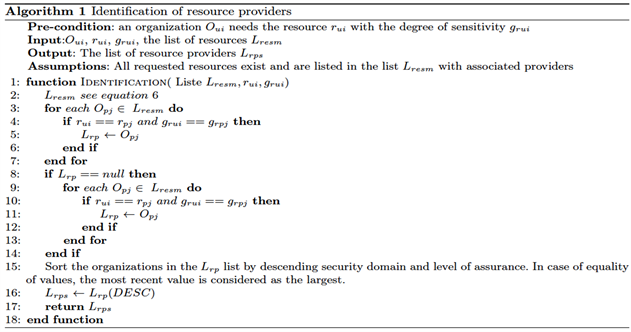
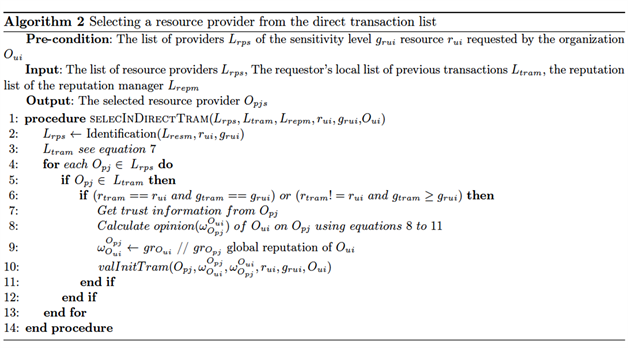
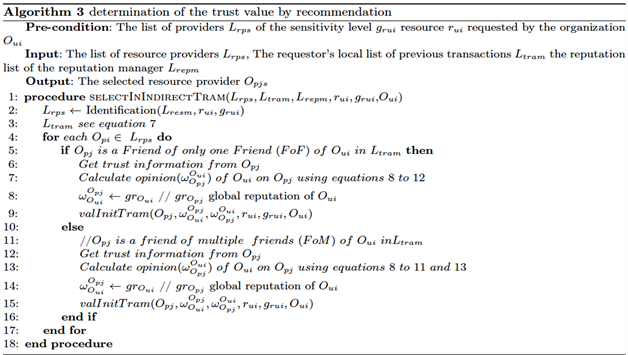
● Supplier selection from the supplier transaction list: This phase consists in first determining the suppliers of a requested resource. This process is described by (Algorithm 1 in the Appendices). Once the suppliers have been identified, the ideal supplier is selected from the supplier’s transaction list (TraM). This selection is done based on direct interaction (Algorithm 2 of the Appendices) at first. Then, if no supplier is found during the direct selection, the choice is made based on the recommendation of friendly suppliers. The types of indirect interactions are presented in the form of Friend of a Friend (FoF) or Friend of Multiple friends (FoM) relationships [8] described in Figure 2 below. The recommendation-based selection procedure is outlined in Algorithm 3 in the Appendices.
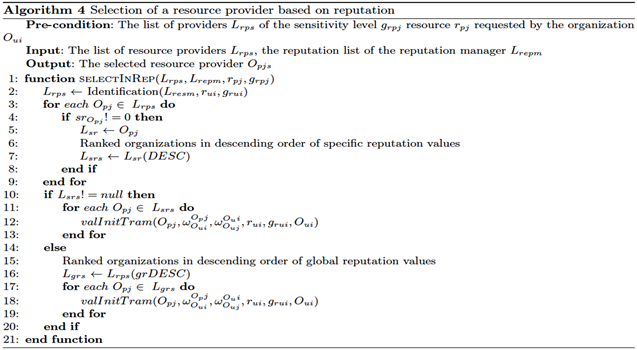
● Selection from the reputation lists: a recourse to the base of specific reputations is triggered if no supplier is found following the TraM searches. If the resource request is not satisfied, a final selection operation from the global reputation list is performed. Algorithm 4 in the Appendices describes the different phases of selection through the reputation lists.
2.3. Components of SeComTrust
The architecture of our model is shown in Figure 3 below. It consists of the following components: the Resource Manager (ResM), the Transaction Manager (TraM), the Trust Value Calculator (TruC), the Update Manager (UpdM), and the Reputation Value Manager (RepM). The different components are described in the sections below.
2.3.1. The Resource Manager (ResM)
The Resource Manager consists of a registry that contains a list of organizations in the community and the resources they offer. This list is expressed in the form below:
(6)
with Opj a resource provider organization rpj of sensitivity degree grpj.
2.3.2. The Transaction Manager (TraM)
The transaction manager is the local repository of an organization’s shares. It records and references all the shares made. As such, it is the priority consultation element in the trusted provider selection process. The information in the TraM is presented as follows:
(7)
with Opj the resource provider, rpj the resource provided, grpj the degree of sensitivity of the resource,
, the partner’s opinion value of trust,
the specific reputation of the provider and
the supplier’s security domain.
As in [22], the applicant’s overall trust opinion of the supplier is defined as the weighted sum of the supplier’s direct or recommended relationship and the supplier’s reputation:
(8)
with
specific reputation,
is the trust opinion based on direct or indirect interactions between the supplier and the partner. This trust opinion value is calculated using subjective logic (SL) and its four basic parameters namely: belief (b), disbelief (d), uncertainty (u) and base rate (α) [23] [24]. The trust opinion of the Oui organization towards the Opj organization for direct interaction is formulated as follows:
(9)
with
(10)
pt the number of previous positive trades between Oui and Opj, and nt the number of negative trades. The base rate α is paramount for new or inactive community members.
(11)
For indirect interactions, several operators are defined by the SL to determine the trust values [23]. For two organizations Oui and Opj without prior direct interactions (Equation (12) below). The trust derived between Oui and Opj is called transitive trust and will be computed as the opinion
using the discounting operator (
):
(12)
On the other hand, if there are two intermediate organizations Otz1 and Otz2, such that Opj has already interacted with Otz1 and Otz2, and there is no previous interaction between Oui and Opj (Equation (13) below). The confidence derived between Oui and Opj is parallel confidence and is represented as the opinion
. It is expressed below using SL and its consensus operator (
) [23]:
(13)
2.3.3. The Confidence Value Calculator (TruC)
The TruC executes the various algorithms for calculating and selecting confidence values.
2.3.4. The Update Manager (UpdM)
The role of the update manager is to update the trust information. The updated values are the specific reputation of the supplier, the global reputation of the partner and the supplier. In addition, the security domains are also updated through the promotion and relegation mechanism.
2.3.5. The Reputation Manager (RepM)
The RepM is the register of reputations of organizations in the community. We distinguish between two types of reputation: the reputation of a specific provider of a given resource and the overall reputation of an organization derived from its general behavior in the community. The information in this register is formulated as follows:
(14)
with Opj the resource provider, rpj the resource provided, grpj the degree of sensitivity of the resource provided,
the reputation of the organization as a provider of rpj of degree grpj,
the overall reputation value, and
the organization’s security domain.
2.4. Updating System Trust Values
2.4.1. Updating the Specific Reputation
The specific reputation of a supplier is updated after each transaction (Figure 4). To encourage the sharing of secure resources, a weight is assigned to each exchange according to the resource’s sensitivity level. The sensitivity level describes the degree of vulnerability of a resource. The grpj degrees of resource sensitivities are defined from the common computer resource vulnerability system CVSS v2.0 score range [18].
(15)
![]()
Figure 4. Transitive and parallel combinaison trust.
Like the contribution in [10], the specific reputation is expressed as follows:
(16)
Ilmin(j) the minimum value of assurance level of security domain j, Ilmax(j) the maximum value of assurance level j, Ilmax the maximum value of the assurance level, γi is the weight of an exchange.
The assurance level Il is the ability of an organization to provide a resource of a given sensitivity level. Organizations are grouped into security domains based on their assurance level.
(17)
2.4.2. Updating the Global Reputation
Global reputation is based on the overall results of an organization’s interactions as a provider within the community. It is formulated as follows:
(18)
with α the prime rate (α = 0.5), n the number of organization-specific reputations Opj,
the total number of exchanges for a given resource provider, STC the total number of shares within the community, and ρ the weight of the organization’s exchanges. After each update operation, the organization is promoted, relegated, or retained in a security domain.
3. Experiments and Results
3.1. Experimentation Environment
This article proposes a community cloud experimentation environment established in two phases. During the first phase, the 3C architecture is initialized. This involves generating dataset files describing organizations, provided resources, and resource requirements queries. Then, in the second phase, statistical data are produced through simulations of resource sharing between organizations. The information deduced from these experiments is used to evaluate the performance of our trust model. The experiments are conducted on a MacBook Pro (Retina, 15-inch, mid-2015), 2.2 GHz Intel Core i7 quad-core processor, 16 GB 1600 MHz DDR3 memory. Programming is performed in a Pycharm development environment (IDE) and the Python language Python 3.9. We distinguish two types of resource provider organizations. On the one hand, organizations provide resources in accordance with service level agreements (SLA) established between the actors involved in a transaction. These are referred to as good providers or G organizations. On the other hand, those providing unreliable resources. They are said to be malicious or M organizations. The number of organizations being an essential characteristic in the setting up of a perennial and prosperous community, the experiments are carried out on groups of organizations of the beach [80,250] members. The rate of malicious organizations is 20%. Rounds consisting of 500 resource requests are performed in each experimentation set. The experimentation parameters are summarized in Table 1 below.
The main metrics used to measure the performance of our model are:
(19)
● SRTG: Transaction success rate of G organizations
● RPOT: Rate of participation of organizations in transactions. This rate measures the number of different organizations involved in successful exchanges.
3.2. Selection Threshold and Parameter β Value
The selection confidence value of a vendor from the SeComTrust is calculated through Equation (8). To determine the value of β, representing the weight of the direct or recommended confidence value (DRT) in this equation, we examine the rate of participation of different organizations in transactions (RPOT) and the success rate of G providers (SRTG). RPOT measures the number of providers actively participating in transactions, limiting the possibility of selecting the same organizations repeatedly to increase the SRTG. The GTRS is an important performance indicator for trust models. It expresses the ability of the trust model to resist malicious attacks.
We perform simulations by setting the value of β between 0.3 and 0.7. The experimental results presented in Figure 5 show that the RPOT and STGR values are jointly higher (RPOT = 0.21, STGR = 0.98) when β is equal to 0.6 and the threshold is equal to 0.3. Ultimately, β is set to 0.6 and the selection threshold to 0.3 to provide a model with a high G-supplier transaction success rate and high organization participation.
![]()
Table 1. The experiment parameters.
3.3. Results and Discussion
To analyze the performance of our model, we compared our model to the TNA-SL model [9] [24] and to the Intertrust algorithm [8]. The simulations consisted in evaluating the scalability of the model by increasing the number of organizations in the community. The SeComTrust G-supplier success rate is compared to the other two models mentioned above. Scalability is one of the major characteristics of a Cloud environment [4]. In this paper, the resource sharing framework is modeled around sets of various sizes of organizations. The communities of organizations range from 80 to 250 members. For each group of organizations, 20% of malicious people are integrated. The results in Figure 6 below show the success rates of the three models (SeComTrust, InterTrust, TNA-SL). Each model is run in 15 rounds of 500 transaction requests per organization
![]()
Figure 6. Success rates for different numbers of resource providers of which 20% are malicious providers.
group. From these results, the success rate of SeComTrust is significantly higher than the success rate of the Intertrust and TNA-SL algorithms for all experienced user groups.
This is due to the selection confidence value which is obtained by the weighted sum of the direct or recommended confidence and the specific reputation value, unlike Intertrust and TNA-SL only based on SL parameters. Moreover, the proposed reputation value update mechanism and the selection of the provider from several lists (Ltram, Lrepm) according to a well-defined order justify the success rates of SeComTrust. In conclusion, we can state that our model allows the deployment of scalable 3Cs.
4. Conclusions
Trust management in cloud environments is a major challenge for adoption. However, trust management systems in cloud environments are primarily focused on public deployment types and focused on feedback between users and cloud service providers or between cloud service providers. These techniques do not focus on community cloud architectures. In view of this observation, we propose in this paper the SeComTrust, a model for managing, evaluating, and selecting trusted organizations in a Community Cloud environment based on a Zero Trust strategy. SeComTrust evaluates trusted organizations grouped in security domains by considering the direct interactions between them and their reputation within the community. In addition, this model is associated with a promotion and relegation mechanism to ensure that trust is monitored over time.
Through a series of experiments, we compared the results of our model to InterTrust and TNA-SL algorithms. We have shown that SeComTrust guarantees the scalability of a 3C by presenting success rates (SRTG) largely superior to those of InterTrust and TNA-SL. In future work, we will propose to incorporate resource quantity attributes and quality metrics into the exchange validation process and evaluate the attack resistance and execution time of SeComTrust.
Appendices